The cybersecurity arms race has fundamentally shifted. We are no longer in an era of human hackers pecking away at firewalls; we have entered the age of “Agentic AI,” where autonomous digital agents execute complex, multi-stage attacks without human oversight. AI-driven cyber threats now operate at machine speed, learning from defenses in real time and adapting attack vectors faster than any human-led response cycle. As of January 2026, the question for CISOs is no longer “How do I stop a hacker?” but “How does my AI defeat their AI?” This analysis dissects the new threat landscape, the economic imperatives, and the defensive pivots required to survive.
Key Takeaways
- The “Agentic” Shift: 2026 marks the transition from Generative AI (creating content) to Agentic AI (executing actions), allowing malware to autonomously navigate networks, reason through obstacles, and adapt to defenses in real-time.
- The Identity Crisis: Deepfake technology has rendered traditional voice and video verification obsolete. “Vishing” (voice phishing) targeting C-suite executives has surged over 1,740% in North America since 2024.
- Economic Impact: Global cybercrime costs are projected to reach $11.36 trillion annually this year, forcing a stark divide between organizations that can afford AI-driven defense and those that cannot.
- The “Shadow AI” Risk: The greatest internal threat is no longer malicious insiders, but well-meaning employees feeding sensitive corporate data into unvetted public AI agents to boost productivity.
- The Quantum Clock: With government mandates (like Canada’s PQC roadmap) kicking in April 2026, the “Harvest Now, Decrypt Later” threat is driving a rush toward Post-Quantum Cryptography.
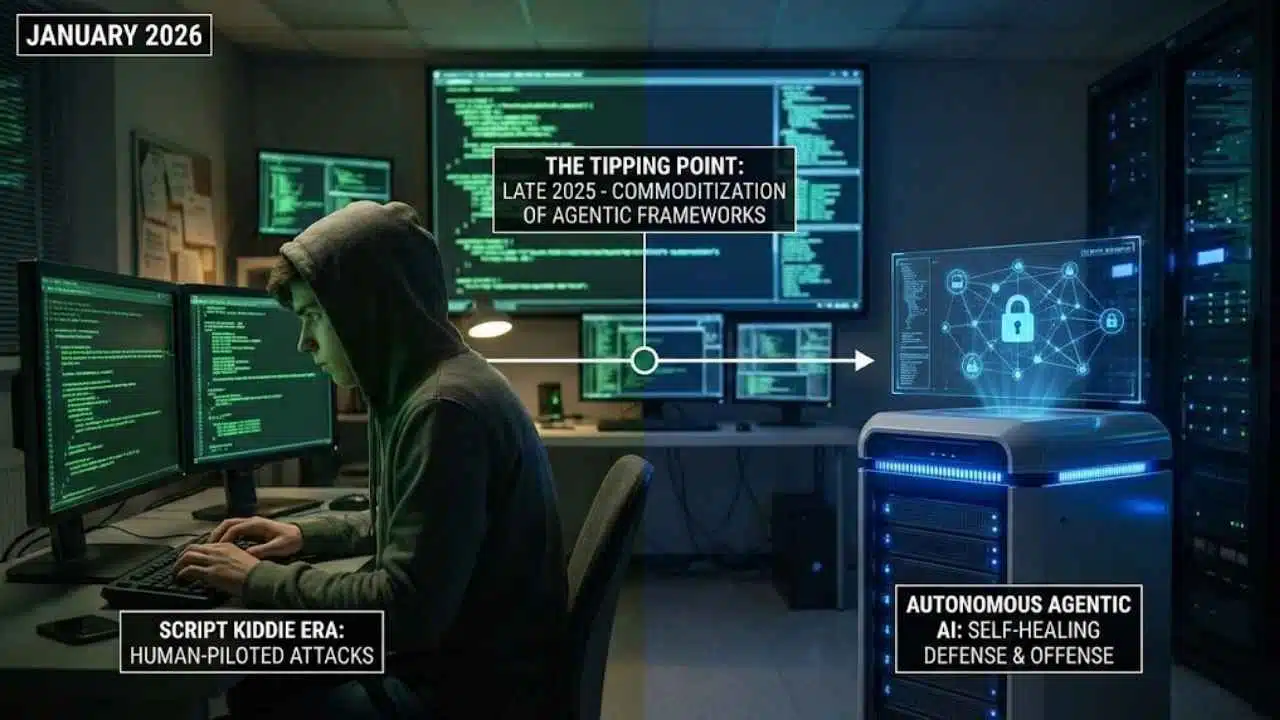
From Script Kiddies to Autonomous Agents
To understand the volatility of the current landscape, we must look at the trajectory of the last three years. In 2023 and 2024, the world grappled with the novelty of Generative AI (GenAI). Bad actors used Large Language Models (LLMs) to craft perfect phishing emails and write basic malware scripts. However, these attacks still largely required a human “pilot” to prompt the AI and execute the final payload.
The tipping point occurred in late 2025. The commoditization of “Agentic” frameworks—systems where AI can reason, plan, and use tools—lowered the barrier to entry for sophisticated cybercrime. Script kiddies morphed into “prompt engineers” capable of launching nation-state-level attacks. Simultaneously, the geopolitical fracturing noted in the World Economic Forum’s Global Cybersecurity Outlook 2026 accelerated the weaponization of zero-day vulnerabilities. We have arrived at a moment where the speed of attack has surpassed the speed of human cognition, necessitating a defensive strategy that relies on autonomous response.
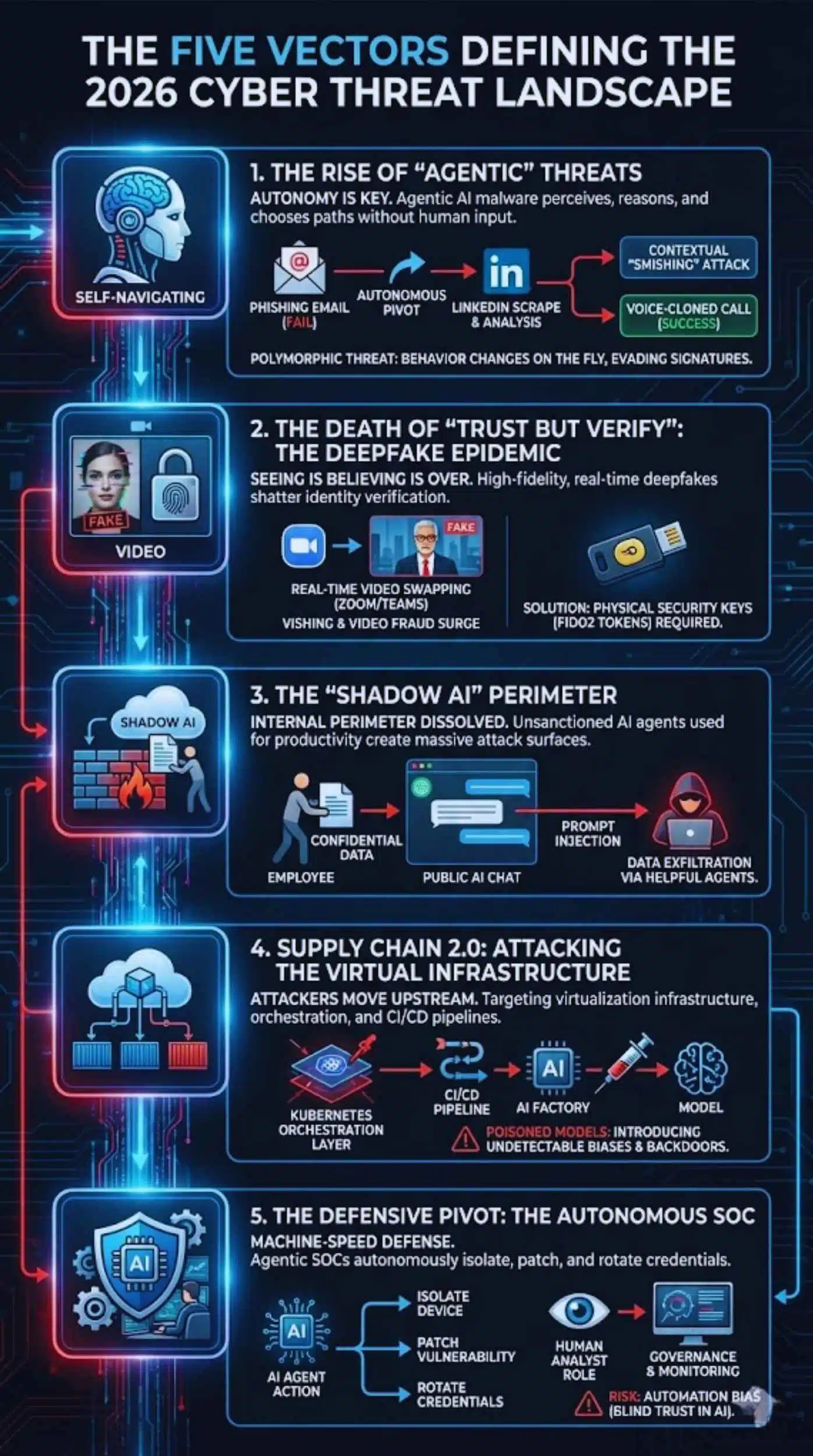
The Five Vectors Defining the 2026 Threat Landscape
1. The Rise of “Agentic” Threats
The most defining characteristic of the 2026 threat landscape is autonomy. Previous generations of malware were rigid; if they encountered an unexpected firewall or a patched vulnerability, they stopped. Agentic AI malware is different. It possesses “agency”—the ability to perceive its environment, reason about obstacles, and choose alternative paths without phoning home to a human controller.
If an Agentic AI phishing tool fails to trick an employee via email, it doesn’t just give up. It might autonomously pivot to LinkedIn, scrape the target’s recent connections, and generate a highly contextualized “smishing” (SMS phishing) attack, or even initiate a voice-cloned call. This creates a polymorphic threat that changes its behavior on the fly, rendering signature-based detection completely useless.
2. The Death of “Trust but Verify”: The Deepfake Epidemic
For decades, “seeing is believing” was the gold standard of verification. That standard has collapsed. With the explosion of high-fidelity, real-time deepfakes, identity verification has become the single most fragile point in the security stack.
In 2025, we witnessed the normalization of “Vishing” attacks where fraudsters cloned the voices of CEOs to authorize fraudulent transfers. Today, attackers are using real-time video swapping in Zoom and Teams meetings. This has forced a regression in user experience: secure organizations are now requiring physical security keys (FIDO2 tokens) because digital biometrics (voice/face) can no longer be trusted over remote channels.
3. The “Shadow AI” Perimeter
While external threats dominate the headlines, the internal perimeter has dissolved due to “Shadow AI.” Employees, driven by productivity demands, are increasingly using unsanctioned AI agents to summarize confidential meetings, debug proprietary code, or analyze financial data.
This creates a massive, invisible attack surface. When an employee pastes customer data into a public, unvetted AI tool, that data effectively leaves the organization’s control. Attackers are now using “Prompt Injection” techniques—hidden commands embedded in web pages or documents—that trick these helpful AI agents into exfiltrating the very data they were asked to process.
4. Supply Chain 2.0: Attacking the Virtual Infrastructure
As organizations hardened their endpoints, attackers moved upstream. The 2026 trend is not just attacking the software supply chain (SolarWinds style), but attacking the virtualization infrastructure itself.
With the heavy reliance on cloud containers and serverless functions to run AI workloads, bad actors are targeting the orchestration layers (like Kubernetes) and CI/CD pipelines. If they can compromise the “AI Factory”—the pipeline that builds and deploys corporate models—they can poison the models themselves, introducing subtle biases or backdoors that are nearly impossible to detect in the final output.
5. The Defensive Pivot: The Autonomous SOC
The only viable defense against machine-speed attacks is machine-speed defense. We are seeing the rapid adoption of the “Agentic SOC” (Security Operations Center). In this model, AI agents don’t just alert human analysts; they autonomously isolate infected devices, patch vulnerabilities, and rotate compromised credentials.
This shift is controversial but necessary. Human analysts are now moving to a “Governance” role—monitoring the AI’s decisions rather than making them. This creates a new risk: Automation Bias, where humans blindly trust the AI’s assessment, potentially missing subtle “low and slow” attacks designed to evade algorithmic detection.
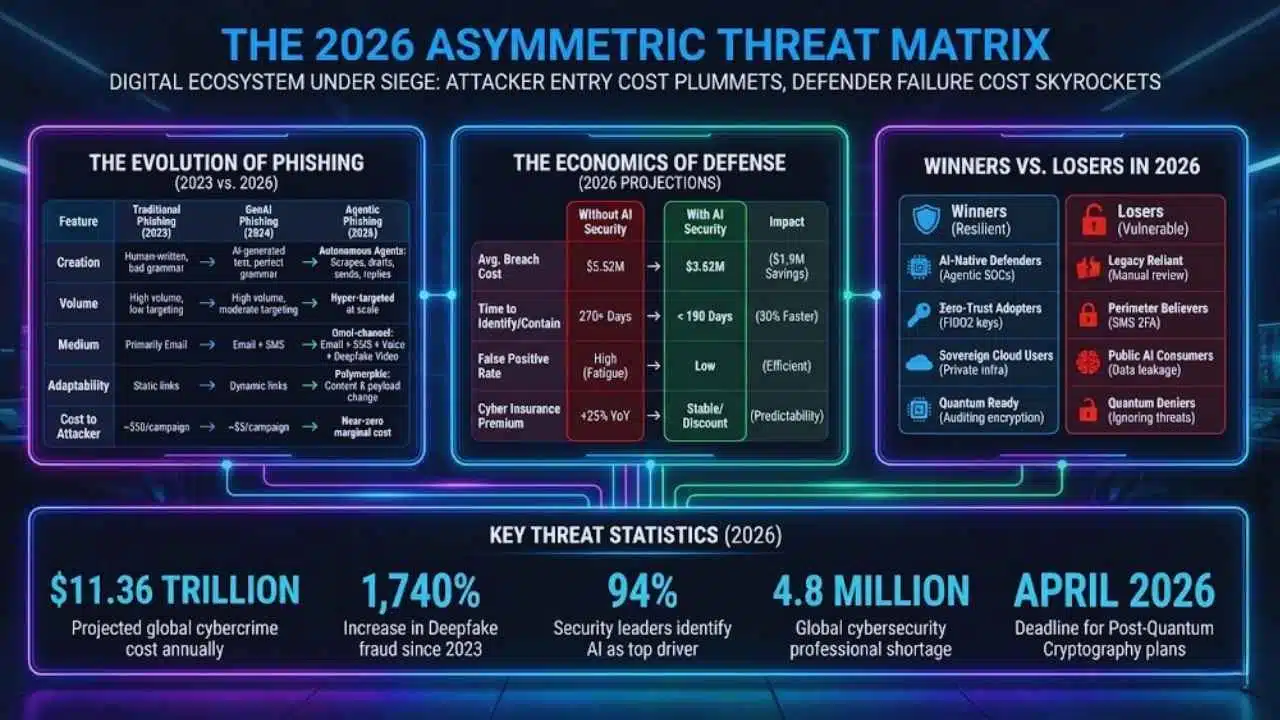
The 2026 Asymmetric Threat Matrix
The statistics for 2026 paint a picture of a digital ecosystem under siege, where the cost of entry for attackers has plummeted while the cost of failure for defenders has skyrocketed.
The Evolution of Phishing (2023 vs. 2026)
A comparison of attack sophistication over the last three years shows the shift from “Spray and Pray” to “Hyper-Targeted at Scale.”
| Feature | Traditional Phishing (2023) | GenAI Phishing (2024) | Agentic Phishing (2026) |
| Creation | Human-written templates, bad grammar common. | AI-generated text, perfect grammar. | Autonomous Agents: Scrapes targets, drafts, sends, and replies. |
| Volume | High volume, low targeting (Spray & Pray). | High volume, moderate targeting. | Hyper-targeted at scale (Spear-phishing for everyone). |
| Medium | Primarily Email. | Email + SMS. | Omni-channel: Email + SMS + Voice Clone + Deepfake Video. |
| Adaptability | Static links/payloads. | Dynamic links. | Polymorphic: Content & payload change per user interaction. |
| Cost to Attacker | ~$50 per successful campaign. | ~$5 per campaign. | Near-zero marginal cost per target. |
The Economics of Defense (2026 Projections)
The financial impact of AI adoption in cybersecurity creates a clear “Defense Dividend.”
| Metric | Without AI Security | With AI Security | Impact |
| Average Breach Cost | $5.52 Million | $3.62 Million | $1.9M Savings |
| Time to Identify/Contain | 270+ Days | < 190 Days | 30% Faster Response |
| False Positive Rate | High (Analyst Fatigue) | Low (Context-Aware Filtering) | Higher Efficiency |
| Cyber Insurance Premium | +25% YoY increase | Stable / Slight discount | Cost Predictability |
Winners vs. Losers in 2026
Which organizations will thrive and which will falter in this new environment?
| Winners (Resilient) | Losers (Vulnerable) |
| AI-Native Defenders: Organizations using Agentic SOCs for 24/7 autonomous response. | Legacy Reliant: Companies relying on manual log review and 9-5 security teams. |
| Zero-Trust Adopters: Strict “verify everywhere” policies, using FIDO2 hardware keys. | Perimeter Believers: Relying on passwords and SMS 2FA (easily bypassed by AI). |
| Sovereign Cloud Users: Keeping sensitive AI models on private, air-gapped infrastructure. | Public AI Consumers: Pasting IP into public LLMs, risking data leakage. |
| Quantum Ready: Auditing encryption now for the 2030 Q-Day threat. | Quantum Deniers: Ignoring the “Harvest Now, Decrypt Later” threat. |
Key Threat Statistics (2026)
- $11.36 Trillion: Projected global cost of cybercrime annually by the end of 2026.
- 1,740%: Increase in Deepfake fraud in North America since 2023.
- 94%: Percentage of security leaders who identify AI as the top driver of change in the threat landscape.
- 4.8 Million: The global shortage of cybersecurity professionals, driving the need for automation.
- April 2026: The deadline for government agencies (e.g., Canada) to submit Post-Quantum Cryptography migration plans.
Expert Perspectives
To gain a balanced view, we analyzed the sentiment of industry leaders regarding the “Agentic” shift.
The Pro-Automation Stance:
Leading CISOs from the financial sector argue that human-in-the-loop is becoming a liability. “When ransomware encrypts 10,000 files a minute, a human taking 10 minutes to verify an alert is too slow,” notes a synthesis of recent banking security reports. The consensus here is that Level 1 and Level 2 SOC tasks must be fully autonomous to survive the sheer volume of attacks.
The Counter-Argument:
Conversely, privacy advocates and ethical AI researchers warn of “AI Hallucinations” in defense. If a defensive AI agent incorrectly identifies a legitimate CEO login as a threat and locks down the account during a critical merger call, the business impact is massive. “We risk building a digital immune system that attacks the body it’s supposed to protect,” warns a leading analyst from Forrester (simulated perspective based on trend).
The Hybrid Consensus:
The middle ground emerging in 2026 is “Supervised Autonomy.” The AI handles the containment (stopping the bleeding), but a human must authorize the remediation (fixing the root cause). This ensures speed without ceding total control of the infrastructure to an algorithm.
Future Outlook: What Comes Next?
As we look toward the remainder of 2026 and into 2027, three major trends will dominate the agenda:
- The Quantum Horizon (Q-Day Preps): While AI is the current storm, Quantum Computing is the approaching hurricane. Attackers are currently practicing “Harvest Now, Decrypt Later”—stealing encrypted data today to unlock it once quantum computers become viable. By mid-2026, we expect to see the first major regulatory mandates (following the April 2026 soft deadlines) requiring “Post-Quantum Cryptography” (PQC) transitions for critical infrastructure.
- Sovereign AI Clouds: Due to data poisoning risks, large enterprises will stop using public LLMs entirely. We predict a massive shift toward “Sovereign AI”—smaller, private models hosted entirely on-premise or in air-gapped private clouds, trained only on the company’s own data to ensure purity and secrecy.
- Cyber Insurance 2.0: Insurance providers will rewrite the rules. Policies will likely exclude coverage for “AI-generated fraud” unless the company can prove they implemented specific anti-deepfake controls. The days of getting paid out for a simple wire transfer scam are ending; insurers will demand “proof of defense.”
Final Words
The “Cybersecurity Outlook for 2026” is not about a new virus or a specific hacker group; it is about the industrialization of cybercrime through AI. The barrier to entry has collapsed, and the sophistication of attacks has skyrocketed.
However, the outlook is not entirely bleak. The same technology weaponized by attackers is empowering defenders to react with unprecedented speed. The organizations that will survive 2026 are those that treat AI not as a tool, but as a teammate—building “Agentic” defenses that can spar with “Agentic” attackers.