Many crypto users worry about a single private key. A seed phrase leak or a hack can drain a crypto wallet in seconds. One wrong click can empty a hardware wallet or smart contract wallet.
You need a stronger guard in decentralized finance.
Multi-signature wallets require more than one signature to send digital assets. They cut theft risk by splitting approvals among people, BitGo services, or smart contract rules. This guide shows how multi-sig works, how it boosts blockchain security, and how to set one up.
Want safer coins?
Key Takeaways
- Multi-sig wallets need multiple keys to sign a transaction, such as 2-of-3 or 3-of-5 rules.
- BitGo launched in 2013 and processed billions in crypto trades for Binance, Crypto.com, OKX, and Huobi.
- Gnosis Safe, Coinbase Wallet, and Trust Wallet offer on-chain multi-sig with smart contract rules.
- Industry use of multi-sig grows 25% each year as firms and DAOs block theft and fraud.
- Users pair multi-sig with cold wallets, antivirus apps, and 2FA to stop hackers.
What Are Multi-Signature Wallets?
Multi-signature wallets stand like a fortress for digital assets. They need two of three keys to sign a transaction. This spreads private key control and kills single points of failure.
Institutions that hold vast crypto assets use them. A key holder might keep a seed phrase in a cold wallet, another uses a hardware wallet, one logs in via a browser extension wallet.
They work with smart contracts on blockchain technology. They stop hackers, fraudsters, thieves from draining an exchange, like a bouncer at a club. Decentralized autonomous organizations lean on them for group fund management.
A business can ask for three approvals from five people to move funds, cutting risk. This design boosts wallet security with multi-factor authentication.
How Multi-Signature Wallets Work
Imagine a digital vault that opens only when three people turn their keys at once. TRON crypto wallets layer in three permission tiers. Owner permissions sit at the top. They run all contracts and operations without limits.
Witness addresses tie into Super Representatives for elections and voting. Active accounts handle daily transfers and smart contract calls. Owners assign address rights and set permission weights, so no one can move digital assets alone.
Cryptographic signatures bind each public key to a real user.
Smart contract wallets use multi-party computation to check each signature. A threshold, like two out of three, ensures safety. The wallet holds a private key slice, not the whole secret.
Each signer uses hardware wallets or a cold wallet to sign. Hackers get blocked, even if one password or seed phrase falls. DAOs and high-value trades lean on this for blockchain security.
DeFi platforms or decentralized applications tap this power. Blockchains pause crypto transfers until enough users approve. Fraud drops and unauthorized access fails.
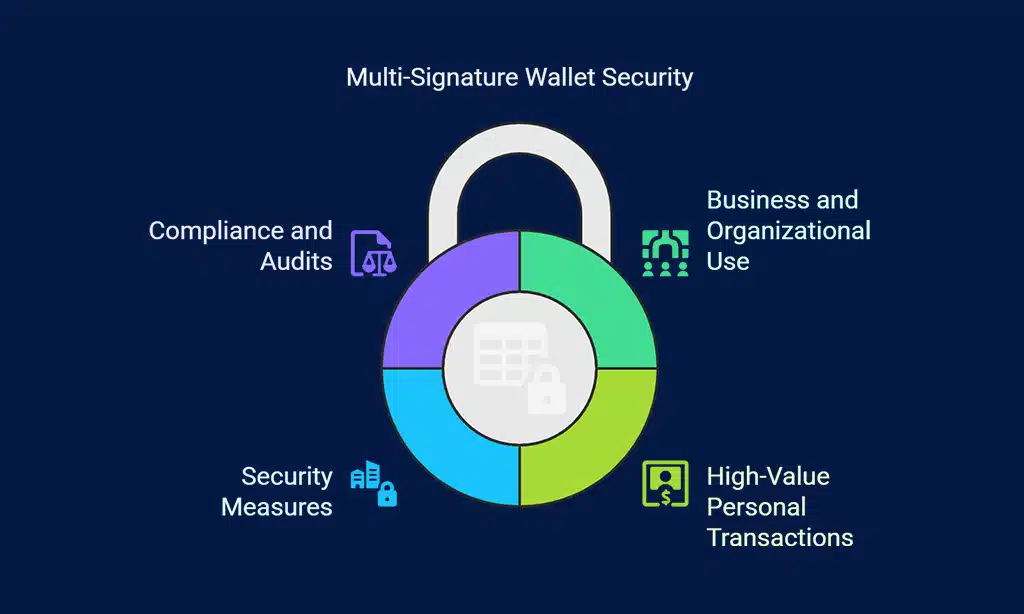
Key Features of Multi-Signature Wallets
Multi-signature wallets pair shared key management with a strong firewall shield to stop single points of failure and block hackers—read on to learn more.
M-of-N Multisig Wallets
This multi-signature wallet setup splits control over private keys across a team of signers. You can pick 2-of-3 or 3-of-5 rules to guard digital assets and cryptocurrencies. The plan cuts theft, hacking and misuse risks.
An institution can hold large crypto holdings in a non-custodial wallet with more safety. The system runs on blockchain technology and uses an on-chain vault.
Many tools like Gnosis Safe and a secure vault app let you use this design. Each signer owns a private key and adds an on-chain signature. The process calls for distinct participants to green-light a move.
It differs from MPC in that each party signs independently. Users gain stronger wallet security and avoid single points of failure.
N-of-N Multisig Wallets
An N-of-N smart-contract wallet makes every signer vital. Each signer holds a private key. All keys must sign to move digital assets. Hackers can grant themselves Owner or Active rights in a flawed multisignature process.
Many daos use that setup for strong blockchain security.
Teams tap MetaMask and Gnosis Safe to share approvals. Designers set permission weights and thresholds for each role. That model cuts fraud and hacking odds. You can pair it with a cold wallet or a hardware dongle.
Antivirus software and a passcode vault boost protection.
Security Benefits of Multi-Signature Wallets
A multi-signature wallet locks your coins behind multiple keys, splits them into seed phrases, uses a firewall to guard your stash, and slams hackers against a brick wall, so keep reading to see how this fortress protects your funds.
Eliminating Single Points of Failure
Multi-signature wallets lock down digital assets with multiple private keys, like having three keys for one door. This scheme stops thieves from grabbing funds if one key leaks. DAOs and businesses trust 2-of-3 setups, needing two approvals to send funds.
Cold wallet, password manager, firewalls, and antivirus software habits still matter. Smart contract wallets tie approvals to on-chain rules.
This approach cuts out single points of failure by spreading control. A hacker must hit two or more keys to move coins. Non-custodial wallet users avoid relying on one seed phrase alone.
Blockchain security grows stronger, lowering risk of exploits or phishing sites, or hacker traps. Owners gain peace of mind, even if one key goes missing.
Enhanced Protection Against Hacking
Wallets that need three of five private keys stop hackers after one key leaks. A thief with a single seed phrase cannot grant full Owner or Active permissions. Hackers lose the chance to slip in new permissions and strip user control.
This setup defends against phishing attacks and cash drains. It adds strong fraud prevention to every decentralized finance transfer.
SlowMist runs security audits and tracks suspicious flows on blockchain networks. It spots threats in real time and blocks cyber attacks before they spread. Firms such as Binance, OKX, Huobi, Crypto.com, EOS and 1inch trust its reports.
You boost blockchain security more by adding a cold wallet, antivirus software and two-factor authentication (2fa). This mix cuts risk in half for high-value coin transfers.
Preventing Unauthorized Transactions
Multiple owners sign each transfer of digital assets. Hackers need two private keys to move assets. They cannot use a single key to sign transactions. This step removes single points of failure.
It boosts blockchain security and fraud prevention.
DAOs, cryptocurrency exchanges, and businesses adopt this model. Gnosis Safe uses programmable smart contract wallets on Ethereum. Teams add multi-factor authentication and access controls.
They enforce internal control and meet compliance rules. Users store funds in a non-custodial cold wallet.
Use Cases for Multi-Signature Wallets
Leaders of DAOs store their digital assets in smart contract wallets, and each transfer needs several hands on deck. They stash keys in an offline vault, so a lone hacker can’t walk away with the loot.
Business and Organizational Use
Large firms hold huge digital assets on blockchains. Exchanges, investment firms, decentralized autonomous organizations, custodial services, and corporate treasuries use multi-signature wallets to lock private keys behind multiple signers.
Setup uses non-custodial and cold wallets with smart contract features. Stakeholders split the keys into M-of-N formats. This adds blockchain security and meets tough compliance rules.
Teams cut single points of failure and stop password leaks.
Adoption of multi-signature wallets grows at 25% every year. Approval stations run antivirus software to guard keys and meet audit needs. DAOs pick 2-of-3 schemes for proposal votes.
Investment firms choose 3-of-5 rules for high-value transfers. Coinbase Wallet and Trust Wallet support these setups. Extra layers block unauthorized crypto transactions and prevent fraud.
High-Value Personal Transactions
Major transfers of digital assets might feel like walking a tightrope. A multi-sig setup asks for more than one private key. You store partial keys offline in a cold wallet. This design cuts risk of hacking or theft in half.
Clients apply it to big-ticket estate planning or rare NFT trades.
The market for multi-signature solutions grows at 25 percent each year. Coinbase Wallet and Trust Wallet support M-of-N signoffs for three keys in crypto transactions. Non-custodial multisignature wallets boost internal control and support compliance audits.
Lawyers, family, and exchanges each hold one part of a private key. They sleep well knowing no hacker grabs all secret keys at once.
Best Practices for Setting Up a Secure Multi-Signature Wallet
Lock your keys inside a hardware wallet and split them across trusted peers, that trick builds a stronghold around your crypto. Pair this with a solid antivirus program on your workstations, so cyber-thieves bounce off your defenses like rubber balls.
Choosing Reliable Wallet Providers
BitGo launched in 2013 to protect digital assets with multi-signature wallets. It stores private keys across multiple custodians. Firms like Binance, Crypto.com, Huobi and OKX use its services.
A swap aggregator and smart-contract network also rely on its cold wallet tech. It has processed billions in cryptocurrency transactions for thousands of institutions. Visit www.bitgo.com for details.
Choose a non-custodial wallet that offers multi-factor authentication and regular audits. Check code repositories and verify firmware versions before a transfer. Install antivirus software on each device.
Keep backup phrases in separate, secure locations. Split seed words across two or more safes.
Managing Recovery Options Effectively
Store private keys in at least three spots. Place a paper backup in a safe. Keep a copy on an encrypted drive. Use a cold wallet and a password manager. Spread backups across home, office, and a safe deposit box.
This step boosts wallet security and helps with fraud prevention.
Test recovery steps before you need them. Open the non-custodial wallet and run the restore flow. Check that the public key ties back to your account. Add multi-factor authentication and connect a security key.
Invite a member of your decentralized autonomous organization to watch. That drill proves you can recover digital currencies under stress. It also adds internal control and backs regulatory compliance.
Takeaways
Multi-sig wallets guard your digital assets with ease. They split control across private keys and signers. Most self-custody wallets use them. Some programmable wallets even meet ERC-4337 rules.
Stolen keys no longer mean empty vaults.
FAQs
1. What is a multi-signature wallet?
A multi-signature wallet is a crypto wallet that needs more than one private key to move cryptocurrency coins. It uses public keys like a group lock and key system.
2. How does it boost blockchain security?
It stops fraud by needing several approvals, it locks out cybercriminals, and it works with blockchain technology. Think of it as a digital vault with extra doors.
3. Can I store digital assets in one?
Yes, you can hold all your digital assets in it. It works with smart contract wallets or programmable wallets, and even for initial coin offerings.
4. How do multi-signature wallets fit into DeFi and DAOs?
In decentralized finance, they split control so no one person moves funds alone. In decentralized autonomous organizations (daos), they let groups vote on payments, like team treasure chests.
5. How do I set one up?
Pick a non-custodial wallet, like an offline vault, add public keys, and turn on multi-factor authentication with strong passwords. It feels like building a digital safe.
6. Any risks or tips?
Watch for vulnerabilities by running AVG or Kaspersky scans, change passwords often, test your Coinbase wallet or Trust purse, and check authenticity on Twitter, Telegram, or Instagram.