The digital age has brought immense advancements in website security, from encryption protocols to firewalls and multi-factor authentication.
However, a new technological revolution—quantum computing—threatens to upend traditional cybersecurity defenses. How quantum computing could change website security is a critical question that web developers, security experts, and businesses must address as we inch closer to an era of unprecedented computational power.
This article explores how quantum computing could change website security, the potential risks it poses, and what measures organizations can take to prepare for the post-quantum world.
Understanding Quantum Computing
Quantum computing is an advanced form of computation that leverages the principles of quantum mechanics to process information at speeds unimaginable with classical computers. Unlike classical bits that exist as either 0s or 1s, quantum bits (qubits) can exist in multiple states simultaneously, thanks to superposition and entanglement.
Key Features of Quantum Computing:
- Superposition: Qubits can be in multiple states at once, enabling parallel computations. This allows quantum computers to process a vast number of possibilities at the same time, making them exponentially more powerful for certain computations than classical computers.
- Entanglement: Qubits can be linked across distances, allowing them to influence each other instantaneously. This unique property enables ultra-secure communication, as any interference with entangled qubits can be instantly detected, making it nearly impossible for hackers to eavesdrop.
- Quantum Speedup: Quantum algorithms can solve complex problems exponentially faster than classical algorithms. This speedup is particularly important for cryptographic challenges, optimization problems, and large-scale simulations that would take classical computers centuries to compute.
Potential of Quantum Computing:
- Solve optimization problems faster: Quantum computing can tackle complex optimization issues in logistics, finance, and AI.
- Break traditional encryption methods: Algorithms like RSA and ECC could become obsolete in the face of quantum attacks.
- Improve AI and machine learning models: Quantum computing can enhance AI capabilities by speeding up data processing and training models more efficiently.
- Enhance cryptographic security (if harnessed correctly): Quantum-safe encryption techniques could make digital communications more secure than ever before.
The Impact of Quantum Computing on Website Security
As quantum computing advances, its impact on website security cannot be ignored. Traditional cryptographic defenses, which have long safeguarded digital platforms, are now at risk of becoming obsolete.
How quantum computing could change website security is a growing concern, demanding urgent attention from businesses and cybersecurity professionals. The following sections explore the ways in which quantum computing is set to reshape the cybersecurity landscape and what measures can be taken to mitigate its risks.
1. Breaking Traditional Encryption Methods
One of the most concerning aspects of how quantum computing could change website security is its ability to break widely used encryption algorithms. Most website security mechanisms rely on:
- RSA Encryption (Rivest-Shamir-Adleman), which depends on the difficulty of factoring large prime numbers.
- Elliptic Curve Cryptography (ECC), which provides security by relying on the complexity of solving discrete logarithm problems over elliptic curves.
- Diffie-Hellman Key Exchange, which enables secure key exchanges based on the difficulty of solving discrete logarithms.
Quantum computers running Shor’s Algorithm could factor large prime numbers in mere seconds, rendering RSA and ECC encryption obsolete. This means that security protocols protecting vast amounts of online data, including government communications, corporate secrets, and personal financial transactions, could be compromised almost instantaneously.
Traditional cryptographic approaches rely on mathematical problems that are computationally infeasible for classical computers, but quantum computers could make these problems trivial to solve.
Implications:
- SSL/TLS certificates used in HTTPS connections could become vulnerable, making websites and online services susceptible to man-in-the-middle (MITM) attacks where attackers decrypt sensitive data in transit.
- Secure email communications could be intercepted and decrypted, allowing adversaries to access confidential business and personal communications.
- Online banking and e-commerce transactions could be at risk, exposing user credentials, credit card information, and other sensitive financial data.
- Data encrypted for long-term confidentiality (such as classified government documents or sensitive business records) could be decrypted retroactively once a sufficiently powerful quantum computer is developed, potentially compromising years of stored information.
- Blockchain security could be undermined, as quantum computers could reverse-engineer public-private key pairs, allowing unauthorized access to cryptocurrency wallets and smart contracts.
Given these risks, businesses and cybersecurity professionals must urgently explore quantum-resistant cryptographic techniques to safeguard digital assets and prevent a future where encryption as we know it is no longer effective.
2. Quantum-Resistant Cryptography
To counter the threats posed by quantum computing, researchers are developing post-quantum cryptography (PQC) algorithms that can withstand quantum attacks.
Notable Quantum-Resistant Algorithms:
| Algorithm Name | Security Feature |
| Lattice-Based Crypto | Uses complex mathematical structures for security |
| Hash-Based Crypto | Relies on cryptographic hash functions |
| Code-Based Crypto | Uses error-correcting codes to ensure security |
| Multivariate Crypto | Involves solving polynomial equations |
The National Institute of Standards and Technology (NIST) is actively working on standardizing these quantum-resistant encryption methods.
3. Impact on Secure Communications
How quantum computing could change website security also extends to secure communication channels, such as:
- VPNs (Virtual Private Networks)
- SSH (Secure Shell) connections
- End-to-End Encrypted Messaging Services
Organizations must transition to quantum-safe key exchange mechanisms like Quantum Key Distribution (QKD) to maintain secure communication channels in the future.
4. Digital Identity and Authentication Threats
Quantum computing could pose risks to authentication mechanisms such as:
- Password-based authentication: Cracked in seconds by quantum brute-force attacks
- Two-Factor Authentication (2FA): Potentially compromised if cryptographic codes are broken
- Biometric Security: Vulnerable to AI-powered deep learning models enhanced by quantum computing
Quantum-Secure Authentication Solutions:
- Quantum-Resistant Digital Signatures: Based on hash functions or lattice-based cryptography
- Quantum-Safe Blockchain: New cryptographic techniques to secure decentralized transactions
- Quantum-Powered Identity Verification: Using quantum randomness for truly unpredictable authentication keys
5. Blockchain and Cryptocurrency Vulnerabilities
Blockchain technology, which underpins cryptocurrencies and decentralized applications, relies heavily on cryptographic hash functions and digital signatures.
Risks:
- Quantum computers could break Elliptic Curve Digital Signature Algorithm (ECDSA), exposing cryptocurrency wallets.
- Public-private key pairs in blockchain networks could become insecure.
- Smart contracts might require new cryptographic safeguards.
Solution: Developers must integrate quantum-resistant cryptographic methods like Lamport signatures or hash-based cryptography to secure blockchain networks in the quantum era.
Preparing for the Post-Quantum Security Era
As the cybersecurity landscape evolves, organizations must proactively prepare for the threats and opportunities posed by quantum computing. How quantum computing could change website security is no longer a theoretical concern but an imminent challenge requiring swift action.
Businesses that fail to adapt may find their encryption and authentication systems obsolete, leaving them vulnerable to cyber threats. The following strategies outline essential steps to future-proof website security in the post-quantum era.
1. Transitioning to Post-Quantum Cryptography
With quantum computing rapidly evolving, traditional encryption methods face an unprecedented threat. The transition to quantum-resistant cryptographic techniques is no longer an option but a necessity for organizations seeking to safeguard their digital assets.
How quantum computing could change website security is a question that demands immediate action, as businesses must future-proof their cybersecurity infrastructure before quantum computers reach their full potential.
Organizations must begin adopting Quantum-Safe Cryptographic Standards (QSCS) by:
- Replacing RSA and ECC with quantum-resistant encryption
- Upgrading PKI (Public Key Infrastructure) for quantum resilience
- Implementing Hybrid Cryptographic Solutions (Classical + Post-Quantum)
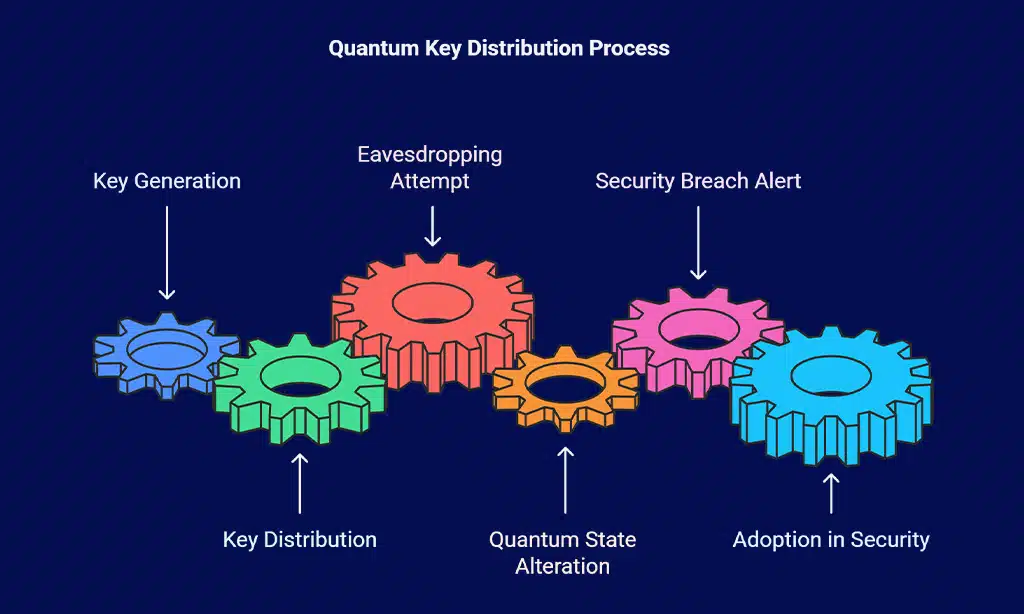
2. Quantum Key Distribution (QKD) Implementation
QKD leverages quantum mechanics to distribute encryption keys securely, making it impossible for attackers to intercept communications without detection. Unlike traditional cryptographic key exchange methods, QKD ensures that any eavesdropping attempt by a malicious actor alters the quantum state of the key, alerting both parties to a security breach.
This method provides an unprecedented level of security, as it eliminates the risk of undetected key interception, which is a major vulnerability in classical encryption protocols. As quantum computing progresses, the adoption of QKD will become a crucial component in safeguarding online communications, financial transactions, and sensitive government data.
3. Regular Security Audits and Risk Assessments
Businesses must:
- Conduct Quantum Readiness Assessments to evaluate their current security frameworks and identify potential vulnerabilities that quantum computing could exploit.
- Identify vulnerabilities in their existing cryptographic systems, including outdated encryption protocols, weak authentication mechanisms, and insecure communication channels.
- Develop a Quantum Transition Strategy that includes a phased approach to adopting post-quantum cryptographic algorithms, employee training programs, and continuous monitoring to ensure ongoing security resilience against emerging quantum threats.
4. Collaboration with Cybersecurity Experts
Organizations should work closely with:
- Cybersecurity firms specializing in post-quantum encryption, as they provide expertise in implementing quantum-resistant cryptographic solutions and staying ahead of emerging threats.
- Government agencies (like NIST) monitoring quantum security threats, which are actively developing post-quantum cryptographic standards and guidelines to ensure global cybersecurity resilience.
- Academic institutions conducting research on quantum-safe security measures, as they contribute to the advancement of encryption techniques, security protocols, and innovative quantum-resistant methodologies that businesses can adopt to safeguard their digital assets.
5. Raising Awareness and Training IT Teams
Companies should:
- Educate developers on quantum-safe coding practices, including implementing quantum-resistant algorithms, hybrid cryptographic solutions, and secure key management strategies.
- Train IT professionals in post-quantum cryptographic techniques, ensuring they understand the emerging threats posed by quantum computing and how to deploy countermeasures effectively.
- Update cybersecurity policies to align with quantum security standards, integrating post-quantum encryption, secure communication protocols, and continuous monitoring frameworks to protect against evolving quantum threats.
Wrap Up
Quantum computing holds immense potential, but it also presents significant challenges to website security. How quantum computing could change website security is a pressing concern that demands proactive measures from businesses, governments, and cybersecurity experts.