Why is this significant right now? In a move redefining the boundaries between national security and corporate intellectual property, India has reportedly drafted regulations requiring smartphone manufacturers like Apple, Samsung, and Xiaomi to share proprietary source code with government labs.
While New Delhi frames this as a necessary shield against cyber espionage for its 750 million users, the industry views it as an unprecedented “red line” that threatens the core trade secrets of the global tech ecosystem. This standoff marks a critical pivot in India’s digital governance strategy—moving from incentivizing hardware manufacturing to aggressively policing the software that runs it.
Key Takeaways
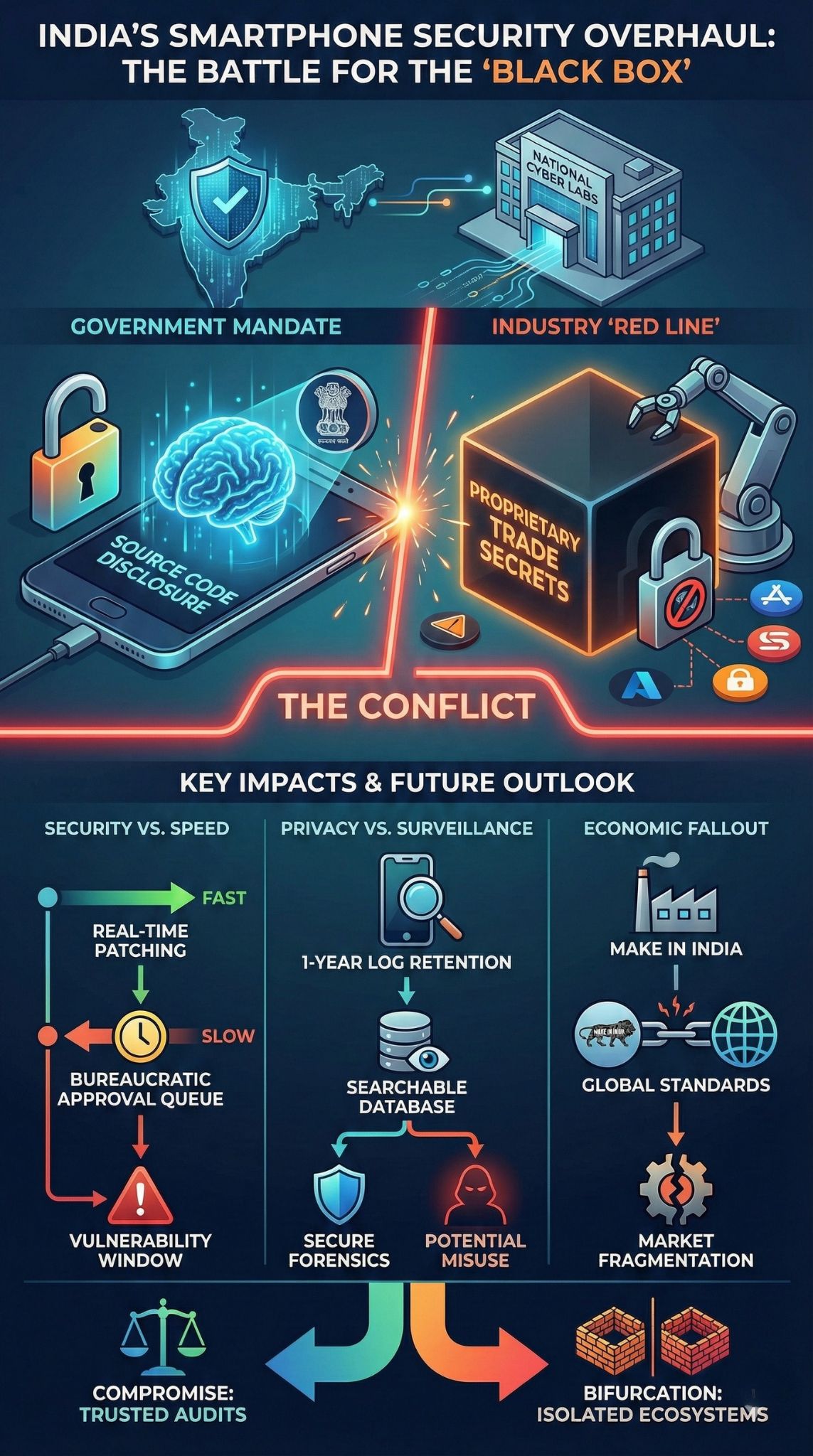
- The Core Conflict: The proposed “Indian Telecom Security Assurance Requirements” (ITSAR) include sharing source code, mandatory removal of pre-installed apps, and government vetting of major OS updates.
- Industry “Red Line”: Global giants argue that handing over source code has no global precedent, risks IP theft, and compromises the security architecture of closed systems like iOS.
- Government Stance: New Delhi denies a finalized mandate, framing the draft as “routine consultation,” yet firmly pushes for deeper visibility into the “black box” of foreign devices to curb data breaches and espionage.
- Operational Risk: Requirements like retaining user logs for one year and government pre-approval for security patches could degrade device performance and leave users vulnerable to zero-day exploits during bureaucratic delays.
- Economic Tension: The strict compliance costs threaten to dampen the “Make in India” manufacturing boom just as India positions itself as the primary alternative to China.
How We Got Here: From Hardware Trust to Software Scrutiny
The current standoff is not an isolated event but the culmination of a five-year shift in India’s digital sovereignty doctrine. Following the 2020 border clashes with China, India banned over 200 Chinese apps and introduced the “Trusted Telecom Portal” to secure network infrastructure.
However, the focus has now shifted from the network to the edge device. With smartphones becoming the primary repository of financial and biometric data for a billion Indians, regulators argue that trusting the hardware assembler is no longer enough—they must verify the software “brain.” The draft regulations, rooted in the National Centre for Communication Security (NCCS) guidelines, signal that New Delhi is no longer content with being a passive market; it demands the keys to the castle to verify there are no backdoors.
The Source Code “Red Line” and Intellectual Property
The most explosive proposal is the requirement for “Source Code Disclosure” to government-designated laboratories. For companies like Apple and Samsung, source code is the “crown jewel”—the proprietary DNA that differentiates a Galaxy from an iPhone.
The “Glass House” Dilemma Tech giants operate on a presumption of privacy. Handing over source code to a third-party lab—even a government one—multiplies the attack surface. If a government lab is hacked (a plausible scenario given global cyber-warfare trends), the blueprint for the world’s most popular operating systems could be leaked to the dark web.
- Industry Counter: They argue that security can be verified through “black box” testing (testing outputs without seeing the code) or certification on Common Criteria (CC) standards, which is the global norm.
- Government Counter: Without seeing the code, regulators cannot definitively rule out “logic bombs” or dormant surveillance scripts buried deep in the kernel, especially in devices originating from adversarial nations.
Security Theater vs. Real Vulnerability
A critical aspect of the analysis is whether these measures actually enhance security or merely increase bureaucracy.
The Patching Paradox The proposal to require government notification or approval before releasing major software updates is particularly contentious.
- The Risk: In the world of cybersecurity, speed is life. When a “Zero-Day” vulnerability is discovered, vendors race to push a patch in hours.
- The Bottleneck: If a patch must sit in a government queue for approval, millions of Indian devices remain vulnerable to active exploitation. Instead of protecting users, the bureaucracy could inadvertently leave the digital door open for hackers.
The Surveillance Anxiety
Privacy advocates warn that the cure may be worse than the disease. The mandate for devices to store 12 months of security audit logs (logins, app installs, permission changes) creates a massive, searchable database of user behavior right on the device.
If the government mandates access to these logs for “forensic” purposes, the smartphone effectively becomes a localized surveillance tool. This contradicts the industry’s move toward “data minimization” (collecting as little as possible). The requirement to scan for “tampering” (rooting/jailbreaking) also forces manufacturers to act as policemen, limiting how users can modify the hardware they effectively own.
Geopolitics and the “China Factor”
While the rules apply to all, the subtext is heavily focused on Chinese OEMs (Xiaomi, Vivo, Oppo), which control nearly 70% of the Indian market.
- Targeting Trust: New Delhi has long suspected that budget Chinese phones send data to servers in Beijing. These rules are a blunt instrument to force transparency.
- Collateral Damage: Western companies like Apple and Samsung are caught in the crossfire. They cannot comply with a law designed to catch Chinese espionage without breaking their own global privacy promises. This creates a diplomatic friction point between New Delhi, Washington, and Seoul.
Comparative Data: The Impact Analysis
The following tables break down the specific proposals and the winners/losers of this policy shift.
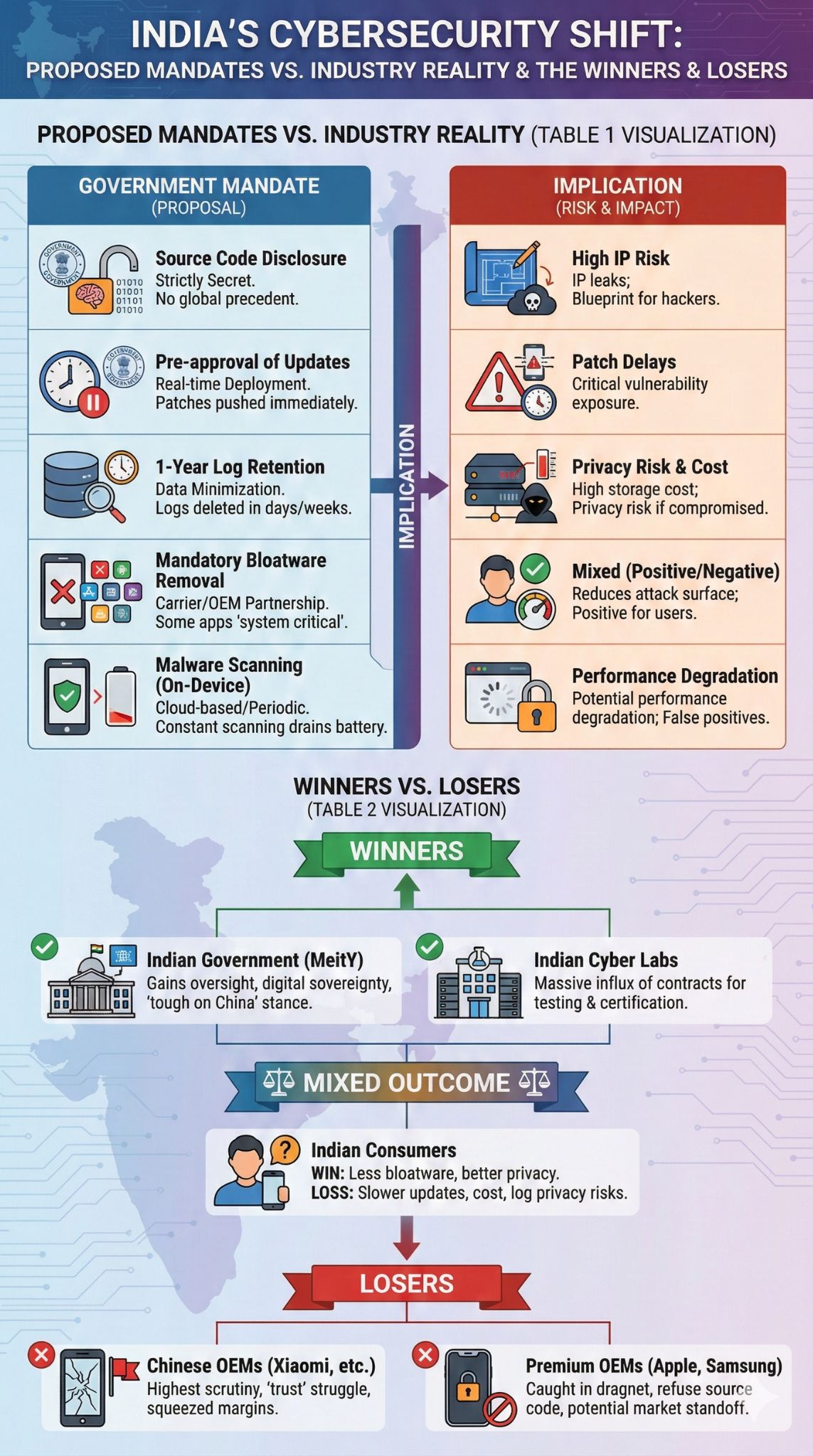
Proposed Mandates vs. Industry Reality
| Proposed Mandate | Industry Standard / Objection | Security Implication |
| Source Code Disclosure | Strictly Secret. No global precedent for mass disclosure. | High risk of IP leaks; creates a blueprint for hackers if labs are compromised. |
| Pre-approval of Updates | Real-time Deployment. Patches are pushed immediately. | Delays in patching critical vulnerabilities leave users exposed to active threats. |
| 1-Year Log Retention | Data Minimization. Logs are often deleted after days/weeks. | High storage cost; privacy risk if the device is seized or hacked. |
| Mandatory Bloatware Removal | Carrier/OEM Partnership. Some apps are “system critical.” | Positive for users. Reduces attack surface and improves performance. |
| Malware Scanning (On-Device) | Cloud-based/Periodic. Constant scanning drains battery. | Potential performance degradation; risks false positives blocking legitimate apps. |
Winners vs. Losers in the New Regime
| Entity | Status | Analysis |
| Indian Government (MeitY) | Winner | Gains unprecedented oversight and asserts digital sovereignty; signals “tough on China” stance. |
| Indian Cyber Labs | Winner | Massive influx of contracts for testing and certification of millions of devices. |
| Chinese OEMs (Xiaomi, etc.) | Loser | Face the highest scrutiny; likely to struggle with “trust” requirements; margins squeezed by compliance. |
| Premium OEMs (Apple, Samsung) | Loser | Caught in regulatory dragnet; will refuse source code sharing, leading to potential market standoffs. |
| Indian Consumers | Mixed | Win: Less bloatware, better privacy controls. Loss: Slower updates, potentially higher device costs, privacy risks from log retention. |
Expert Perspectives
To understand the nuance, we must look at conflicting expert views:
The National Security Hawk: “Smartphones are dual-use technologies. We cannot allow ‘black boxes’ from potentially hostile nations to operate in our critical infrastructure. If a foreign car manufacturer must meet local safety standards, why should a foreign phone manufacturer be exempt from software safety standards?” — Defense Analyst, New Delhi Think Tank.
The Privacy Advocate: “The road to hell is paved with good intentions. By forcing companies to build ‘access’ mechanisms for the government to review code, you are effectively mandating the creation of backdoors. Once a backdoor exists for the ‘good guys,’ it is only a matter of time before the ‘bad guys’ find it.” — Cybersecurity Researcher, Bengaluru.
The Industry Lobbyist: “This is a ‘Make in India’ killer. If Apple or Samsung cannot sell their global standard devices here without compromising their IP, they will simply prioritize other markets. You cannot demand global manufacturing leadership while imposing hyper-local, draconian software rules.”
Future Outlook: What Comes Next?
The current situation is a high-stakes poker game. The government’s denial of a “finalized” mandate suggests they are testing the waters to see how much the industry will bend.
The “Watered Down” Compromise (Most Likely): The government will likely drop the demand for raw source code sharing. Instead, they may settle for “Trusted Third-Party Audits,” where a neutral, international firm verifies the code without the government ever seeing it directly. This satisfies the security requirement without violating IP.
The Bifurcated Market: If India persists, we may see a “China Model” emerge, where Apple and Samsung create specific “India-only” versions of their OS (similar to iCloud in China) that comply with local logging rules. This would increase costs and fragment the ecosystem.
The Timeline:
- Q1 2026: Intense closed-door consultations. MeitY will likely issue a revised draft.
- Q2 2026: Implementation of the “easier” rules: Mandatory removal of pre-installed apps and clearer permission dashboards.
- Late 2026: Phased rollout of “Security Assurance” testing, likely starting with cheaper devices (under ₹15,000) where the risk of malware is higher.
Final Thoughts
India’s move is a bellwether for the “splinternet.” As nations realize that controlling the physical border is useless without controlling the digital border, mandates like this will become more common. However, the success of this overhaul depends on execution. If MeitY creates a nimble, trusted certification body, it could set a global standard. If it creates a bureaucratic bottleneck that demands trade secrets, it risks stalling India’s engine of digital growth.