Hey there, are you worried about keeping your supply chain data safe from sneaky cybercriminals? It’s a real headache when supply chain attacks mess with your business, steal important info, or hurt your good name.
Here’s a scary fact, folks: a supply chain attack often targets weaker links like suppliers or partners to sneak into a company’s system. That’s a tough pill to swallow, right? But don’t fret, my friends.
This blog post will arm you with 10 solid tips to boost your supply chain security and dodge those nasty cyber threats. We’ll chat about everything from risk assessments to data encryption, making sure your business stays strong.
Stick around for the full scoop!
Key Takeaways
- Spot weak links with risk assessments; stats show a 27.7% chance of data breaches in organizations.
- Secure suppliers since 60% of breaches tie to third-party risks; check for ISO 27001 certification.
- Use multi-factor authentication to block 99.9% of automated cyberattacks, as per Microsoft.
- Lock data with end-to-end encryption and verify authenticity using blockchain technology.
- Monitor in real-time with GPS and AI tools like Splunk to catch threats fast.
Conduct Comprehensive Risk Assessments
Digging into supply chain security starts with a solid plan. You’ve got to spot the weak links before they snap, right? Conducting full risk assessments helps you find both physical and digital threats lurking around your operations.
Think of it like checking your house for leaky pipes; you fix them before the flood hits. Stats show a scary 27.7% chance of data breaches for organizations, so ignoring this step is like leaving your front door wide open.
Now, let’s get real about where the danger often hides. Around 60% of data breaches tie back to third-party risks, meaning your suppliers or partners might be the crack in your armor.
Map out every piece of your supply chain, from warehouses to software systems. Pinpoint where cyber threats or physical gaps could strike. Use tools like risk management software or even basic checklists to catch issues early.
Stay ahead of supply chain risks, and keep those sneaky data breaches at bay.
Strengthen Supplier and Vendor Security
Hey there, readers, let’s talk about keeping your supply chain secure by prioritizing supplier and vendor security. It’s like constructing a solid fence around your backyard; you want to keep the valuable things in and the harmful things out.
Suppliers and vendors often manage sensitive information, so establishing clear security expectations for them is essential. Consider it as setting firm rules to shield against data breaches and supply chain attacks.
Now, take action by performing consistent security reviews with your partners. Maintain open and transparent communication, much like staying in touch with a friend. Evaluate their reliability by checking for certifications like ISO 27001, which demonstrates their commitment to information security.
By emphasizing third-party risk management, you’re not just protecting your data; you’re fortifying the entire network against cyber threats.
Implement Robust Cybersecurity Measures
Hey there, want to keep those pesky cyber crooks at bay? Locking down your supply chain data with tough digital defenses, like firewalls and encryption, is a surefire way to slam the door on threats.
Stick around to dig deeper into guarding your systems!
Use firewalls and encryption
Let’s talk about keeping your supply chain data safe with some solid tools, folks. Firewalls act like a tough bouncer at a club, blocking unwanted guests from sneaking into your network.
They stop cyber threats before they can mess with your info. Pair that with encryption, and you’ve got a killer combo. Think of encryption as a secret code that scrambles your data, making it unreadable to outsiders.
We’re talking about using the Advanced Encryption Standard (AES), a top-notch method to lock down your stuff.
Now, imagine hackers trying to crack into your system, but they hit a brick wall. That’s what firewalls and AES encryption do for supply chain security. They shield against data breaches and cyber attacks, keeping your business safe.
So, set up these defenses, and watch how they beef up your digital security. It’s like having a guard dog and a locked safe all in one!
Regularly update and patch systems
Hey there, keeping your systems fresh with updates and patches is a must for supply chain security. Think of it like fixing holes in a boat before they turn into big leaks. Regular system updates stop cyber threats from sneaking in through old, weak spots.
Every piece of software and hardware needs this care to block sneaky data breaches.
Now, don’t wait around for trouble to strike. Get those security patches rolled out as soon as they drop. It’s a simple step, but it slams the door on cyber-attacks trying to exploit outdated setups.
Stay ahead of risks, and keep your supply chain data safe from harm.
Ensure Data Integrity and Secure Communication Channels
Hey, wanna keep your supply chain data safe from sneaky cyber crooks? Use end-to-end encryption to lock down your info, making it tough for anyone to mess with your messages or steal your stuff.
Curious about more tricks to guard your data? Stick around and read on!
Use end-to-end encryption
Securing your supply chain data starts with a solid shield like end-to-end encryption. This method keeps your info locked tight from the moment it leaves your system until it reaches the other side.
No sneaky middleman can peek at your messages or files. By using this for all communications, as I’ve learned from the latest tips, you protect data in transit and at rest. It’s like sending a secret note in a sealed box that only the right person can open.
Think of end-to-end encryption as your trusty guard dog for supply chain security. It stops cyber threats from messing with your data, whether it’s moving or sitting still. Pair it with tools like secure communication apps, and you’ve got a strong defense against data breaches.
Stick with this approach, my friends, and watch those cybersecurity risks shrink. Let’s keep those digital bandits at bay with smart moves like encrypted data!
Verify data authenticity
Hey there, let’s chat about keeping your supply chain data real and true. Verifying data authenticity means making sure the info you get hasn’t been tampered with, like checking if a letter’s signature is legit.
It’s a big deal in supply chain management to stop sneaky data breaches or fake inputs from messing things up. Using blockchain technology can help a ton here, as it tracks and verifies data with a secure, unchangeable record.
Stick with cryptographic methods to lock in data integrity, folks. These tools act like a secret code, ensuring no one can twist the facts without you knowing. With blockchain for traceability, mixed with strong cyber security tricks, your supply chain risks drop fast.
Keep those digital fingerprints clean, and you’ll dodge a lot of cyber threats!
Monitor Supply Chain Operations in Real-Time
Hey, want to keep your supply chain safe from sneaky threats? Using sharp tools like GPS tracking and smart systems powered by machine learning can help you watch every move as it happens.
Stick around to learn more awesome tips!
Leverage advanced monitoring tools
Let’s talk about using cutting-edge tools to keep an eye on your supply chain. Advanced monitoring tools, like those powered by AI and machine learning, can spot odd patterns or cyber threats before they become big headaches.
These smart systems dig through tons of data in a snap, catching risks that humans might miss.
Think of Internet of Things (IoT) devices as your supply chain’s extra set of eyes. They track everything in real time, from shipment locations to warehouse conditions, using GPS tracking and smart surveillance.
With tools like Splunk, you can stay ahead of supply chain attacks and boost your security posture, keeping data breaches at bay.
Set up alerts for unusual activities
Hey there, readers, let’s chat about keeping an eye on your supply chain with smart alerts for unusual activities. Picture your supply chain as a busy highway; you’ve got to spot any odd detours or slowdowns fast.
Setting up alerts helps catch weird stuff, like unexpected delays or odd data patterns, before they turn into big headaches. It’s like having a trusty guard dog that barks when something’s off.
Now, imagine getting real-time notifications on your phone or computer the second a threat pops up. These quick heads-ups, tied to advanced tools like SIEM systems or machine learning algorithms, let you jump into action right away.
With supply chain security at stake, such warnings tackle cyber threats or sneaky supply chain attacks head-on. Stay sharp, and keep those alerts humming to dodge data breaches or other nasty surprises.
Implement Strong Authentication and Access Control
Hey, locking down your supply chain data is like guarding a treasure chest, and using multi-factor authentication is your toughest padlock. Stick around to catch more tips on keeping those digital thieves at bay!
Use multi-factor authentication
Let’s chat about a key way to guard your supply chain data, folks. I’m talking about multi-factor authentication, or MFA for short. It’s like adding an extra lock to your front door.
You don’t just use a key; you also need a code to get in. This method stops cyber crooks in their tracks, and get this, Microsoft says MFA blocks 99.9% of automated cyberattacks. That’s a huge win for your security posture!
Now, picture your supply chain as a treasure chest. Without MFA, it’s easier for hackers to sneak in and grab your data. So, put this shield up across all systems. Whether it’s for accessing a database or logging into cloud technology, make sure everyone uses multi-factor authentication.
It’s a simple step, but it fights off cyber threats like phishing attacks with real power. Keep those digital pirates at bay!
Limit access to sensitive data
Hey there, readers, let’s chat about keeping sensitive data safe in your supply chain. Locking down access is like guarding a treasure chest, you only give keys to those who truly need them.
Stick to the least privilege principle, which means folks get just enough access to do their jobs, nothing more. This cuts down on risks like data breaches or stolen data sneaking out.
Now, keep a sharp eye on privileged accounts, the ones with bigger keys to your system. Check them often to spot any odd moves. Using role-based access controls helps here, tying access to specific jobs.
Pair this with multi-factor authentication for an extra safety net. Think of it as double-locking your front door, making it tough for cyber threats to slip in.
Enhance Physical Security in Supply Chain Facilities
Securing your supply chain isn’t just about digital defenses; physical security matters a ton too. Think of your warehouses as a vault holding precious goods. You can’t let just anyone waltz in.
So, slap on some surveillance cameras to keep an eye on every corner. Add access control systems to lock down who gets in and out. These tools act like a watchdog, always on guard against sneaky intruders or supply chain risks.
Also, bring in on-site security personnel to patrol the grounds. They’re your boots on the ground, ready to tackle any funny business. Don’t skip regular audits to spot weak spots in your setup.
Check doors, locks, and fences for any gaps. By staying sharp with physical security, you cut down on threats that could mess up your logistics. Keep those facilities tight as a drum!
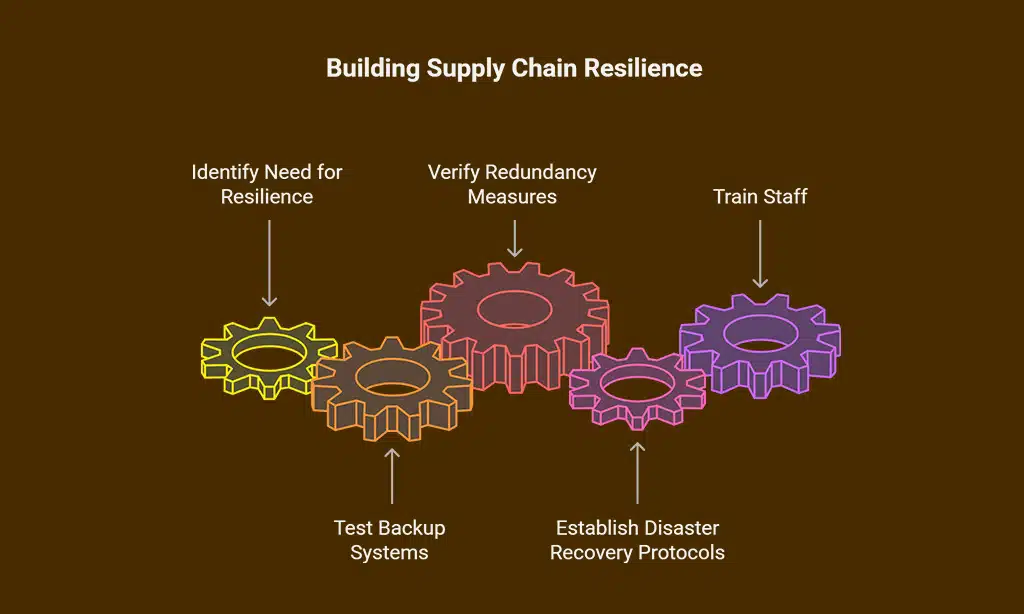
Build Resilience with Redundancy and Backup Plans
Hey, want to keep your supply chain running, no matter what hits? Building solid backup systems and spare plans can save the day when surprises strike!
Regularly test backup systems
Testing backup systems often is a must for supply chain security. You don’t want to find out they fail when disaster strikes. So, check them monthly or quarterly to confirm reliability.
This step keeps your data safe from cyber threats or sudden data loss. Imagine losing everything, only to realize your backup is a dud, what a mess!
Now, get hands-on with those redundancy measures. Verify they work as planned by running test restores. A solid backup isn’t just a file sitting there; it’s your lifeline during supply chain attacks.
With data breaches lurking, this habit boosts your business continuity. Keep it simple, test often, and stay ahead of trouble.
Establish disaster recovery protocols
Hey there, let’s chat about setting up solid disaster recovery protocols for your supply chain. Disasters can strike out of nowhere, like a storm hitting a warehouse, and you’ve got to be ready to bounce back fast.
Having a clear plan in place, like a roadmap during a road trip, keeps your data and operations safe from cyber threats or physical mishaps.
Now, get this, developing comprehensive disaster recovery plans is a must. Train your staff on these steps so everyone knows their role when trouble hits. Think of it as a fire drill, but for supply chain resilience.
With the right disaster recovery setup, you’re not just reacting; you’re staying one step ahead of data loss prevention challenges.
Comply with Industry Standards and Regulations
Hey, sticking to the rules in your supply chain game is a must, ya know! Following top guidelines like those from the National Institute of Standards and Technology can keep your data safe from nasty cyber threats.
Follow ISO and NIST guidelines
Adhering to ISO and NIST guidelines is a wise choice for maintaining strong supply chain security. These standards, established by leading organizations, provide a straightforward path to avoid cyber threats and data breaches.
Consider them a reliable compass, assisting you in creating a firm security foundation without becoming overwhelmed by confusion.
By complying with these principles, you manage supply chain risks effectively through established methods. Consistent evaluations and updates, as recommended by ISO and NIST, ensure your protections remain effective against subtle threats.
So, engage with these frameworks, and see your data privacy and cybersecurity risks diminish noticeably.
Conduct regular compliance audits
Hey there, let’s talk about keeping your supply chain safe with regular compliance audits. These checks are like a health checkup for your business, making sure everything follows the rules.
By doing audits often, you spot gaps in data security or supply chain risks before they turn into big headaches.
Stick to this habit, and address any compliance gaps fast, as they pop up during these reviews. Think of it as fixing a leaky pipe before it floods the house. With standards like ISO or NIST as your guide, audits help strengthen your security posture against cyber threats and data breaches.
So, keep at it, and stay one step ahead of trouble!
Foster a Culture of Security Awareness and Training
Hey, want to keep your supply chain data safe? Start by training your team to spot cyber threats and act fast!
Provide regular security training for staff
Let’s chat about keeping your team sharp on supply chain security, folks. Regular security training for staff is a must. It’s like giving your crew a map to dodge cyber threats. Schedule these sessions often, and make sure every employee joins in.
Use real examples, like sneaky data breaches or the infamous SolarWinds attack, to show the risks. This keeps everyone alert and ready.
Now, think of training as a shield against cyber villains. Update your materials to match new tricks hackers pull. Focus on hot topics, like data privacy and spotting malicious code.
Toss in tips on multi-factor authentication too. Make it fun, maybe with a quiz or a game, to keep your team hooked on cybersecurity training.
Encourage reporting of security concerns
Hey there, folks, let’s chat about making your workplace a safer spot by speaking up on security worries. Got a gut feeling something’s off with the supply chain data? Don’t keep it hush-hush.
A simple system for employees to report security concerns can catch cyber threats before they blow up. Think of it like being the early bird that spots the worm, or in this case, a sneaky data breach.
Now, imagine a setup where everyone feels safe to flag odd stuff without fear. Push for a proactive stance on security issues, and watch how it tightens your supply chain security.
If you see a glitch or a weird login attempt, report it fast. This isn’t just about dodging cyber security breaches; it’s about building a wall against supply chain attacks. So, speak up, and help keep the bad guys out!
Takeaways
Wow, we’ve covered a lot of ground on securing supply chain data, haven’t we? Let’s wrap this up with a quick nudge to act. Start putting these ten practices into play, from risk checks to real-time tracking with cool tools like GPS systems.
Trust me, taking these steps can shield your business from nasty cyber threats. So, go on, beef up that security and keep your supply chain rock solid!
FAQs on Best Practices for Securing Supply Chain Data
1. What’s the big deal with supply chain security, and why should I care?
Hey, supply chain security is no small potatoes; it’s about guarding your business from cyber threats and data breaches that can cripple operations. Think of supply chains as the lifeblood of commerce, and any glitch, like a sneaky supply chain attack, can cost millions. Let’s not let those cyber crooks mess with our critical infrastructure, alright?
2. How can data encryption help protect my supply chain data?
Data encryption is like locking your treasure chest with a secret code. It scrambles your info so cyber villains can’t read it, even if they sneak into your system. This is a solid step to dodge data privacy disasters in supply chains.
3. Why are security audits a must for dodging supply chain risks?
Listen up, running security audits is like giving your supply chain a health checkup. It spots weak links, uncovers security vulnerabilities, and helps with risk assessment before a cyber mess, like the SolarWinds attack, hits hard.
4. Can multi-factor authentication really stop supply chain attacks?
You bet it can! Multi-factor authentication is like adding an extra deadbolt to your digital door, making it tougher for hackers to barge in and exploit zero-day vulnerability issues in your network.
5. How does real-time monitoring boost my supply chain resilience?
Picture this, real-time monitoring is your watchdog, always on the lookout for cyber threats with tools like GPS tracking and machine learning. It catches weird activity fast, helping with threat detection before a breach spirals out of control. This keeps your security posture strong, no matter the sneaky tricks hackers pull.
6. Should I worry about third-party risk management in my supply chain?
Oh, absolutely, third-party risk management is your safety net when you outsource or use the cloud infrastructure. Those partners might have shaky ITS security or skip software updates, opening doors to cyber risks. Stay sharp with cybersecurity training and penetration testing to keep those supply chain risks at bay.