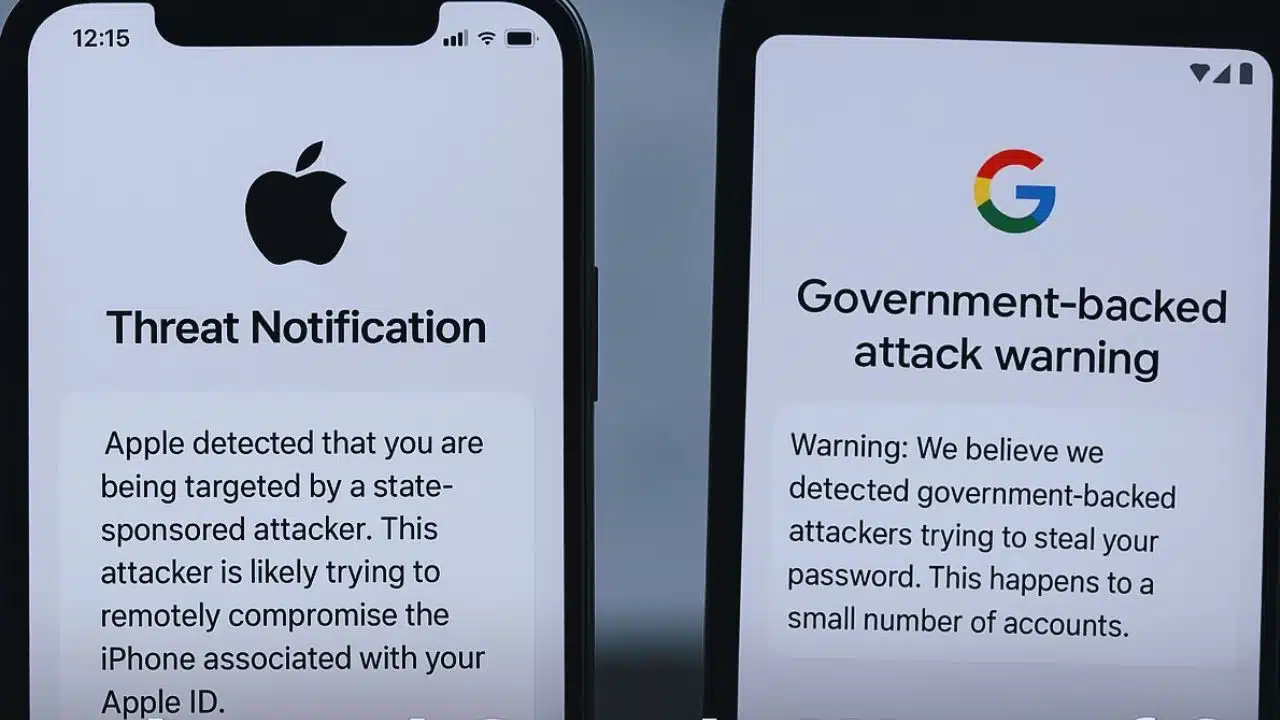
Apple and Google have issued a new wave of cybersecurity alerts to users across the world, warning them about highly sophisticated spyware campaigns believed to be backed by state actors or powerful commercial surveillance companies. These warnings reflect a growing pattern of digital espionage targeting individuals who are often at the center of sensitive political, social, or journalistic environments.
Apple sent out its notices on December 2 to users in 84 countries, marking yet another significant escalation in the tech giant’s efforts to inform people when they may have been singled out by government-linked hackers. Google followed a day later with its own notifications sent to several hundred accounts, particularly in countries such as Pakistan, Kazakhstan, Angola, Egypt, Uzbekistan, Saudi Arabia, and Tajikistan—regions where digital surveillance operations have historically raised concerns among rights groups.
Both companies emphasized that these alerts are not routine spam but high-confidence warnings based on internal threat intelligence. Their notifications typically indicate that a user may be part of a targeted campaign, not a broad, indiscriminate cyberattack. Apple also noted that it has now issued threat alerts in more than 150 countries overall, underscoring how widespread and global these operations have become. Past waves of Apple’s warnings have triggered scrutiny from lawmakers and regulators, especially in the European Union where high-level officials have been targeted with commercial spyware. Experts say that even the act of alerting users disrupts spyware operations by forcing attackers to change tactics, slow down activity, and face increased public and regulatory pressure.
Intellexa’s Spyware Network Continues Operating Despite Sanctions
Google’s latest threat intelligence places particular focus on Intellexa, a Cyprus-based spyware consortium sanctioned multiple times by the United States for its role in creating and distributing the Predator spyware. Despite these sanctions, Intellexa appears to be operating actively and adapting to restrictions. Google’s security researchers revealed that the firm has exploited at least 15 zero-day vulnerabilities since 2021—representing more than one-fifth of all major zero-days discovered by the company’s teams in that period.
Zero-day exploits are especially dangerous because they target previously unknown flaws that software developers have no chance to fix before the attacks occur. This level of technical capability suggests that Intellexa’s tools are well-resourced and engineered to bypass even modern device protections. A recent joint investigation highlighted that Intellexa has developed an advanced zero-click infection system named “Aladdin,” which can compromise devices through malicious online advertisements alone. This means people do not need to click, download, or interact with anything—simply loading a webpage with the infected ad is enough to trigger a silent attack.
Privacy advocates warn that this kind of weaponization of the advertising ecosystem poses an unprecedented threat to everyday smartphone users. It also exposes vulnerabilities in the broader digital infrastructure relied on by billions of people worldwide.
A Growing Global Pattern of Surveillance and the Push for Accountability
The alerts from Apple and Google fit into a much larger global trend: the increasing use of commercial spyware tools by governments and private clients to monitor journalists, activists, dissidents, business leaders, and political figures. While these tools are often marketed as solutions for law enforcement and counterterrorism, numerous investigations have shown they are frequently misused to surveil critics and suppress dissent.
Google announced it is adding domains associated with Intellexa to its Safe Browsing service, further attempting to block malicious operations at the browser level. The company is also continuing to issue direct government-backed attack warnings to any account believed to be linked to past targeting campaigns. Meanwhile, security experts emphasize that public notifications often become the first step in exposing broader abuses. Once a victim becomes aware of a possible attack, civil society organizations and investigative bodies can begin tracing the origins, uncovering networks of clients, and demanding accountability.
The continued expansion of these alerts highlights an urgent global need for stronger oversight, improved transparency around spyware vendors, and better protection for individuals at risk. As spyware tools grow more advanced—particularly with zero-click delivery systems—the responsibility increasingly falls on technology companies, policymakers, and the international community to confront the escalating threat and safeguard digital rights.