Online threats lurk in every app and site. You might miss a hack until it hits you. Weak security can cost you data and cash. You need clear threat detection that works without a full IT crew.
Artificial intelligence and machine learning can spot threats ten times faster. We cover seven hosts that use AI for cloud security and threat hunting. You will learn how Azure Security, GuardDuty, and Darktrace stand guard.
These tips help you pick a plan that fits your needs. Read on.
Key Takeaways
- Seven hosting services use AI and machine learning to hunt cloud threats ten times faster and cut false positives by up to 90%.
- Azure Security blends SIEM, cloud log monitoring, and Microsoft Defender to spot zero-day attacks in real time and send instant alerts.
- AWS GuardDuty applies DIGEST and DEMIST-2 models to CloudTrail and VPC Flow Logs for automated anomaly detection and response.
- Google Cloud Threat Intelligence taps Mandiant AI in Security Command Center and SIEM tools to block breaches in VM instances and container clusters.
- Darktrace, IBM QRadar on Cloud, Vectra AI, and SentinelOne Singularity use self-learning AI, NDR, and EDR to watch thousands of endpoints and trigger automated incident response.
Microsoft Azure Security
Azure spots strange logins, data leaks, and sudden traffic spikes with its smart security dashboard, and it shoots instant alerts to your team. It blends threat intelligence, incident playbooks, and a cloud log monitor into one tool, so you can tackle zero-day attacks in a snap.
AI-driven threat detection and response
Security logs pour in from servers, apps, and devices. A cloud SIEM analyzes that data in real-time. It uses machine learning to spot odd behavior and flag anomalies. That mix of threat detection and threat hunting predicts attack trends.
Teams gain situational awareness in the cloud.
That service then summarizes incidents and recommends responses. It links to Microsoft Defender for automated incident response. It filters false positives and cuts alert fatigue. It tracks advanced persistent threats across endpoints and network paths.
Teams see real-time monitoring and clear guidance.
Integration with existing Microsoft services
Azure Security meshes with Microsoft Defender, the EDR solution, and Sentinel to guard cloud workloads. It feeds logs into SIEM and NDR tools. Teams can share threat alerts via Microsoft 365 Defender.
You can connect Intune and Azure Active Directory in minutes. This setup scans for zero-day attacks and insider threats. It uses machine learning, natural language processing, and AI to spot anomalies.
It links to Microsoft Security Copilot to speed threat hunting and automated incident response. Admins can build custom playbooks in Azure Logic Apps. You can tweak detection rules to match each network.
It plugs into Microsoft Graph API for real-time monitoring and incident workflows. This design fits best for users in the Microsoft ecosystem and lets you customize cloud security with ease.
Amazon Web Services (AWS) GuardDuty
GuardDuty uses machine learning to mine CloudTrail and VPC Flow Logs for odd activity. It sniffs out zero-day tricks like a guard dog and sends threat intelligence updates in real time.
Automated threat detection for cloud workloads
AWS GuardDuty spots threats in cloud workloads with AI. It applies machine learning models like DIGEST and DEMIST-2 for improved threat prioritization, anomaly detection, and analysis.
The service feeds threat intelligence data into security information and event management tools to guard against zero-day attacks.
It flags unusual API calls, VPC flow records, and log anomalies in real-time monitoring. Automated incident response kicks in after detection, which speeds up threat hunting and cuts alert fatigue.
Cloud security teams gain proactive defense and fast response automation.
Machine learning for anomaly detection
Amazon Web Services GuardDuty runs DIGEST and DEMIST-2 to flag odd traffic. The models track changes in log patterns and spot rare behaviors. They slash false positive alerts by up to 90%.
SOCRadar hooks into GuardDuty, feeding fresh threat intelligence into the analytics engine. Security teams see risks in real time and hunt down lurking cyber threats.
Continuous dark web scans feed silent chatter into the system. Machine learning acts like a guard dog, sniffing out zero-day attacks and insider threats. This rapid risk identification lets teams patch gaps before hackers strike.
Google Cloud Threat Intelligence (Mandiant)
Google Cloud’s threat detection feed taps Mandiant’s attack data to spot zero-day breaches in VM instances and container clusters. It sends clear alerts to Security Command Center so you can block malware fast before it spreads.
AI-enhanced threat monitoring
Mandiant platform scans logs with artificial intelligence. It uses DIGEST and DEMIST-2 models to rank threat alerts. Security teams hunt anomalies in network detection and response and endpoint detection and response data.
Real-time monitoring ties into SIEM for automated incident response to zero-day attacks. The process slashes false positives and boosts proactive detection of insider threats and data leaks.
One of seven hosting services using AI, it offers a user-friendly interface for small and medium enterprises.
Advanced reporting and actionable insights
Google Cloud Threat Intelligence taps Mandiant AI. It offers advanced reporting and actionable insights for threat detection. Machine learning drives anomaly detection. SIEM links logs and network traffic analysis in one place.
Teams run threat hunting from a single dashboard. It shines a spotlight on hidden risks like a searchlight in the fog. They spot zero-day attacks faster with automated incident response.
It ranks among seven AI hosting services covered in this guide. Other hosts, like SOCRadar, mix vulnerability feeds with dark web monitoring for industry-specific alerting. This mix speeds up security operations.
It cuts false positives and boosts real time monitoring across cloud security.
IBM Security QRadar on Cloud
It scans cloud logs like a hawk, so lurking cyber threats can’t slip past. It mixes machine learning and security analytics to cut alert noise, then pushes clear incident alerts in real time.
AI-powered threat analytics
IBM Security QRadar on Cloud links security event manager and SOAR modules with machine learning models. Machine learning analyzes historical data to predict attack trends. The system uses anomaly detection to flag odd network traffic.
Threat intelligence feeds enrich detection context. Zero-day exploits show up in risk dashboards. Security analysts receive instant alerts.
Analysts work inside the security event manager interface to hunt malware. EDR integration brings endpoint detection and response data. Automated incident response kicks in on confirmed threats.
Teams review logs in seconds. Network traffic analysis powers risk graphs. Alert fatigue drops as false positives shrink. AI cybersecurity tools drive better decisions.
Real-time detection of malicious activities
IBM QRadar on Cloud runs AI analytics on logs and events. It scans millions of alerts every second. Devices stream logs for proactive threat detection via data scans. The system blends SIEM with network traffic analysis and NDR tools.
Users see threats fast. Real time response automation kicks in. Security teams get faster incident response.
The platform uses machine learning for anomaly detection. It hunts zero-day attacks and insider threats. It links with endpoint security like Microsoft Defender. The tool cuts alert fatigue for analysts.
Cloud security stays strong with deep data scanning. Teams can focus on threat hunting.
Vectra AI
Vectra AI uses network detection and response, it tracks odd moves in traffic with machine learning. It cuts alert noise, so teams chase real threats with more speed and less guesswork.
Network threat detection using AI
AI tools spot odd traffic in real time. A smart NDR engine scans every packet. It flags anomalies with machine learning models. Teams get alerts with context-aware prioritization. They chase real threats, not noise.
This cuts alert fatigue. A managed detection service takes over busy shifts. It hunts hidden threats so analysts can rest.
A SIEM platform adds threat intelligence feeds from email security logs and cloud security tools. It links internal events to dark web monitoring. This boosts anomaly detection across endpoints.
The system profiles devices on IoT networks. It spots insider threats and phishing attempts fast. IT staff see clear dashboards. They fix zero-day attacks before damage shows.
Scalable solutions for large enterprises
Large enterprises face vast networks that span offices, clouds, and data centers. Vectra AI uses network detection and response with machine learning to watch traffic in real time.
It spots anomalies, like odd login bursts or stealth scans. The system scales across tens of thousands of endpoints. Users sync logs with SIEM and threat intelligence feeds. Integrations work with FortiGate and Palo Alto gear.
Some firms note limited reporting capabilities. The docs need work too.
A global bank handling billions of transactions counts on this NDR engine to sniff out insider threats and zero-day attacks. Vectra cuts alert fatigue with automated threat hunting and deep learning insights.
It taps network traffic analysis and natural language processing. Engineers see malware traces in minutes. The platform links with Microsoft Defender and GuardDuty. A few admins want fuller guides.
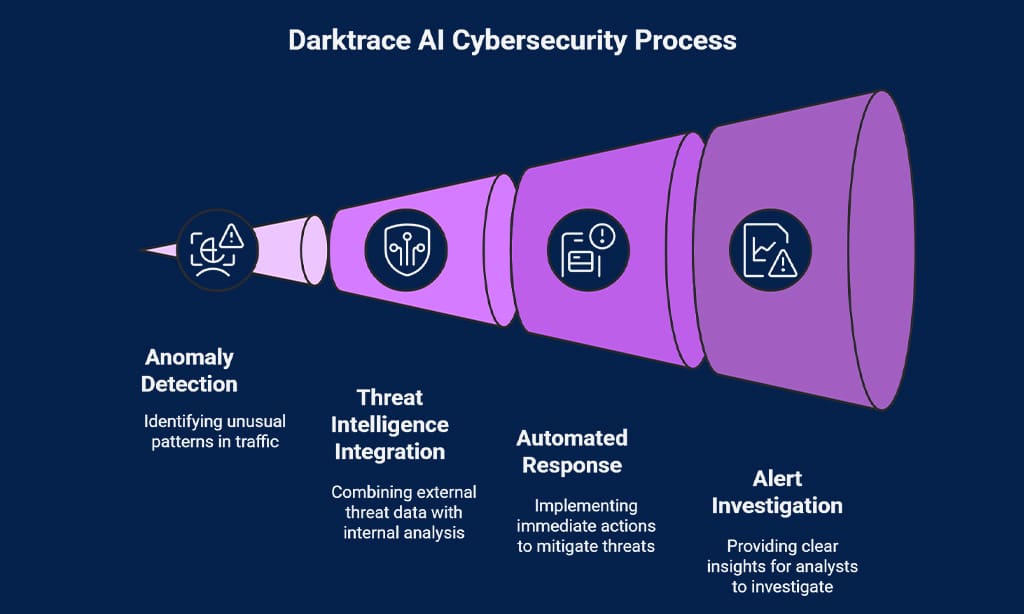
Darktrace
Darktrace uses adaptive AI to learn normal network flows. It flags zero-day attacks fast and taps threat intelligence feeds to guide auto incident response.
Self-learning AI for cybersecurity threats
That smart software powered by machine learning kicks into gear when an odd pattern pops up. DIGEST and DEMIST-2 models scan packet flow, spot anomalies, and learn new tricks overnight.
This adaptive system drives threat hunting, from phishing emails to insider mishaps, without constant updates. It slices alert fatigue, so teams can focus on real risks.
Engineers plug self-learning AI into cloud security stacks and workstation agents for endpoint detection. The models tweak rules on their own, cutting zero-day attack windows. One team joked that the AI even learned their coffee habit.
This tool stops data leaks, guides incident response, and shields against cyber threats.
Proactive response to advanced attacks
Darktrace AI Sentinel learns each network pulse. It spots odd traffic in real time. Machine learning flags zero-day exploits. Automated threat mitigation springs into action. It blocks malicious moves within seconds.
Autonomous alert investigation gives analysts clear clues.
AI Sentinel adapts as attacks grow more sly. It blends threat intelligence feeds with anomaly detection. Teams see alerts on friendly dashboards. SIEM tools sync logs for deeper threat hunting.
This mix cuts dwell time and tames cybercriminals.
SentinelOne Singularity
SentinelOne Singularity shields your laptops, servers, and IoT gadgets with machine learning that learns new attack patterns in minutes, not days. Its endpoint detection and response agent yanks zero-day malware out like a bouncer tossing out troublemakers, so the AI defender locks the door on new threats before they sneak in.
AI-based endpoint protection
Hey, did you catch that alert? It jumped off the screen. A single agent boosts endpoint security by combining endpoint detection and response (EDR) with XDR for smarter threat detection.
Machine learning spots zero-day attacks and hunts insider threats in real time. The tool taps into threat intelligence feeds and cuts alert fatigue.
Security staff smile at fewer false positives. They see clear alerts and swift triage. The service runs on desktops, servers, and mobile gear. It uses cybersecurity automation to seal data leaks and block phishing.
Its single-agent design saves CPU cycles and keeps systems humming.
Automated threat mitigation
A Purple AI assistant works like a guard dog. It spots cyber threats, and it fires a real-time automated response. The system triggers firewalls, blocks suspicious code, and starts automated incident response at once.
It uses endpoint detection and response (EDR) tools and machine learning for anomaly detection. This AI cybersecurity tool cuts down alert fatigue and stops zero-day attacks before they spread.
How to Choose the Best AI Hosting Service for Your Needs
Match your needs to the right mix of SIEM, EDR, and NDR features. See how Defender for Cloud, GuardDuty and Singularity XDR stack up on cost, customization, and cloud security.
Scalability and customization
Cloud hosts grow or shrink on demand, so threat detection scales with your team. Microsoft’s cloud shield spots zero-day attacks in real time, and Amazon’s threat sensor learns anomalies with machine learning.
AI in cybersecurity hunts threats before escalation, and it adapts defenses fast.
Teams tweak rules in minutes to fit new apps. Google’s threat radar feeds actionable insights to SIEM tools, and it cuts alert fatigue. IBM’s analytics engine tracks insider threats and data leaks with automated incident response.
Scale up scanning in seconds, then dial back to save on cloud security costs.
Integration with existing systems
Azure Security links with most SIEM tools and SOAR engines. It streams logs to a log analysis platform and spins up automated incident response playbooks. It taps Microsoft Security Copilot, which uses natural language processing to sift alerts, and Microsoft Defender, so you spot cyber threats fast, and hunt anomalies or zero-day attacks.
You drop it in your ticketing flow or chat rooms, like a puzzle piece, and it snaps into place. It feeds email security events and endpoint detection and response alerts into your NDR setup.
That mix makes threat intelligence richer, cuts false positives, and helps you hit attacks before they hit you.
Cost considerations
Price tags can sway your choice. Darktrace quotes run near $30,000 per year. Tessian costs vary, you must ask sales. Some services bill by cloud nodes or endpoint count. Hidden fees can pop up for threat detection updates and machine learning models.
Consider free trials and pay-as-you-grow plans. Choose a service with clear per-use rates. Compare add-ons like email security or network detection and response tools. Spot costs for threat hunting, automated incident response, and SIEM integration.
This helps you balance budget and protection.
Takeaways
As cyber threats become more sophisticated, relying on traditional security measures is no longer enough. The hosting providers highlighted in this list are leading the way by integrating AI-driven threat detection to offer smarter, faster, and more adaptive protection. Whether you’re managing a personal blog or a large-scale enterprise site, choosing a hosting service that leverages artificial intelligence for security can provide peace of mind and a powerful layer of defense.
Stay proactive—opt for intelligent hosting that evolves with the threat landscape.
FAQs on Hosting Services That Use AI for Threat Detection
1. What is real-time threat detection in hosting services?
Hosts use ai in cybersecurity to scan network traffic, they run machine learning models, they flag odd patterns with anomaly detection, they do real-time monitoring to halt cyber attacks fast.
2. How does automated incident response work?
The system spawns an alert, then runs scripts that block bad IPs and roll out security patches. It acts like a guard dog on patrol, it draws on threat intelligence feeds to stay ahead.
3. Which tools help fight zero-day attacks?
Hosts tap endpoint security, endpoint detection and response (EDR), and network detection and response (NDR). They lean on predictive engine and V-AI. They hunt threats without a rulebook, closing blind spots in the dark.
4. Can hosting stop insider threats and phishing?
Absolutely. They mix email security and phishing detection with SIEM logs. They weave in natural language processing to check a message’s tone, like a private eye, spotting shady links before they bite.
5. How do services reduce false positives and alert fatigue?
They layer deep learning models, they tweak thresholds. Who likes alerts? Not you, not me. They log session cookies, persistent cookies and scan for anomalies, then tune filters with dark web monitoring to trim useless alarms.
6. Does cloud security cover data governance and IoT devices?
Yes. Good hosts vault data loss prevention, they follow National Institute of Standards and Technology guides. They lock down IoT security, they run federated learning on device data. They patch fast, they keep your site safe.