You know that feeling when you have the perfect ingredient for a recipe, but it’s in a jar you just can’t open? That’s exactly what the blockchain world felt like for years. You had value on Ethereum and opportunity on Solana, but no safe way to connect them. From my perspective as a lifestyle and market analyst, true efficiency only happens when systems talk to each other seamlessy.
Cross-Chain Bridges are the digital infrastructure solving this fragmentation. They allow blockchains to exchange data and value, much like how SWIFT lets different banks communicate. However, this convenience came with a high price tag in the early days.
According to Chainalysis, cross-chain bridges were exploited for approximately $2.8 billion in stolen assets by mid-2025 alone. That data point isn’t just a statistic; it’s a clear signal that security is the dividing line between a gambling tool and a genuine financial utility. Today, the conversation has shifted from “how do we move tokens?” to “how do we move them without losing sleep?”
In this guide, I’ll walk you through the mechanics of these bridges, the massive security upgrades like Circle’s CCTP that are restoring trust, and the smart features you need to look for right now.
What Are Cross-Chain Bridges?
Cross-chain bridges connect different blockchains and let digital assets move freely between them. These tools help cryptocurrencies “travel,” making many new things possible for users and projects alike.
Definition and purpose
A bridge is a protocol that lets digital assets move between two different blockchain networks. Without a bridge, your Bitcoin is stuck on the Bitcoin network, completely cut off from the decentralized finance (DeFi) apps on Ethereum. It’s like trying to use US dollars directly in a Tokyo vending machine without exchanging currency first.
For example, Chainlink’s Cross-Chain Interoperability Protocol (CCIP) has become a standard for this, allowing not just tokens but also data to flow securely between chains. This capability is what allows developers to build applications that harness the speed of one chain and the security of another simultaneously.
People use bridges so they do not have to stay on just one blockchain. Many see bridges as key for interoperability because users want easy asset transfer without extra steps. These connections let different blockchains exchange data or money, helping users skip slow swaps or risky workarounds.
Importance in blockchain interoperability
Interoperability is the backbone of a mature digital economy. If all chains stayed separate, people would lose out on better liquidity and choices for their digital assets. For instance, a 2025 report by The Business Research Company projected the DeFi market would grow to over $42 billion, a surge driven largely by the ability to move capital efficiently across networks.
Cross-chain bridges help blockchains talk to each other. They make asset transfer fast and simple, lowering the need to rely on one blockchain only. This connection lets digital assets, like cryptocurrencies, move across different networks with ease. However, the risk remains real.
Expert Insight: “The rise of cross-chain communication is critical, but with over $2.8 billion stolen from these protocols recently, the focus must shift from speed to verifiable security.”
These facts show why secure crosschain protocols are crucial in today’s blockchain infrastructure. Blockchains need these bridges to swap data and value safely between networks such as Ethereum and Bitcoin.
Why Interoperability Matters in Crypto
Interoperability lets digital assets move smoothly across blockchains. This helps users do more with their cryptocurrency, without being stuck on one network.
Enhanced liquidity for assets
Moving assets between blockchains is much easier with cross-chain bridges. Users can transfer tokens from one blockchain to another in a few steps. This helps connect several networks, which lets people buy, sell, or swap digital assets more freely. In the US market, this fluidity is essential for traders who need to arbitrage prices between exchanges quickly.
For example, someone with Bitcoin can use a bridge to move their coins to Ethereum and trade them on a DeFi app there. This breaks down the “walled gardens” that trap value.
| Feature | Isolated Blockchain | Interoperable Ecosystem |
|---|---|---|
| Liquidity Access | Limited to one network’s users | Access to global capital pools |
| Asset Utility | Store of value only | Used as collateral in DeFi apps |
| Transaction Speed | Network dependent (often slow) | Can route to faster chains |
Reports show massive losses from bridge hacks, which highlights the need for better security as activity grows. Still, secure cross-chain solutions keep improving asset flow across platforms. More connected networks help reduce the risk of assets getting stuck in just one place or being left out of new blockchain opportunities.
Access to multiple blockchain ecosystems
Cross-chain bridges let you use assets on different blockchain networks. For example, you can move your tokens from Ethereum to Solana, or even swap them for others like Avalanche or Polygon in seconds. This smooth transfer opens the door for more choices and better asset management.
Interoperability like this helps users join many digital asset communities without being tied to just one network. A prime example is the Portal Token Bridge (formerly Wormhole), which connects over 20 networks, allowing users to access the unique apps and communities on each one.
Even with risks, secure multichain infrastructure is growing fast. These bridges build strong connections between blockchains so people enjoy wider access while reducing reliance on any single crypto system. This shared space lets projects and investors work together easily across different blockchain ecosystems.
Reducing reliance on a single blockchain
Dependence on one blockchain can cause problems. If that network fails or faces hacking, users may lose access to their digital assets. Chainalysis reports show billions have been stolen from bridge hacks in recent years, highlighting how risky it is if everyone uses only one system.
Interoperability lets users move assets and data across different blockchains using solutions like crosschain bridges. It allows people to find better fees, faster transactions, and stronger security by spreading activity over many networks.
Developers are now building secure protocols so locking, verifying, and unlocking work safely without relying on a single chain for all steps. This keeps value moving even if one part goes down or gets attacked as seen before in the crypto space.
How Do Cross-Chain Bridges Work?
Cross-chain bridges link two blockchains, letting users move their tokens between them with ease. Think of these bridges as digital highways, each using different rules to keep your assets safe on the journey. Understanding the mechanism is the best way to protect your investments.
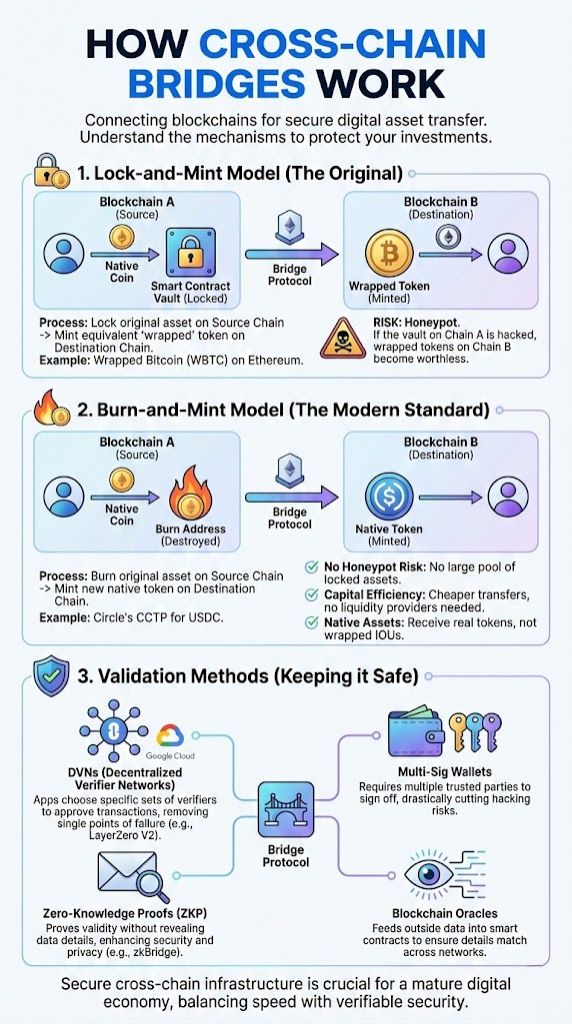
Lock-and-mint model
The lock-and-mint model keeps your cryptocurrency safe during asset transfer. First, it locks your digital assets on the original blockchain using a smart contract. Next, it creates (or “mints”) new tokens on another blockchain. These new tokens are called wrapped tokens.
For example, Wrapped Bitcoin (WBTC) uses this model. You lock real Bitcoin with a custodian, and an equivalent amount of WBTC is minted on Ethereum. This system helps blockchains communicate and share value without losing track of real ownership. It also cuts out extra steps for users who need quick access across ecosystems like DeFi or NFT platforms.
However, this model creates a “honeypot” risk. If the smart contract holding the locked Bitcoin is hacked, the wrapped tokens on the other side become worthless instantly. Safer models now focus on strong smart contracts and decentralized ways to verify each step.
Burn-and-mint model
Burn-and-mint bridges work by destroying, or “burning,” your tokens on one blockchain before making new, or “minted,” tokens for you on another. This is the modern standard for efficiency and safety. A leading example is Circle’s Cross-Chain Transfer Protocol (CCTP), which allows USDC to move natively between chains without using a wrapped version.
For instance, if you want to move cryptocurrency from Blockchain A to Blockchain B, the bridge will burn your coin on Blockchain A and mint a new version on Blockchain B. This method helps keep the total supply steady across different networks and reduces the risk of double spending.
- No Honeypot Risk: Since tokens are burned, there is no massive pool of assets for hackers to target.
- Capital Efficiency: You don’t need to pay liquidity providers, making transfers cheaper.
- Native Assets: You get the real token at the destination, not a “wrapped” IOU.
Cybersecurity is still key here because hackers have stolen billions in digital assets from cross-chain bridges. The burn-and-mint model adds some safety since there are no extra coins floating around between chains. Still, it can be a target for attacks if smart contracts have vulnerabilities.
Validation methods
Cross-chain bridges use different ways to check and approve asset transfers. These validation methods help keep asset transfer safe and lower security risks.
- Decentralized Verifier Networks (DVNs): Used by LayerZero V2, this allows applications to choose a specific set of verifiers (like Google Cloud or Polyhedra) to approve transactions, removing the single point of failure.
- Validators watch the network and agree on each transaction before allowing the transfer of digital assets, like wrapped tokens, between blockchains.
- Some bridges use multi-signature wallets which need several trusted parties to sign off for each move, drastically cutting down on hacking risks.
- Zero-Knowledge Proof (ZKP) integration lets bridges prove something is true without showing all the details, making crosschain communication more secure.
- Blockchain oracle solutions feed outside data into smart contracts; these oracles make sure every detail matches across different networks.
- Decentralized models spread out the power to lock, verify, and unlock assets so no single person or group can take over the process.
- Some trust-based bridges rely on well-known entities or companies who control checks but this setup faces centralization risks as seen in some hacks.
- Trustless protocols let users depend on code and math instead of people, using automated systems for validation and asset transfer across blockchain infrastructure.
- Hybrid approaches mix both human checks and automatic tools; this aims to balance speed with strong risk management for multichain networks.
- Security-focused bridges such as zkBridge use advanced cryptography to cut down vulnerabilities found in earlier models, helping blockchain stay safer from hacking events.
Types of Cross-Chain Bridges
You can spot different cross-chain bridges out there, and understanding the difference is vital for your security strategy. Each works in its own way, offering a different balance of speed, cost, and safety.
Trust-based bridges
Trust-based bridges use trusted parties, like companies or groups of people, to manage asset transfers between different blockchains. They lock digital assets on one network and release them on another after checking the request.
A classic example is BitGo, which acts as the custodian for WBTC. You trust them to keep the Bitcoin safe. Since these bridges rely on a small group to control funds, they face centralization risks. Hackers have targeted them before and stolen large amounts.
Some trust-based bridges make transfers fast and are simple for users because you do not need special skills or knowledge. Still, if the trusted party fails or gets attacked, all connected user assets are at risk. These security risks create a big challenge as more people want safe ways to move tokens between networks while using multichain infrastructure for their digital assets.
Trustless bridges
Trustless bridges use smart contracts and advanced protocols instead of a central party. This approach lets blockchains talk to each other without giving control to one group or company. Smart contracts lock, verify, and unlock assets during transfer steps on both sides.
One of the most innovative examples is Hop Protocol, which uses a system of “Bonders” to create liquidity across chains without a central authority. These systems lower the risks of hacking or theft tied to central control.
Many trustless bridges now rely on multi-signature wallets and blockchain oracle solutions for extra safety. For example, security-focused models like zkBridge add another layer using Zero-Knowledge Proofs (ZKP). Each step in these bridges runs with clear rules that anyone can check. Developers build them to protect users from losing digital assets worth millions, as seen in recent hacks where billions were stolen across bridge attacks.
Hybrid bridges
Hybrid bridges use both trust-based and trustless methods. They try to balance speed, security, and cost. For example, a hybrid bridge might rely on a group of trusted parties for some steps while also using smart contracts or blockchain oracle solutions to check transactions.
Axelar is a great example of this evolution, providing a decentralized network of validators that functions like a “proof-of-stake” bridge. These bridges help lower centralization risks that come with only one model.
| Bridge Type | Best For | Primary Risk |
|---|---|---|
| Trust-Based | Institutions needing compliance | Centralized failure or censorship |
| Trustless | DeFi natives seeking security | Smart contract bugs |
| Hybrid | General users wanting speed | Complexity of system |
Teams build them to improve cybersecurity since hacks have stolen over $2 billion from crosschain systems. Hybrid models often use multi-signature wallets or newer tools like Zero-Knowledge Proofs. These features give users more control over asset transfer between networks and make the process safer for everyone who moves digital assets across blockchains.
Challenges of Cross-Chain Bridges
Cross-chain bridges face many safety hurdles, especially with digital asset transfers. These weak spots can attract hackers and put your assets at risk.
Centralization risks
Centralization risks show up when one person or group controls a cross-chain bridge. If this happens, hackers have an easier target and can steal large amounts of digital assets. Chainalysis found that bridges remain a primary target, with nearly $3.5 billion stolen in 2025 crypto crimes, a large portion from infrastructure vulnerabilities.
A single point of control makes it simpler for attackers to break through all layers at once. Decentralizing how tasks like locking, verifying, and unlocking happen in asset transfer helps avoid these dangers. Many new security protocols use multi-signature wallets or smart contracts to split control between several parties instead of just one. This approach builds trust and protects users during multichain transactions across networks.
Smart contract vulnerabilities
Smart contracts run cross-chain bridges. Hackers look for weak points in this code. Vulnerabilities appear when the smart contract does not handle assets or data transfers safely. A famous example is the Nomad bridge hack, where a simple code update allowed users to drain $190 million by copying a valid transaction.
Cross-chain interoperability brings big risks if these digital agreements are not secure. A small bug can let someone steal all locked funds, causing huge losses and shaking trust in blockchain asset transfer. Strong security protocols must get built into every bridge to help block attacks and protect users’ digital assets as they move between different networks.
Scalability concerns
Cross-chain bridges handle many asset transfers at once. As more people use blockchain, these bridges can slow down or get overloaded. Sometimes they cannot keep up with fast growth.
During busy times, networks get clogged and transactions take longer to finish. This isn’t just an annoyance; it causes “slippage,” where the value of your asset changes before it arrives. In 2025, Chainalysis reported significant theft figures, showing that as bridges grow bigger and busier, security risks also rise fast.
Developers must find ways to help bridges process lots of trades while staying safe from hackers. Making sure these tools scale well helps protect digital assets across blockchains and supports trust in multichain systems like DeFi and token swaps.
Innovations Making Cross-Chain Bridges Safer
Safer cross-chain bridges now use smarter tech to stop hackers. New ideas help protect your digital assets and build trust for asset transfers, turning what was once a gamble into a reliable tool.
Zero-Knowledge Proof (ZKP) integration
Zero-Knowledge Proof (ZKP) lets users prove they have certain data without showing the data itself. In cross-chain bridges, this keeps private information safe during asset transfer and verification steps.
Polyhedra Network is leading this charge with their zkBridge, which uses ZK proofs to verify block headers between chains. This means the bridge doesn’t need to “trust” a third party; it uses math to verify the transfer happened. Security risks drop because ZKPs do not reveal details that hackers could target.
Developers use ZKP to avoid centralization in bridge protocols. This means no single group controls the transactions or sees user secrets. As blockchain hacks grow, using ZKP adds much-needed protection for digital assets and makes interoperability safer for everyone.
Multi-signature wallets
Multi-signature wallets add a layer of security to cross-chain bridges. These wallets need more than one private key to approve any asset transfer. This means hackers cannot steal funds by cracking just one password or key.
For example, if a wallet uses three signers, at least two must agree before assets move. This approach helps avoid centralization risks found in other setups. Decentralizing the “locking” and “unlocking” steps in transactions makes attacks harder and keeps users’ digital assets safer.
Many new blockchain projects now use multi-signature wallets to protect against big hacks like those that led to billions stolen from bridges. Multi-signature technology builds trust for everyone using cross-chain solutions in cryptocurrency infrastructure and DeFi protocols.
Blockchain oracle solutions
Blockchain oracle solutions connect blockchains to real-world data. They help bridges check the truth of a transaction. Oracles feed crosschain systems with outside information, making smart contracts trustable and safer for asset transfer.
Chainlink’s Proof of Reserve (PoR) is a game-changer here. It allows a bridge to automatically verify that the assets it claims to have are actually in the vault before minting any new tokens. If the reserves drop, the bridge pauses automatically.
- Automated Checks: Oracles monitor collateral in real-time.
- Circuit Breakers: Transfers stop instantly if data looks suspicious.
- Decentralized Data: No single source of truth that can be manipulated.
These tools fight security risks in multichain setups by stopping false claims and hacks. Some new oracles use advanced math proofs like Zero-Knowledge Proofs (ZKP) to show data is correct without showing everything about it.
Security-focused bridge models like zkBridge
New bridge models like zkBridge use Zero-Knowledge Proofs to boost security. These proofs let a system show that a transaction is real without sharing all the details. Hackers stole over $2 billion from cross-chain bridges in recent years, so stronger cybersecurity methods are needed.
Bridges such as zkBridge fix many old weaknesses by removing single points of failure and limiting how much any one party controls. Decentralized validation with zero-knowledge tech means hackers face greater challenges if they try to break in. This helps stop big hacks seen before and builds more trust for users who want safe asset transfer between blockchains.
Benefits of Secure Cross-Chain Bridges
Safe cross-chain bridges give people confidence to move assets across different blockchains. These upgrades shape how users trust and grow in digital finance.
Improved security and user trust
Cross-chain bridges once faced huge security risks. Chainalysis reports show that billions in cryptocurrency were stolen in recent years. Today, smart contract upgrades and new validation tools like zero-knowledge proofs help close these gaps.
Multi-signature wallets make it harder for hackers to break in. Teams are also using blockchain oracle solutions to check transactions from many sources before they approve an asset transfer. These steps mean users worry less about losing their digital assets on crosschain platforms. Stronger cybersecurity practices build real trust with people who send tokens between blockchains.
Cost-effective and efficient asset transfer
Secure cross-chain bridges keep blockchain transactions fast and cheap. People can move digital assets from one blockchain to another without paying high fees or waiting a long time. For many users, this means they save both time and money.
New standards like ERC-7683, developed by Uniswap and Across, are making this even better by standardizing “intents.” This allows a competitive market of fillers to complete your trade instantly for the lowest fee, rather than you waiting for a slow bridge transaction.
| Method | Speed | Cost Efficiency |
|---|---|---|
| Legacy Bridges | 10-30 Minutes | High (Gas fees on both chains) |
| Intent-Based | Seconds | Low (Fillers compete on price) |
This lets traders and businesses jump between networks with ease. Moving cryptocurrencies like Ethereum or Bitcoin across different blockchains is now much simpler. The safer asset transfer also reduces worries about hacks that have cost billions in losses according to Chainalysis data from recent years.
Facilitating widespread Web3 adoption
Cross-chain bridges let users move digital assets between different blockchains. This opens the door for more people to try Web3 tools and apps. Better interoperability means new users can use many blockchain services without extra steps or worries about being stuck on one network.
Safer bridge designs, like those using zero-knowledge proof integration or multi-signature wallets, help stop attacks. These safety steps increase trust and make it easier for anyone to join multichain ecosystems. Now, users can transfer tokens and enjoy decentralized finance without fearing huge security risks or hacks.
Final Thoughts
Interoperability bridges have evolved from risky experiments into the secure highways of the crypto economy. With innovations like Chainlink’s CCIP and Circle’s CCTP, we are finally seeing a system where safety doesn’t come at the expense of speed.
The shift toward “Chain Abstraction” means that soon, you might not even know you’re using a bridge at all—it will just work. For anyone serious about digital assets, sticking to protocols that use these verified, audited, and decentralized methods is the only way to navigate the market confidently.
Stay curious and always verify your tools—smart choices today are the foundation of your financial wellness tomorrow.