For decades, the password was the gatekeeper of our digital lives. Then came the fingerprint scanner—a convenient, albeit imperfect, upgrade. But as we step into 2026, the era of static authentication is effectively over. In a world where AI can clone voices in seconds and 3D printers can replicate fingerprints, “touching a sensor” is no longer enough to prove you are you.
We have entered the age of invisible, continuous security. In 2026, biometric authentication is not a single event that happens when you unlock your phone; it is a fluid, ongoing process that occurs in the background. Your devices now recognize you by how you walk, how you type, and even the unique rhythm of your heartbeat. This shift is driven by necessity: the rise of generative AI and deepfake technology has rendered older biometric methods vulnerable, forcing a migration toward multi-modal and behavioral systems.
This guide explores the cutting-edge biometric landscape of 2026, analyzing the technologies replacing the fingerprint, the rise of “zero-trust” environments, and the critical balance between seamless convenience and ironclad privacy.
Why Fingerprint Authentication Is No Longer Enough
While fingerprint scanners remain common on budget devices, they have lost their status as the “gold standard” of high-assurance security. By 2026, the limitations of single-factor touch authentication have become undeniable hurdles for enterprises and security-conscious consumers.
Limitations of Fingerprint Biometrics
The primary failing of traditional fingerprint scanners is that they rely on static credentials. Once a hacker has a copy of your fingerprint data, that credential is compromised forever—you cannot change your fingerprint like you can a password.
- Spoofing Risks: High-resolution photography and 3D printing have made “presentation attacks” (using a fake finger) alarmingly easy.
- Physical Contact: The post-pandemic world retains a strong preference for touchless interfaces. Public fingerprint scanners are increasingly viewed as hygiene risks.
- Environmental Failure: Moisture, dirt, or even a small cut on a finger can still result in a “False Rejection,” locking legitimate users out of their own devices during critical moments.
Rising Threat Landscape in 2026
The threat landscape has evolved faster than hardware. The commoditization of Generative AI means cybercriminals no longer need Hollywood-level budgets to bypass security.
- AI-Assisted Duplication: AI tools can now reconstruct partial fingerprints from photos found on social media, creating synthetic prints that fool older capacitive sensors.
- The “Injection” Attack: Sophisticated attackers in 2026 don’t just hold a fake finger up to a camera; they use software to “inject” fake biometric data directly into the authentication stream, bypassing the sensor entirely.
- Need for Continuous Auth: A fingerprint check only validates the user at the start of a session. If a device is unlocked and then stolen while active, the security is void. 2026 security models demand continuous authentication—verifying the user every second they are using the device.
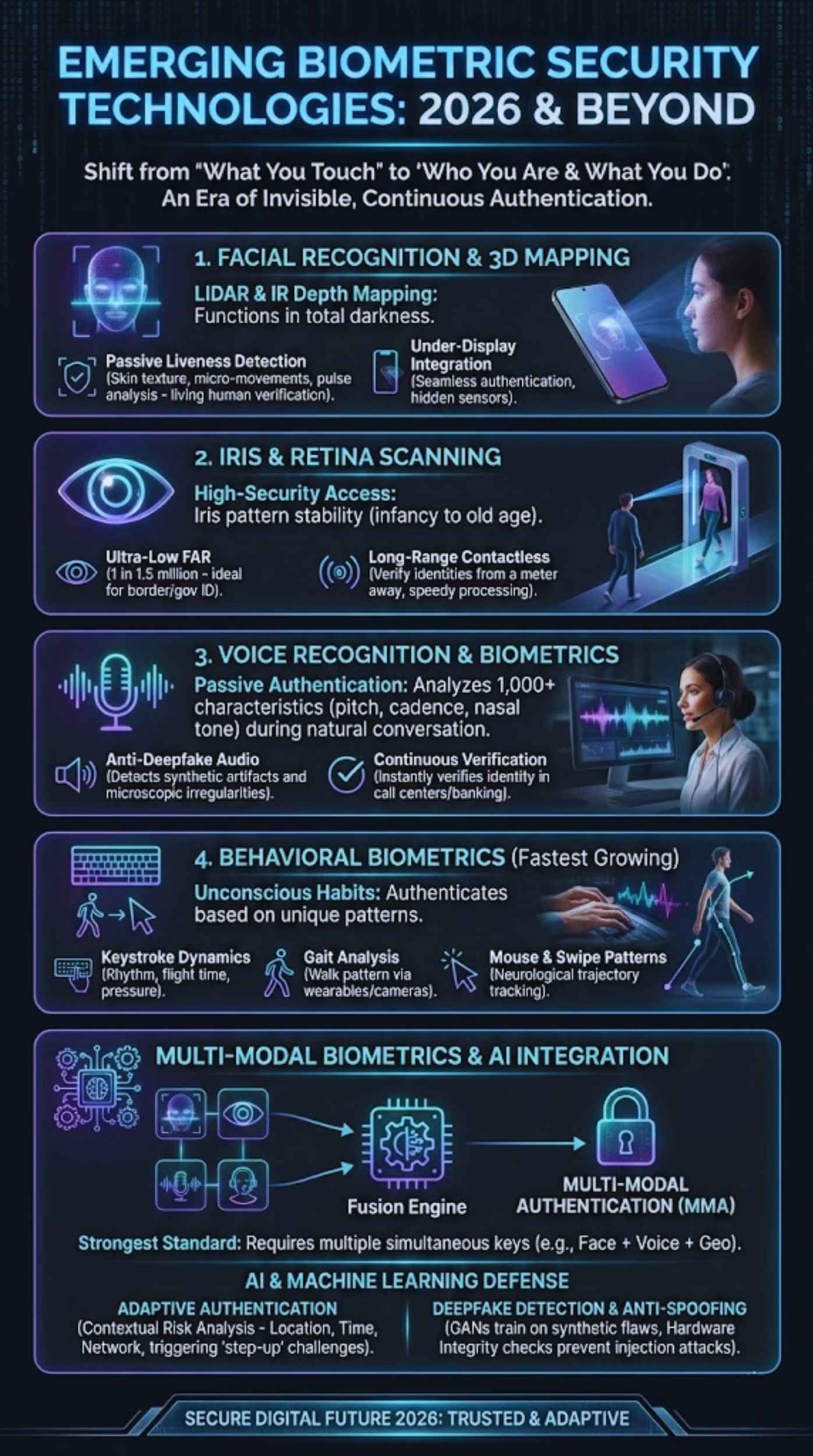
Emerging Biometric Technologies Shaping Security in 2026
The focus has shifted from “what you touch” to “who you are” and “what you do.” The following technologies are dominating the security market in 2026.
Facial Recognition and 3D Face Mapping
Gone are the days of 2D photo matching. Modern facial recognition utilizes LIDAR and infrared depth mapping to create a mathematical model of the face that functions in total darkness.
- Liveness Detection: The defining feature of 2026 facial tech is “Passive Liveness.” The system analyzes skin texture, micro-movements (like the pulse in your forehead), and light reflection to ensure it is looking at a living human, not a 3D mask or a high-res screen.
- Under-Display Integration: Cameras and sensors are now routinely hidden under the screen, allowing for seamless authentication without notches or cutouts.
Iris and Retina Scanning
While often confused, these are distinct technologies. Iris scanning (analyzing the colored ring of the eye) has become the preferred method for high-security access control in 2026 due to its stability—your iris pattern remains virtually unchanged from infancy to old age.
- False Acceptance Rate (FAR): Iris scanning boasts one of the lowest FARs in the industry (often 1 in 1.5 million), making it ideal for border control and government ID systems.
- Contactless Capabilities: New long-range scanners can verify identities from a meter away, speeding up lines at airports and secure facilities.
Voice Recognition and Voice Biometrics
Voice security has moved beyond “active” passphrases (e.g., “My voice is my password”).
- Passive Authentication: In 2026, call centers and banking apps use passive voice biometrics. The system analyzes over 1,000 unique vocal characteristics—pitch, cadence, nasal tone—during natural conversation to verify identity instantly.
- Anti-Deepfake Audio: Advanced algorithms now look for “synthetic artifacts” in audio waves—microscopic irregularities left behind by AI voice cloners—to distinguish between a human and a deepfake bot.
Behavioral Biometrics
This is the fastest-growing sector in 2026. Behavioral biometrics authenticate users based on unconscious habits.
- Keystroke Dynamics: The rhythm, flight time between keys, and pressure you use when typing are unique. If a hacker steals your password but types it with a different rhythm, access is denied.
- Gait Analysis: Wearables and smart cameras can identify you by your walk. This is particularly useful for smartphone security; if the phone detects a walking pattern that doesn’t match the owner, it locks automatically.
- Mouse & Swipe Patterns: How you scroll through a feed or move your mouse follows a specific neurological trajectory that is difficult to mimic.
Multi-Modal Biometrics
The strongest security standard in 2026 is Multi-Modal Authentication (MMA). Instead of relying on one lock, MMA requires multiple keys simultaneously.
- Example: A banking app might require a Face Scan (Who you are) + Voice Phrase (What you sound like) + Geolocation (Where you are) to authorize a large transfer.
- Fusion Engines: These systems use AI to weigh the “confidence score” of each factor. If facial lighting is poor, the system might rely more heavily on voice and behavioral signals to grant access.
AI and Machine Learning in Next-Gen Biometric Security
Artificial Intelligence is both the sword and the shield in 2026. While hackers use AI to attack, defenders use it to create smarter, adaptive locks.
Adaptive Authentication Systems
Security is no longer binary (Open/Closed). It is contextual. AI algorithms analyze risk in real-time to determine how much friction to apply.
- Scenario A: You are at home (trusted location), on your usual Wi-Fi, at 8:00 PM. The system may lower its guard, allowing face unlock alone.
- Scenario B: You are in a foreign country, on public Wi-Fi, at 3:00 AM. The AI detects high risk and triggers a “step-up” challenge, demanding a voice scan or a hardware security key in addition to face recognition.
Deepfake Detection and Anti-Spoofing
As generative AI videos become indistinguishable from reality to the human eye, biometric systems have deployed Generative Adversarial Networks (GANs) for defense.
- The Arms Race: Security vendors train their AI on millions of deepfakes to learn the subtle flaws of synthetic media.
- Injection Attack Prevention: New standards verify the integrity of the camera hardware itself, ensuring the video feed is coming directly from the lens and hasn’t been intercepted or replaced by software.
Real-World Applications of Advanced Biometrics
Biometrics have moved out of the spy movie and into the grocery store, the hospital, and the airport.
Consumer Devices and Smart Homes
- Smartphones: Devices now use “intent-based” security. The phone unlocks when you look at it with the intent to use it, distinguishing between a glance and an active gaze.
- IoT Security: Smart locks and cars are abandoning keys. Your car recognizes you as you approach (gait/face) and adjusts the seat and mirrors to your profile before you even open the door.
Banking, Fintech, and Digital Payments
- FIDO2 & Passkeys: The “Passkey” revolution is complete. Users no longer type passwords for banking; they authenticate via a biometric token stored on their phone.
- Naked Payments: In select innovative retail zones, “pay-by-face” or “pay-by-palm” is reality. You walk in, grab items, and a combination of cameras and sensors charges your account biometrically as you leave.
Healthcare and Identity Verification
- Patient Safety: Hospitals use biometrics to match patients to records instantly, preventing medication errors. Unconscious patients can be identified via iris or fingerprint scans to access life-saving allergy data.
- Remote Access: Doctors prescribing controlled substances remotely use behavioral biometrics to prove they are the ones issuing the script, preventing credential sharing or theft.
Travel, Airports, and Border Security
- The Seamless Journey: “E-Gates” have replaced manual passport checks in major hubs. A traveler creates a “Single Token ID” (face + passport data) before leaving home. From curb to gate, cameras recognize the face, opening doors and boarding bridges without the traveler ever removing a passport from their bag.
Privacy, Ethics, and Data Security Challenges
The convenience of 2026 comes with a heavy question: Who owns your face?
Biometric Data Protection
The storage model has shifted from “Centralized” to “Decentralized.”
- On-Device Processing: To prevent massive data breaches, reputable companies now store biometric templates locally in a Secure Enclave (a dedicated chip on the device). The server never receives your fingerprint; it only receives a cryptographic “Yes/No” token confirming the match.
- Cancelable Biometrics: A new area of research involves distorting biometric data (hashing) before storage. If the data is stolen, it is a useless string of code that cannot be reverse-engineered into a picture of your face.
Regulatory Landscape in 2026
- AI Act & GDPR: Europe and parts of the US have strict laws requiring explicit consent for biometric capture. “Shadow profiling” (scanning faces in public without consent) is heavily fined.
- Right to Erasure: Users have the legal right to demand their biometric templates be permanently deleted from corporate servers.
Ethical Risks and Bias
- Algorithmic Bias: Historically, facial recognition struggled with darker skin tones and diverse facial structures. In 2026, regulatory compliance requires algorithms to be tested on diverse datasets to ensure equal accuracy for all demographics.
- Surveillance Creep: The tension between safety and privacy remains. While biometrics stop crime, privacy advocates warn of the “panopticon” effect where citizens are tracked continuously in public spaces.
What the Future Holds for Biometric Security Beyond 2026
As we look toward the latter half of the decade, the concept of “logging in” will disappear entirely.
- DNA and Heartbeat: Portable DNA sequencers and ECG (heartbeat) sensors are shrinking. Future wearables might authenticate you by your unique cardiac rhythm or perspiration markers.
- Zero-Trust Integration: Biometrics will be the engine of Zero Trust Architecture. No user or device is trusted by default. Trust is earned continuously, second by second, through behavioral verification.
- Decentralized Identity (Web3): Users will hold their own “Self-Sovereign Identity” wallets. You will verify your age to a website using a cryptographic proof without ever revealing your name, birthdate, or face to the vendor.
The future of security is not about building higher walls; it is about building smarter gates—ones that open seamlessly for you, and stay firmly shut for everyone else.
Final Thoughts: The New Era of Trust
As we navigate 2026, the transition from simple fingerprint scans to complex, AI-driven behavioral and multi-modal biometrics represents more than just a technological upgrade—it is a fundamental shift in how we define identity. We are moving away from a model where you have to prove who you are by stopping and performing an action, to a model where the technology simply knows who you are by how you interact with the world.
This evolution brings unparalleled convenience and security, effectively neutralizing many of the threats that plagued the digital landscape of the early 2020s. However, it also places an immense responsibility on organizations to handle this intimate data with the highest ethical standards. The winners in this new era will not just be those with the most advanced algorithms, but those who can implement “invisible security” while maintaining visible trust.
For consumers and businesses alike, the message is clear: The password is dead, and the fingerprint is retiring. The future of security is fluid, continuous, and undeniably human.