Microsoft confirmed on Tuesday that several China-linked hacking groups have been exploiting critical vulnerabilities in its SharePoint Server, a popular on-premises collaboration platform used by enterprises and government agencies worldwide. The attacks began in early July and have targeted numerous high-value systems, raising global concern over the growing cybersecurity risks tied to nation-state cyber operations.
The hacking activity, which Microsoft attributes to three distinct Chinese threat actors, has prompted urgent patch rollouts, government alerts, and increased scrutiny over Microsoft’s global security infrastructure.
Who Is Behind the Attack?
Microsoft has identified three China-based groups actively exploiting the vulnerability:
-
Linen Typhoon (APT27) – A nation-state group long associated with cyber-espionage and targeting of government and corporate networks.
-
Violet Typhoon (APT31) – Another advanced persistent threat (APT) actor with a history of operations focused on intelligence gathering.
-
Storm-2603 – A less-known but highly active group originating from China, also involved in the current exploit wave.
All three actors are believed to have worked independently or in parallel to take advantage of a zero-day vulnerability affecting multiple SharePoint versions. These groups are known for sophisticated intrusion methods and stealthy persistence techniques, often leveraging stolen credentials and legitimate system tools to evade detection.
Timeline of the Attacks
The earliest evidence of exploitation traces back to July 7, 2025, when Microsoft’s threat intelligence teams first detected irregular behavior linked to SharePoint Server deployments. The attackers reportedly focused on on-premises SharePoint installations, not the cloud-based Microsoft 365 versions. Exploits occurred against:
-
SharePoint Server 2016
-
SharePoint Server 2019
-
SharePoint Subscription Edition
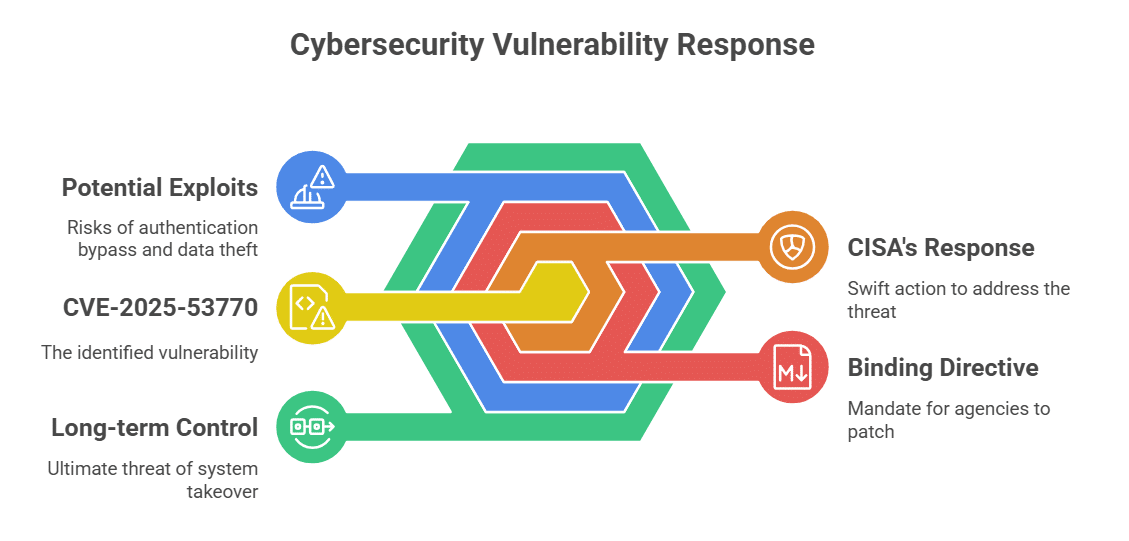
Initially, the attackers used a previously disclosed exploit chain known as ToolShell, which was made public in May 2025. They adapted this known technique to exploit two new vulnerabilities—later catalogued as CVE-2025-53770 and CVE-2025-53771—allowing remote code execution and unauthorized access.
How the Exploit Works
The attackers leveraged these vulnerabilities to upload malicious payloads—most notably, a custom web shell named spinstall0.aspx—onto SharePoint servers. Once installed, the web shell allowed attackers to execute arbitrary code and extract sensitive data.
Crucially, the attackers focused on accessing and exfiltrating ASP.NET machine keys used by SharePoint. These cryptographic keys are vital in authenticating users and applications. By stealing them, the attackers could forge authentication tokens, granting themselves administrative access without triggering alerts.
Even systems configured in load-balanced environments were vulnerable, as the machine keys are often shared across multiple servers. This allowed persistent, distributed access and made mitigation more challenging.
In more advanced cases, threat actors also deployed in-memory modules that did not leave any trace on the hard drive. These stealthy tactics bypassed traditional antivirus tools and made incident response far more complex.
A Growing List of Victims
Although the full extent of the breach is still under investigation, cybersecurity consultants and Microsoft’s own threat intelligence suggest that at least 50 organizations have been impacted. These include:
-
U.S. federal agencies
-
Military subcontractors
-
Energy sector firms
-
Educational institutions
-
Several state and local government entities
Security teams discovered that some compromised SharePoint instances were being used as launchpads for lateral movement, enabling attackers to pivot into email systems, internal databases, and critical enterprise applications.
Organizations running outdated or unpatched SharePoint versions were especially vulnerable. In several cases, forensic analysis found evidence of data tampering, credentials harvesting, and deployment of secondary malware loaders.
Microsoft’s Response: Patches and Recommendations
Microsoft responded by releasing emergency patches:
-
Patches for SharePoint Server 2016 and 2019 were released on Sunday, July 21
-
A patch for SharePoint Subscription Edition followed on Monday, July 22
In addition to the patches, Microsoft urged all organizations using on-premises SharePoint to:
-
Immediately apply the latest updates
-
Rotate all cryptographic machine keys and authentication tokens
-
Check logs and files for evidence of web shells and unauthorized access
-
Deploy endpoint detection tools capable of identifying in-memory threats
Microsoft emphasized that simply patching the system is not enough. Once machine keys are compromised, attackers can maintain access even if the software is updated. Key rotation and forensic reviews are essential to ensure complete remediation.
U.S. Government Agencies Take Action
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) responded swiftly by adding CVE-2025-53770 to its Known Exploited Vulnerabilities (KEV) catalog. CISA also issued a binding operational directive requiring all federal civilian agencies to patch the vulnerability by July 24, 2025.
The directive was based on evidence that multiple federal networks were already compromised before patches were available. CISA warned that this exploit could allow attackers to bypass authentication, steal sensitive documents, or gain long-term control over internal systems.
Security Experts Raise Alarms
Cybersecurity firms such as Mandiant, now owned by Google, assessed that at least one of the groups exploiting the vulnerability had direct ties to China’s intelligence apparatus. While Microsoft did not name the Chinese government as being directly responsible, security experts widely consider these groups to operate with at least implicit support from state agencies.
This latest incident follows a series of breaches involving Chinese actors targeting Microsoft technologies. In 2021, the Hafnium group (also China-linked) exploited vulnerabilities in Microsoft Exchange Server, gaining access to email communications in thousands of networks globally. More recently, Microsoft faced backlash after Chinese hackers breached U.S. government email accounts in 2023—a failure that drew criticism from federal oversight bodies.
Internal Security Measures at Microsoft Under Scrutiny
The SharePoint exploit comes at a time when Microsoft is under growing pressure to improve its internal security operations. In early July, the company announced that it would no longer rely on engineers based in China for certain sensitive work, including Pentagon-related cloud services. This decision followed media reports suggesting that global infrastructure supported by Chinese personnel could present supply chain and insider threats to U.S. national security.
Microsoft CEO Satya Nadella previously committed to making cybersecurity a top company priority, especially after critical government reports questioned the company’s handling of past attacks.
Despite this pledge, the current incident raises questions about Microsoft’s vulnerability response timelines, incident communication, and the reliance on legacy on-premise software still widely deployed in enterprise environments.
Urgent Recommendations for Organizations
Security experts are advising all organizations running SharePoint to treat this vulnerability as a severe and active threat. Recommended actions include:
-
Apply Microsoft’s latest security updates immediately.
-
Conduct a full audit of machine keys and security tokens.
-
Inspect for web shells like
spinstall0.aspxand delete them. -
Run memory analysis tools to detect hidden modules.
-
Isolate compromised servers from the network until they are fully cleaned.
-
Engage professional cybersecurity teams to conduct forensic investigations.
Organizations should also consider accelerating migration from legacy on-premise systems to cloud-based, actively managed solutions where patching and monitoring are more streamlined.
A Wake-Up Call for Enterprise Security
The exploitation of Microsoft SharePoint by Chinese hacking groups illustrates the ongoing challenge of securing critical infrastructure software. As threat actors become more advanced, vulnerabilities in enterprise platforms like SharePoint represent high-value targets for espionage, intellectual property theft, and data manipulation.
This incident reinforces the urgent need for proactive patching, zero-trust architecture, and continuous threat monitoring. For both private and public organizations, the attacks serve as a stark reminder that security is only as strong as the weakest link in the digital chain.
As investigations continue and the list of victims grows, Microsoft and its customers face a difficult period of response, recovery, and restructuring of their cybersecurity strategies.