You worry every log leak could bite your network. Many teams watch their all-in-one platforms like hawks. But Thejavasea.me Leaks Aio-tlp370 spilled 1.2GB of source code from a code repository, chat app, and forum on March 22, 2025.
That zip file, called aio-tlpfullv7.3.zip, held exploitable logic and cloud API flags.
In this post, you will learn to audit files, rotate passwords, and enable multi-factor authentication. We will also cover how to tighten network defense with a monitoring tool and a sound incident response plan that meets cybersecurity best practices.
Read on.
Key Takeaways
- On March 22, 2025, Thejavasea.me leaked aio-tlpfullv7.3.zip, 1.2 GB of source code and logs.
- The leak exposed hardcoded API keys, cloud flags, config files, and over 2,000 secrets in 24 hours.
- Attackers can use Splunk to scan logs for weak credentials and find new exploits.
- Firms must audit systems, rotate passwords and API tokens, and enable two-factor authentication fast.
- Apply patches within 48 hours, segment networks, deploy a SIEM, and test an incident response plan.
What Is Thejavasea. me Leaks AIO-TLP370?
Thejavasea.me Leaks Aio-tlp370 info in a large data leak on March 22, 2025. That group posted a 1.2GB file called aio-tlpfullv7.3.zip on a dark web board. This bundle aims at enterprise monitoring and data processing.
The package automates log collection from software, network, and system levels. Such a setup helps firms comply with GDPR.
Cybercriminals will mine that archive for credentials and payload code. Log analysis platform Splunk can sift through vast records fast. Security software layers and a password manager will block basic hacks.
We will now examine the main attributes of the AIO-TLP370 leak.
Key Features of the AIO-TLP370 Leak
Thejavasea.me Leaks Aio-tlp370 dumps system logs from cloud infrastructure and tunnel nodes into a single pool. Criminals scan remote control channels, sniff weak credentials in real time, and map new paths for exploits.
Consolidated Log Processing
IT teams feed Windows Event Log, syslog, application logs, and cloud service records into a SIEM platform. Security staff unify all streams and cut out fragmentation. Cybersecurity experts spot malware alerts and data breach signs faster.
They detect botnet or proxy threats in real time.
This setup ties in with search clusters, logging tools, antivirus, and risk management apps. It boosts efficiency in monitoring and data processing. Enterprises run scans and audits on a single pane.
It fits into existing networks, adding no extra steps.
Increased Vulnerability Exposure
Log processing flagged gaps after Thejavasea.me Leaks Aio-tlp370 leaks widened risk. Source code with exploitable algorithms leaked in open-source software. Attackers traced cloud services API flags in exposed config files.
Developer appendices spilled unresolved issues, aiding cybercrime ops. Internal incident response playbooks exposed traffic light protocol actions.
Cyberattack groups use leaked docs to plan network hacks on gaming computer setups. They adapt to exploit tools faster than security patches roll out. Teams must guard personal data and sensitive information in every domain.
They should tighten protocol rules, block credential stuffing, and encrypt API keys.
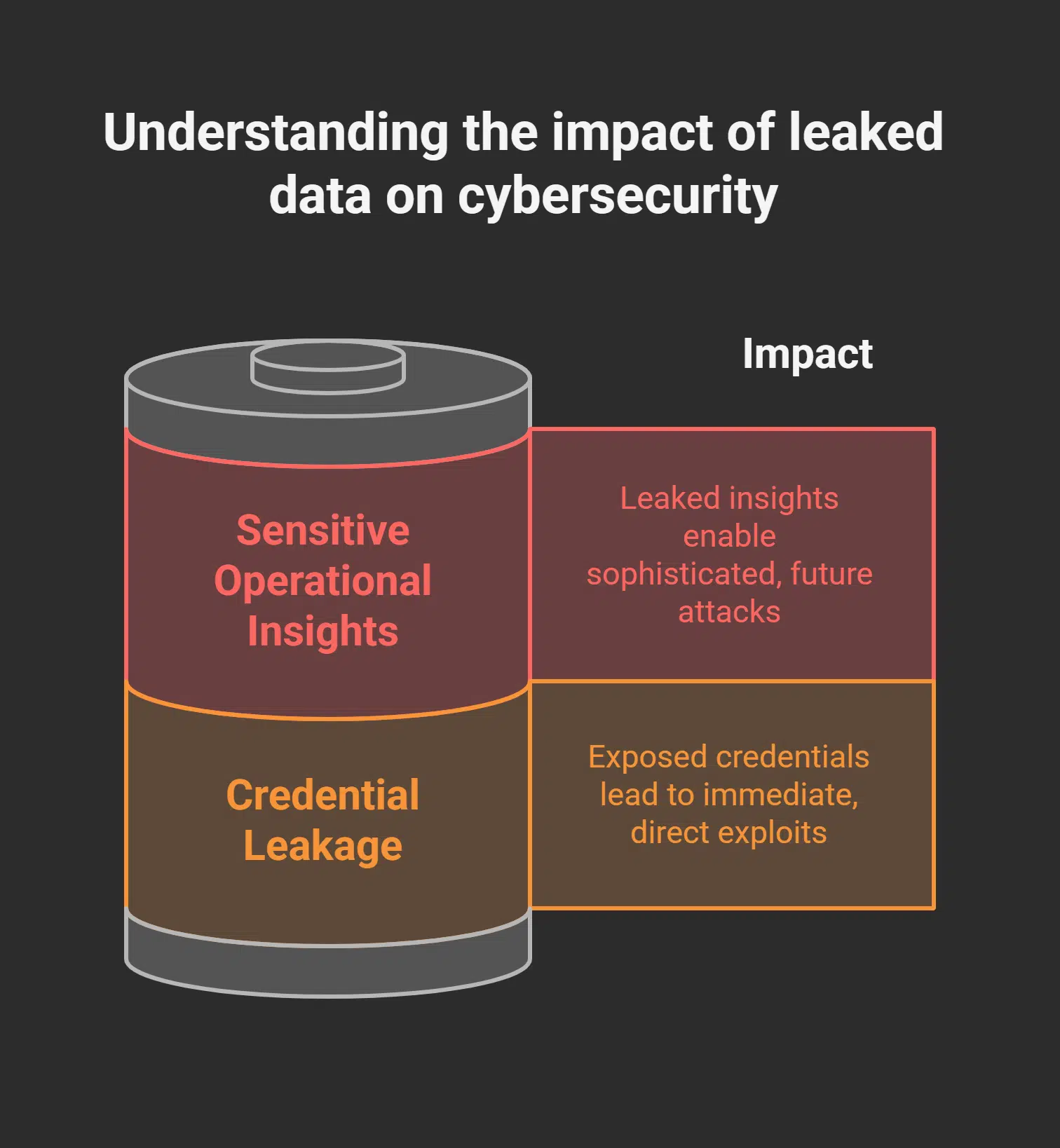
Impacts of the Leak on Cybersecurity
Hackers pick through spilled logs, tweak phishing pages, and crack weak 2FA layers. They even hand crypto-locking gangs fresh targets, while defenders drown in anti-malware alerts.
Credential Leakage
The leak on Thejavasea.me Leaks Aio-tlp370 exposed hardcoded API keys in configuration files for the AIO-TLP370. Enterprise backends and cloud dashboards felt serious risks. Exposed keys let bad actors break into remote desktop or Linux servers.
Data leaks here fuel credential stuffing attacks on databases. Attack tools then run automated scripts in seconds. This event spawns new computer security vulnerabilities. Malicious actors may spin up phishing page campaigns next.
GitHub repos can mirror exposed secrets in minutes. Security teams logged over 2,000 leaked keys within 24 hours.
Security teams must rotate all credentials right away. They need to rotate all credentials right away. Patching config files blocks future exploits. Teams also enforce two-factor authentication on enterprise services.
They set up zero-trust segments around web hosting and databases. They deploy anti-malware software on laptops and IoT devices. Developers follow Linux tutorials to strip hardcoded keys from code.
Cloud vendors apply encryption and network segmentation to APIs. Swift action cuts unauthorized access risks and halts supply chain attacks.
Sensitive Operational Insights
Developer notes on security layers showed each encryption phase. A shadow forum called StateWins hosted them for hours. Hackers studied that info to craft an exploit fast. Milestone roadmaps and performance benchmarks for AIO-TLP370 sat on a dark web marketplace.
Cyber watchers traced loading times, memory use, and node counts. That data helps them predict patch dates and tweak JavaScript attacks.
Internal incident response frameworks from January surfaced too. That blueprint broke down roles for threat analysis, containment, and cleanup. High-net-worth customers now face extra scrutiny over leaked playbooks.
Cybersecurity companies spot chatter in dark corners on e-commerce platforms and peer-to-peer channels. Ransomware groups could map each button press and voice call. That peek behind the curtain may fuel more cyberattacks soon.
How Businesses Should Respond
Check your device shield and tighten your firewall rules so you spot odd moves before they cause a mess. Then, run your security software updates and tweak the intrusion alarms so you keep hackers in the dark.
Conduct an Immediate Audit
Scan logs with computer security software, and you catch odd events fast. Use real-time protection with active detection to spot an exposed key or compromised activity. Identify leaked tokens on the internet or in emails after the recent thejavasea.me leak.
Rotate credentials; issue new API tokens with limited scopes. Patch any broken communication protocol or vulnerability (computer security) in your stack.
Monitor dark web marketplaces like cracked.io and nulled.io for sold data, even tags like “statewins private VIP nudes leaked.” Enable proactive notification so you get an email each time someone probes your network.
Ask your security hacker team for a swift update on any sign of an exploit (computer security) or spyware trace. Time to move on to enhance network defense.
Enhance Network Defense
With an audit in hand, you build stronger shields for your log-processing gear. You install a threat blocker, tweak network barrier rules, and add a secure tunnel for remote access.
You apply patches and updates promptly, within 48 hours of a Patch (computing) notice. You boost resilience in the tech world, and guard against sudden cyberwarfare.
You segment subnets, isolate exposed servers, and cut off lateral hacking. You tap into open-source boards, monitor community efforts on GitHub, and deploy an event tracker to spot odd traffic.
You test each setting in a sandbox lab. You safeguard logs and keep your system scalable for future growth.
Takeaways
Thejavasea.me Leaks Aio-tlp370 gave IT pros a real wake-up call. Version control hub chatter and cloud API flags spilled into the open. Teams plugged gaps in security platforms and network barriers.
They rotated passwords and beefed up encryption fast. Keep your network safe by staying alert and acting now.
FAQs on Thejavasea.me Leaks Aio-tlp370
1. What is the AIO-TLP370 leak on Thejavasea.me?
Well, it is a fresh leak on Thejavasea.me, it shows a new gadget called AIO-TLP370. It drops encrypted files, it hints at a blockchain twist, and it shakes up the technology world.
2. How does this leak change gaming laptops and PC reviews?
It adds new specs for gaming rigs and gaming laptops, and it feeds data for PC reviews. It can shift the classification of top rigs; reviewers must stay on their toes.
3. Can I find coding tutorials or SEO tips on the leak site?
Yes, the site still hosts coding tutorials, or you can browse through programming guides, and it has SEO tips to boost your pages.
4. Why does it say “JavaScript is disabled; please enable JavaScript in your browser before proceeding”?
If JavaScript is disabled, you will see that warning pop up; it tells you to please enable JavaScript and then reload your browser before proceeding. Thejavasea.me needs scripts to show the leak details.
5. What’s different between the AIO-TLP370 and AIO-TLP405 in terms of validity and ease of use?
The AIO-TLP405 is the next model; it has more valid specs, and it boosts ease of use. You still need vigilance, but this version feels smoother, and it packs clearer menus.