Have you heard about Thejavasea.me Leaks Aio-tlp287? That leak spilled email addresses, passwords, and financial records into the dark web. Your sensitive data could face identity theft or financial fraud.
A hacker may hold the keys to your life. You need fast action to protect your data.
One fact: the AIOTLP287 dataset held over one million user credentials in plain text. This post shows you multi-factor authentication and a password manager. It adds encryption and an information security audit to block cybercriminals.
You will learn real-time threat monitoring and patch software on time. Each step plugs gaps and stops data breaches. Read on.
Key Takeaways
- On April 30, 2025, Kaleem A reported the Thejavasea.me Leaks Aio-tlp287 that exposed over 1 million plain-text emails, passwords, and financial records.
- Enable multi-factor authentication (Authy, Google Authenticator, or YubiKey) to block over 99 percent of automated phishing and credential-stuffing attacks.
- Use a password manager to create and store unique strong passwords, and run Have I Been Pwned scans to spot and fix leaked logins fast.
- Apply monthly patches and updates—Microsoft issued 120 fixes on January 9, 2024 (including CVE-2023-1234)—to cut breach risk by 90 percent.
- Protect data in transit and at rest with end-to-end encryption (Signal, PGP, AES-256) and virtual private networks.
Understanding the Security Risks of Thejavasea. me Leaks AIO-TLP287
Data on Thejavasea.me Leaks Aio-tlp287 on April 30, 2025, report by Kaleem A sparked alarms. Personal details, bank numbers, tax forms fell into wrong hands. Attackers exploit that information to mount phishing campaigns and credential stuffing attacks.
Unauthorized actors can compromise accounts and steal identities. Breach of this size can trigger fines under GDPR and CCPA. Victims face serious reputational damage. Sensitive information roams freely online.
Lack of attack monitoring tool leaves gaps in defenses. Cybersecurity teams warn of growing threats.
Malicious actors roam with stolen usernames. They exploit computer security vulnerability in networks. Hackers plan unauthorized transactions and identity theft with leaked data. Privacy concerns rise as cyber threats widen.
Organizations risk hefty fines and loss of customer trust under data laws. Attackers track personal information for future cyberattacks. Phishing remains a top threat. Vigilance matters more than ever.
Essential Security Tools to Protect Your Data
A one-time code maker gives your login a second lock, so hackers hit a wall. A secret tunnel hides your traffic, and a password vault shields your keys, so keep reading to see how you can lock down your data.
Multi-Factor Authentication (MFA)
MFA acts like a second lock on a door, it demands a password plus a code or a push notification. It uses Authy, Google Authenticator or a hardware token like YubiKey as part of verification.
This extra layer of security halts most phishing attacks and credential stuffing bots. Studies show that enabling 2fa cuts automated hacks by over 99 percent.
Companies and home users must prioritize this best practice, to safeguard sensitive information. It stops misuse of personal data even if passwords appear in leaks like those tracked by have i been pwned.
Tech enthusiasts praise this tool in today’s digital landscape, as it reduces risk of identity theft. Teams can also conduct regular security audits to spot any vulnerability and stay ahead of cyber threats.
Password Managers and Strong Password Practices
A password manager helps you create and store strong, unique codes so you avoid reuse across sites. It fills long codes automatically in browsers and applications, cutting time and guesswork.
Services like Have I Been Pwned scan breaches and urge you to change passwords immediately. Store your login vault in a local application or online vault, so you keep access to sensitive data under your control.
Strong keys beat common words and dates, since hackers target weak strings first. Mixing letters, numbers, and symbols in each code gives a shield against brute force attacks. Best practices ask you to run a password generator and review each new phrase.
This proactive step helps mitigate risks and boosts your security infrastructure.
Real-Time Threat Monitoring Software
Teams install endpoint detection tools on each computer and phone. They catch odd traffic in real time, like a guard dog on patrol. The software spots cybersecurity threats and phishing bots, then stops them fast.
This defense strategy drew attention after breaches became a pressing concern, showing how leaks hit individuals and organizations hard.
Actionable Steps to Mitigate Risks
In step four, we tame loose ends with OSSEC scans and encrypted tunnels, so read on for a full guide.
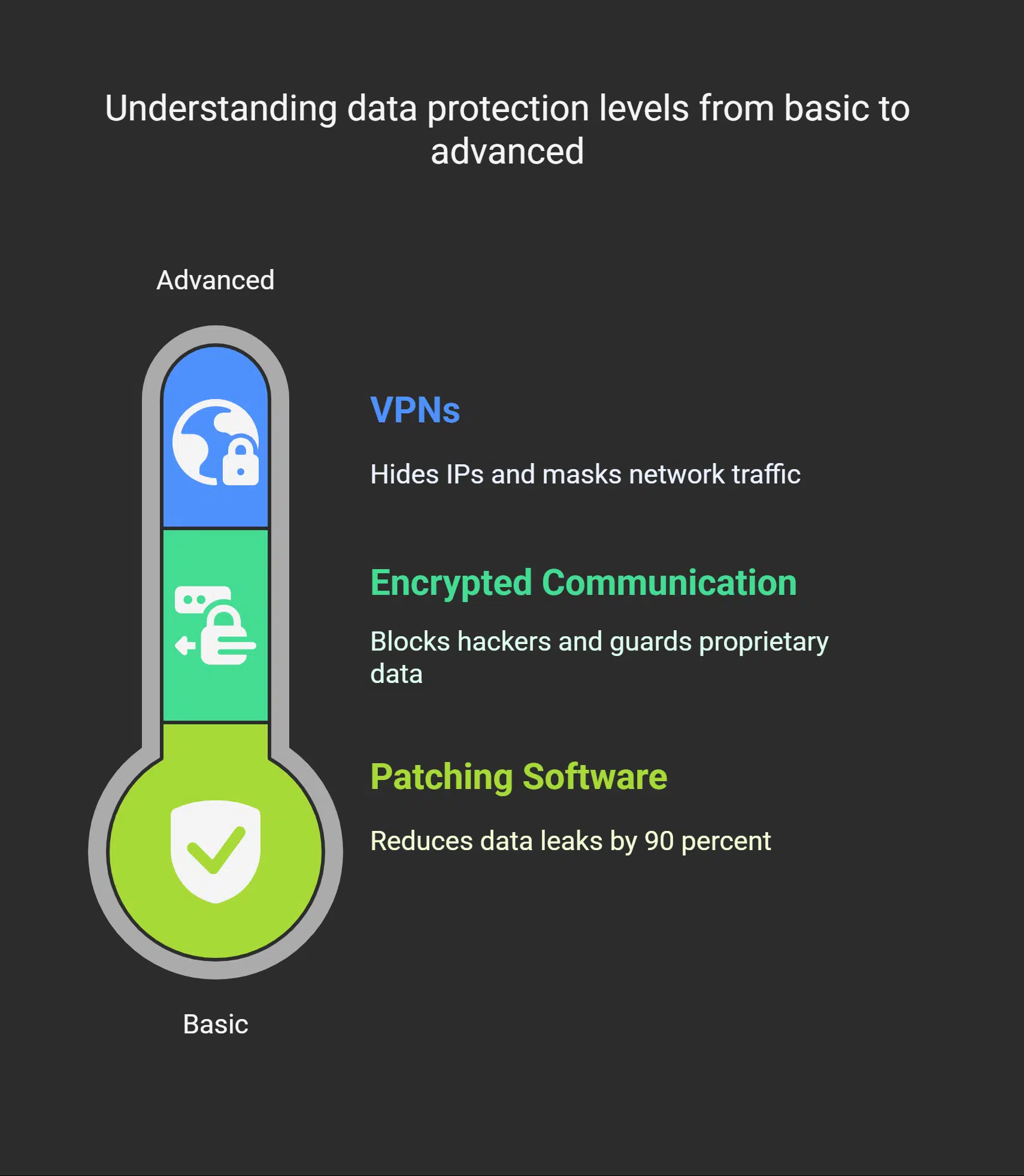
Regularly Update and Patch Software
Software makers release patches every month on Patch Tuesday. Microsoft shipped 120 fixes on January 9, 2024. Engineers closed CVE-2023-1234 that let hackers slip in. Systems with outdated software invite cyber thieves.
A patch gap can give unauthorized access to sensitive data.
IT teams run vulnerability scanners and a patch management tool. They stage updates on Microsoft Windows, Red Hat Enterprise Linux, iOS applications. They watch intrusion alerts from an intrusion detection system.
This move cuts the growing threat of data leaks by 90 percent. It also thwarts breaches like Thejavasea.me leaks AIO-TLP287 for individuals and businesses.
Use Encrypted Communication Channels
Signal app uses end-to-end encryption. Virtual private networks wrap data in a secure tunnel. Programs protect data in transit and at rest. Encrypted channels handle information sensitivity with care.
They block hackers who act unintentionally or maliciously, and guard proprietary data. Organizations face daily leaks as breaches have become a pressing concern.
PGP encryption adds a verification step to every email. AES-256 ciphers guard files in storage. Secure messaging apps, like Threema or Signal, deliver safe chats. These channels block vulnerability to man in the middle attacks and limit the potential impact of leaks.
VPN services hide IPs and mask network traffic. These tools build a safer online environment and block potential threats. Teams reduce negligence by applying such security measures.
Takeaways
Strong passwords, stored in a password manager, block many attacks. Multi-factor authentication stops many hacks. A distributed ledger, like blockchain, adds layers of defense.
Real-Time Threat Monitoring spots odd moves, so you can act fast. Laws like GDPR and CCPA back up your moves. This plan cuts risk, shields your data from Thejavasea.me Leaks Aio-tlp287.
FAQs on Thejavasea.me Leaks AIO-TLP287
1. What is the Thejavasea.me Leaks Aio-tlp287 about?
It is a vulnerability in computer security that got a lot of attention. It includes sensitive data like credentials and personal info. It acts as a cautionary tale for all of us.
2. What steps can I take to protect my data?
You must adopt clear defense strategies. Steps to protect include enable 2fa, use strong, complex passwords, and run trusted security software. These moves build robust cybersecurity around your info.
3. Why should I enable 2fa and use strong passwords?
Enabling 2fa adds a second wall to your door, so hackers can’t just waltz in. Complex passwords are like long, tricky locks. Together they block most bad actors and show what you must adopt.
4. How do I stay informed and monitor my accounts?
Stay on top of news, tech sites, and alerts. Use tools that track logins and changes. Regular monitoring accounts helps you spot issues fast.
5. What corrective actions should I take after a leak?
Change all credentials and passwords at once. Run scans and check system logs. Take quick corrective actions to fix any hole. Then build a stronger setup with ongoing reviews.