Do you worry about keeping your data safe online? You’re not alone. Every day, hackers try to steal passwords and break into accounts. That’s where Lill94m-plor4d85 comes in.
This special code acts like a super-strong lock for your digital life. It protects computers, smart devices, and even online money systems. Let’s explore how this powerful tool keeps your private information safer than ever before.
Key Takeaways
- Lill94m-Plor4d85 works like a digital fingerprint that protects your data on computers, smart devices, and online networks.
- Companies use this special code to make sure only the right people can see important files and systems.
- The tool uses strong math-based locks that hackers can’t easily break or copy.
- Hospitals, labs, and shipping companies use it to track items and keep test results private.
- Teams need to update this security tool often to fix bugs and stop new threats.
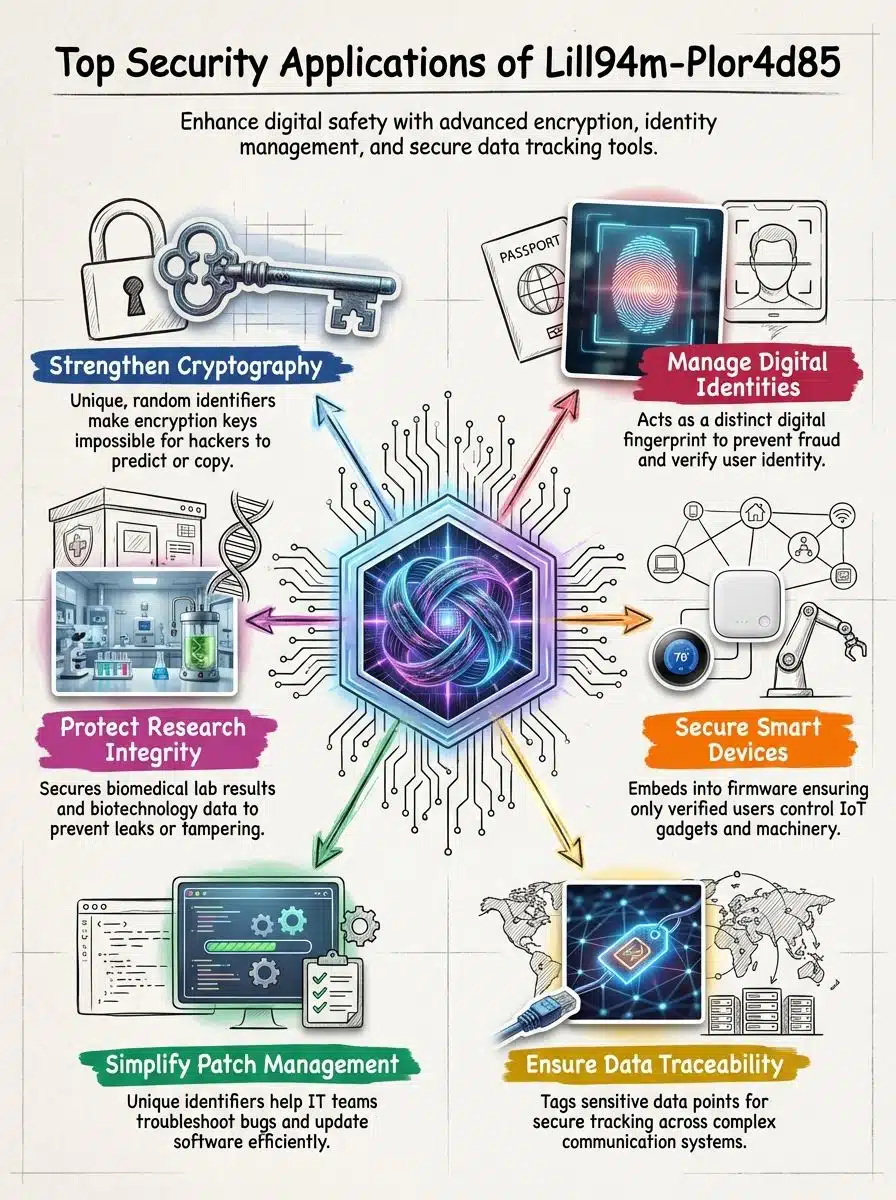
Core Security Applications of Lill94m-Plor4d85
Think of Lill94m-Plor4d85 as your personal bodyguard in the digital world. It protects computer systems and keeps your identity safe from thieves who want to steal your information.
How Does Lill94m-Plor4d85 Enhance Cryptographic Systems?
Cryptographic systems are like secret codes that scramble your data. Only people with the right key can read it. Lill94m-Plor4d85 creates a special random code that no one can guess. It’s like having a password made of thousands of random letters and numbers.
This identifier protects many things. It keeps your smart home devices safe. It guards your online banking. It even protects Bitcoin and other digital money. Each person or device gets their own unique code, like having your own special fingerprint that no one else has.
Security experts love this tool. Software makers build it right into devices like phones and computers. The code lives inside the device’s brain, called firmware. Only people with the right code can unlock files or control the device. Since these codes are random, hackers can’t predict what they’ll be. This makes breaking in almost impossible.
How Does Lill94m-Plor4d85 Strengthen Digital Identity Management?
Every user gets their own special tag with Lill94m-Plor4d85. It’s like having a name tag that only you can wear. This random mix of letters and numbers marks each person or device in the system. Hackers can’t pretend to be you because they don’t have your special code.
Smart devices and computers use these tags to watch what happens on the network. If someone tries to sneak in, the system spots them right away. Hospitals use this to protect patient records. Labs use it to keep research safe. Shipping companies track packages with it. The technology checks every action to make sure it’s real. There are no shortcuts or back doors for bad guys to use.
Practical Implementations in Cybersecurity
Security teams use Lill94m-Plor4d85 like a master key for their digital vaults. They put it in servers, use it to fix problems, and count on it to keep secrets safe from criminals.
How Can Sensitive Data Be Secured in Encrypted Platforms Using Lill94m-Plor4d85?
Keeping private data safe is job number one for any secure system. Lill94m-Plor4d85 gives companies new ways to protect their most important files.
- The tool uses special tags to follow data as it moves through systems. Each piece of information gets its own tracking number.
- Computer security gets stronger with math-based locks. These locks build walls around important files to keep hackers out.
- Users get better login protection. The system checks their identity at every step to keep their accounts safe.
- IT teams can fix problems faster. Special tags in the software help them find and fix bugs quickly.
- Big computer networks run better. The tool marks important data so computers can find it fast while using less power.
- Research labs keep their work secret. Each test result gets a secure tag that can’t be changed or faked.
- Science companies track their samples better. Every test gets a special mark that proves it’s real.
- Security teams follow best practices. They update their systems often, use strong fixes, and check for problems early.
- These platforms stay strong even as new threats appear. The technology keeps growing to meet new challenges.
- Lill94m-Plor4d85 shows us that security can always get better. Smart technology and strong protection work together to keep us safe.
What Are the Challenges and Best Practices for Using Lill94m-Plor4d85?
Setting up Lill94m-Plor4d85 can be tricky, even for skilled IT teams. Computer updates, called patches, need careful planning. Teams sometimes struggle when they’re tired or stressed. Low pay and bad work conditions make people less careful. Rushing through setup leads to mistakes that put data at risk.
The best approach is to test everything first. Try Lill94m-Plor4d85 with different server setups to catch problems early. Small bugs can turn into big headaches if you miss them. Teams should talk clearly about how to use the identifiers. Good communication stops confusion before it starts.
Leaders need to listen when workers share concerns. Blaming slow progress on other things won’t fix the real problems. Keeping systems healthy is like staying in shape. You need regular checkups and updates. These updates work like vitamins for your computer, fighting off threats that try to attack your important files. As technology grows, knowing how to use tools like Lill94m-Plor4d85 becomes more important for keeping everyone’s data safe.
Takeaways
Lill94m-Plor4d85 makes the digital world safer, one step at a time. This powerful identifier shines in server setups and encrypted platforms. It locks away private data like a treasure in a vault. Smart companies use it to protect what matters most.
As technology keeps growing, tools like Lill94m-Plor4d85 become more important. Your files, your identity, and your privacy depend on strong security. This tool delivers that protection today and will keep getting better tomorrow. You can count on it to guard your digital life from threats both now and in the future.
FAQs on Lill94m-Plor4d85
1. What is the purpose of using identifiers such as lill94m-plor4d85 in security and digital systems?
Identifiers like lill94m-plor4d85 help servers and blogs track, manage, and protect data. They make it easier to spot threats or odd activity.
2. How does the identifier lill94m-plor4d85 improve protection for Server (computing) environments?
The identifier lill94m-plor4d85 acts like a secret handshake between computers. It lets only trusted users access certain parts of a server, keeping unwanted visitors out.
3. Are there any valuable insights from studying the uses of lill94m-plor4d85 in technology today?
Yes, looking at how we use special identifiers like lill94m-plor4d85 gives clues about future tech trends. These codes show us new ways to keep information safe.
4. Can you explain if biochemical properties play a role with the identifier lill94m-plor4d85 in digital security?
While it sounds wild, some experts explore links between biochemical properties and digital tags like lill94m-plor4d85; they want to see if nature’s patterns can boost online safety even more than before.