Hey there, are you worried about keeping your website safe from sneaky cyber threats like data breaches or unauthorized access? Here’s a key fact, cloud security tools are vital for protecting your data and apps from nasty attacks.
In this blog, we’ll show you 10 awesome cloud-native security tools that can guard your site with ease. Stick around, let’s explore!
Key Takeaways
- Wiz protects over 5 million workloads and scans 230 billion files daily, making it a top choice for cloud security.
- Prisma Cloud by Palo Alto Networks offers multi-cloud protection with Zero Trust security for hybrid setups.
- Orca Security uses agentless scanning with SideScanning tech to spot risks fast in cloud workloads.
- Aqua Security focuses on container safety, securing Kubernetes setups against cyber threats.
- Lacework uses machine learning for automated threat detection, catching odd behavior in real-time.
Wiz: Comprehensive Cloud Security Management
Got a website running in the cloud? Then you need top-notch protection, and Wiz steps up to the plate with awesome cloud security management. It guards over 5 million workloads, showing just how big its reach is.
Plus, it scans a mind-blowing 230 billion files every single day. That’s like having a super guard dog sniffing out trouble before it even gets close to your cloud infrastructure.
Now, imagine your site as a giant castle in the sky. Wiz acts like the sharpest lookout, spotting risks and fixing gaps in your cloud platform fast. It’s trusted by half of the Fortune 100 companies, proving it’s a heavy hitter in threat detection and data security.
Stick with Wiz, and keep those cyber threats at bay without breaking a sweat.
Prisma Cloud by Palo Alto Networks: Multi-Cloud Protection
Prisma Cloud by Palo Alto Networks stands out as a top choice for guarding your cloud setups. It works across different cloud platforms, keeping your data safe no matter where it lives.
Imagine it as a watchful guard dog, always on duty to sniff out cyber threats in hybrid cloud environments. With its sharp focus on Zero Trust security, it makes sure only the right folks get access.
Plus, it offers runtime protection to stop issues before they grow big.
Have a multi-cloud setup? No sweat, Prisma Cloud has your back with strong tools for threat detection and data protection. It keeps an eye on regulatory compliance too, helping you avoid costly slipups.
Think of it like a trusty sidekick, always monitoring for sneaky risks. Stick with this tool, and you’ll sleep better knowing your cloud infrastructure is under tight watch.
Orca Security: Agentless Security for Cloud Workloads
Hey there, let’s chat about Orca Security, a game-changer for protecting your cloud workloads. This tool offers agentless scanning, so you don’t need to install anything on your systems.
That means less hassle and quicker setup for your cloud infrastructure. With Orca, you get instant cloud visibility to spot risks right away. It’s like having a watchdog that never sleeps, keeping an eye on your cloud services.
Guess what else? Orca Security uses patented SideScanning technology to dig deep into your cloud setup. This helps catch security vulnerabilities and cyber threats without slowing things down.
If you’re managing cloud-native applications, their method is a breath of fresh air. It keeps your data protection tight, guarding against data breaches in a snap. Stick with this for top-notch threat detection!
Trend Micro Cloud One: Integrated Security Services
Trend Micro Cloud One is a powerful tool for protecting your cloud setups. It brings together various security services into one neat package. Think of it as a Swiss Army knife for your cloud infrastructure, tackling multiple threats at once.
This tool guards your workloads, containers, and even file storage with ease.
Got a complex cloud system? No sweat. Trend Micro Cloud One offers runtime protection to spot and stop cyber threats in real time. It works across different cloud providers, keeping your data safe from malware and data breaches.
Stick with this, and you’ve got a solid shield for your cloud-native applications.
Aqua Security: Advanced Container and Cloud-Native Protection
Aqua Security emerges as a leading force in protecting your cloud environments, particularly for those using containerized applications. This solution is dedicated to fortifying Kubernetes setups, ensuring your systems remain secure from cyber threats.
If you’re using containers, Aqua provides strong defense against data breaches and hidden attacks. It acts as a reliable protector for your digital space, always vigilant.
Now, let’s discuss why this is significant for you. Aqua thoroughly examines container security, identifying vulnerabilities before they turn into major issues. It integrates seamlessly with cloud-native applications, maintaining workload security across various platforms.
Additionally, it supports adherence to regulatory standards, so you don’t have to worry about compliance or penalties. Stay with this, and see your cloud infrastructure gain a sturdy barrier against potential dangers.
Sysdig: Runtime Security for Kubernetes and Cloud Environments
Sysdig offers top-notch runtime security for your Kubernetes and cloud setups, folks. It keeps a sharp eye on cloud-native applications, spotting cyber threats as they happen. Think of it as a watchful guard dog, always ready to bark at intruders sneaking into your cloud infrastructure.
Got containers or serverless functions? Sysdig protects them with real-time threat detection. It also helps with incident response, so you can act fast if something goes wrong. Plus, it works smoothly with CI/CD pipelines, making sure your software development stays safe without slowing down.
Stick with this tool, and watch your cloud environments stay secure!
Check Point CloudGuard: Unified Cloud and Network Security
Check Point CloudGuard stands out as a solid pick for protecting your cloud setups and networks. It mixes cloud security with network defense, making sure your data stays safe across platforms.
Think of it like a trusty guard dog, always watching over your digital yard. With tools for threat prevention and policy enforcement, it helps block cyber threats before they sneak in.
This solution also shines in giving you clear cloud visibility. It works across hybrid cloud setups, keeping an eye on everything from Google Cloud Platform to other environments. Plus, it tackles shadow IT, so no sneaky apps slip through.
Stick with CloudGuard, and you’ve got a strong shield against data breaches and more.
Lacework: Automated Threat Detection and Compliance
Hey there, readers, let’s chat about Lacework, a top player in cloud-native security. This tool shines with its automated threat detection, keeping your cloud setups safe from sneaky cyber threats.
It uses smart tech like machine learning to spot odd behavior fast. Got a weird login or data access issue? Lacework catches it before trouble brews.
Also, it helps with regulatory compliance, making sure your site follows the rules without a headache. Think of it as a watchful guard, scanning for risks in real-time across your cloud infrastructure.
Whether you’re on AWS or Google Cloud Platform, Lacework offers clear visibility and quick fixes for vulnerability management. Stick with this, and watch those data breaches stay far away!
Microsoft Defender for Cloud: Built-In Security for Azure Workloads
Got a site running on Azure? Microsoft Defender for Cloud is your go-to buddy for keeping things safe. It’s built right into the Azure platform, so you don’t need extra tools or tricky setups.
This gem watches over your cloud workloads, spotting cyber threats before they hit. With real-time threat detection, it acts fast to guard your data and apps.
Think of it like a watchdog for your cloud infrastructure. It also helps with vulnerability management, pointing out weak spots you can fix. Plus, it ties into compliance frameworks, making sure your site meets rules without the headache.
Stick with this, and your Azure setup stays locked down tight.
SentinelOne Singularity Cloud: AI-Powered Threat Prevention
Hey there, folks, let’s chat about SentinelOne Singularity Cloud, a top-notch player in cloud security. This tool uses AI-powered threat detection to spot cyber threats before they wreak havoc.
Imagine it as a digital watchdog, always sniffing out danger in your cloud infrastructure. It’s sharp, fast, and keeps your data safe from sneaky attacks.
What’s cool is how it offers risk prioritization, helping you tackle the biggest issues first. Plus, with secret scanning, it hunts down hidden vulnerabilities in your setup. Think of it as a treasure map, pointing straight to the weak spots in your cloud-native applications.
Stick with this, and you’ve got a solid shield against data breaches.
Key Features to Consider When Choosing Cloud-Native Security Tools
Let’s talk about keeping your site safe in the cloud. Picking the right cloud-native security tools can feel like finding a needle in a haystack, but I’m here to help!
- Full Cloud Visibility: You need a tool that shows every corner of your cloud infrastructure. Think of it as a map for your digital world. Without this, you’re flying blind, and stats show that by 2029, 60% of businesses lacking a unified CNAPP will face big cloud visibility challenges. Tools like Wiz and Prisma Cloud by Palo Alto Networks shine here, spotting risks across multi-cloud setups.
- Automated Threat Detection: Speed matters when cyber threats strike. Go for tools using machine learning for real-time threat detection. This cuts down risks fast, slashing security incidents by up to 50% with automation. Lacework and Microsoft Defender for Cloud excel at catching odd behavior before it’s a problem.
- Strong Compliance Support: Staying on the right side of rules like GDPR or HIPAA is a must. Pick tools with automated compliance checks to match regulatory frameworks. This saves time and keeps data breaches, which cost an average of $4.88 million globally in 2024, from hitting harder. Check Point CloudGuard helps enforce policies with ease.
- Container and Workload Safety: If you run cloud-native applications, securing containers is key. Look for container security features to guard Kubernetes or Docker setups. Aqua Security and Sysdig offer runtime protection, keeping workloads safe from sneaky attacks in hybrid cloud spaces.
- Identity and Access Control: Who gets in matters a ton. Tools with solid identity and access management stop unauthorized entry cold. This ties into zero trust architecture, a must-have for cloud access safety. Orca Security nails this with agentless scans to lock down access controls.
- Data Loss Prevention Skills: Losing data stings, especially with costs soaring to $9.36 million per breach in the U.S. in 2024. Choose tools with data loss prevention (DLP) to shield sensitive info. Trend Micro Cloud One blocks data leakage across your cloud computing setup.
- Integration with CI/CD Pipelines: Your development shouldn’t slow down for security. Find tools that plug into CI/CD pipelines for smooth vulnerability scanning. This keeps your cloud-native apps secure from the start. SentinelOne Singularity Cloud uses AI to spot issues early in the build process.
- Cloud Security Posture Management (CSPM): A good CSPM feature spots missteps in your cloud setup before they bite. It’s like having a watchdog for your infrastructure as code. This helps avoid pricey errors, and tools like Prisma Cloud lead the pack in risk prioritization.
- Support for Multi-Cloud Environments: If you use AWS, Azure, or Google Cloud Platform (GCP), you need broad coverage. Select tools that protect across all platforms without gaps. Microsoft Defender for Cloud ties seamlessly with Azure, while others like Wiz handle hybrid cloud setups well.
- Incident Response Speed: When trouble hits, quick action saves the day. Opt for tools with sharp incident response and threat intelligence baked in. This keeps downtime low and recovery fast. Cloud Detection and Response (CDR) in tools like Lacework makes a big difference.
Best Practices for Deploying Cloud-Native Security Solutions
Hey there, let’s chat about keeping your cloud safe. Deploying cloud-native security solutions the right way can save you from cyber threats and headaches.
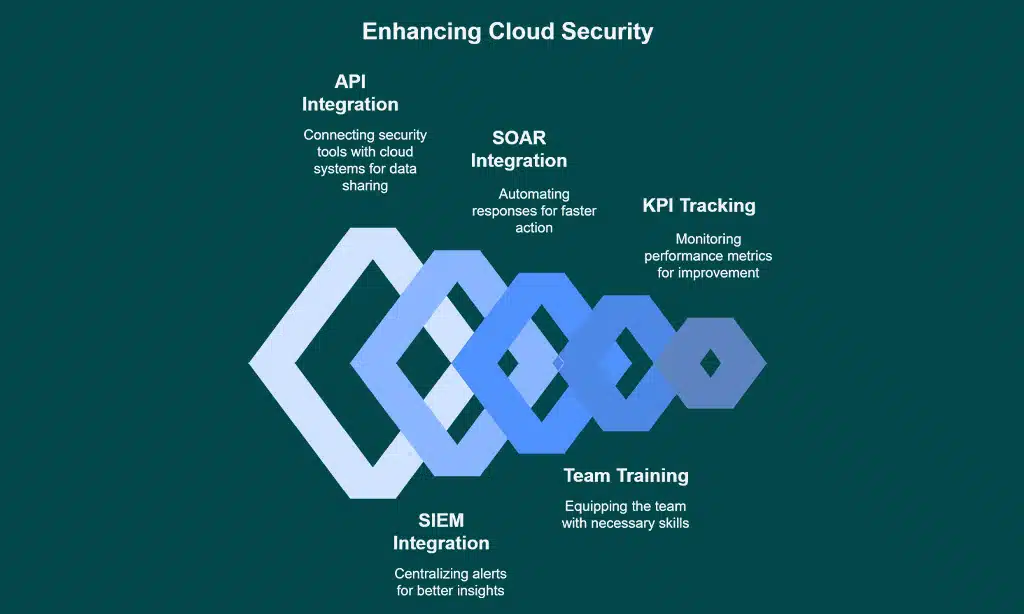
- Start by blending these tools with your cloud platforms like Google Cloud Platform (GCP) or Azure. This means making sure your security setup talks smoothly to your cloud infrastructure. It’s like having a good buddy who always has your back. When they sync up, you catch risks fast and keep data breaches at bay.
- Tap into APIs for tighter integration. APIs are like secret handshakes between your security tools and cloud systems. They help share info quick, so your threat detection stays sharp. This step keeps your cloud visibility high and stops shadow IT in its tracks.
- Hook up with SIEM systems for better insights. Security Information and Event Management (SIEM) tools gather all your alerts in one spot. Think of it as a control tower watching over your cloud computing setup. Connecting them means you spot cyber threats sooner and boost incident response.
- Link to SOAR platforms for speedy action. SOAR stands for Security Orchestration, Automation, and Response. It’s like having a superhero sidekick that automates fixes for issues. Pairing this with cloud-native security cuts down on manual work and ramps up real-time protection.
- Train your team to handle these tools well. Even the best cloud security posture management (CSPM) software flops without skilled users. Set up regular learning sessions on vulnerability management and policy enforcement. A sharp crew slashes mean time to resolve (MTTR) and keeps your site safe.
- Track success with clear KPIs like MTTR and alert coverage. These numbers show how fast you fix problems and how much of your cloud is watched. Picture it as a scorecard for your risk management game. Checking these often helps prove the worth of tools like Prisma Cloud or Microsoft Defender for Cloud.
- Focus on automation to lighten the load. Automating tasks in CI/CD pipelines or compliance checks saves time and cuts errors. It’s like setting up a robot to do the boring stuff. This lets your team tackle bigger threats and keeps workload security tight.
- Keep an eye on regulatory compliance at every step. Use tools like Check Point CloudGuard to match compliance frameworks. Think of it as following the rules of the road to avoid fines. Staying on top of this protects against data loss prevention (DLP) slips.
- Prioritize real-time threat detection over delayed scans. Waiting too long is like leaving your front door unlocked all night. Tools like Orca Security or Trend Micro Cloud One spot issues as they happen. This approach shields hybrid cloud setups from sneaky attacks.
- Test and tweak your setup often for top results. Treat your cloud-native application protection platform (CNAPP) like a car needing tune-ups. Regular checks with vulnerability scanning stop small glitches from becoming big messes. It keeps your data protection solid against evolving risks.
The Role of Automation in Cloud-Native Security
Automation plays a huge part in keeping your cloud-native setups safe. Think of it as a tireless guard dog, always sniffing out issues like data breaches or sneaky cyber threats. Tools with automation, such as cloud security posture management systems, cut down manual work by a ton.
They spot risks in your cloud infrastructure fast and fix them before trouble hits. Plus, they can shrink security incidents by up to 50% through sharp visibility and quick action.
On top of that, automation ties right into your workflows with SIEM and SOAR platforms. It’s like having a trusty sidekick that helps with threat detection and keeps you in line with regulatory compliance.
No more sweating over endless checklists; cloud-native application protection platforms handle the heavy lifting. So, you can focus on growing your site while staying safe from nasty surprises in the digital jungle.
How These Tools Enhance Site Protection and Compliance
Hey there, let’s chat about how cloud securityactual tools can be your site’s best buddy in staying safe and following the rules. Imagine your website as a house; these tools act like top-notch locks and alarms.
They shield your data from nasty stuff like unauthorized access and data breaches. Plus, they stop service interruptions that can mess up your day. With cyber threats lurking around every corner, tools like Prisma Cloud and Microsoft Defender for Cloud stand guard, keeping your cloud infrastructure secure.
It’s like having a watchdog that never sleeps, always ready to bark at intruders.
Now, think of compliance as a strict teacher checking your homework. Rules like GDPR, HIPAA, CCPA, SOC 2, and ISO 27001 aren’t just suggestions; ignoring them can lead to hefty penalties.
Cloud security tools help you ace this test by automating compliance tasks. They scan for weak spots in your setup and fix them fast. Whether it’s Aqua Security or Check Point CloudGuard, these helpers make sure your site meets every standard.
Even with open-source options, you get flexibility, though they need some know-how. Commercial picks, on the other hand, come with vendor support to guide you through the maze of regulatory compliance.
Takeaways
Wow, we’ve covered a lot of ground on cloud-native security tools! These solutions, like Wiz and Prisma Cloud, are your trusty sidekicks in guarding your site’s data. Don’t wait for a cyber threat to strike; pick the right tool now.
Imagine your cloud setup as a fortress, safe and sound. Let’s keep those digital walls strong together!
FAQs on Cloud-Native Security Tools
1. What are cloud-native security tools, and why do sites need them?
Hey, let’s break this down. Cloud-native security tools, like Prisma Cloud or Microsoft Defender for Cloud, guard your cloud infrastructure against cyber threats and data breaches. They’re vital for keeping cloud-native applications safe in today’s wild west of digital transformation.
2. How do tools like Aqua Security help with container security?
Listen up, container security is no small potatoes. Aqua Security steps in with runtime protection and vulnerability scanning to shield your CI/CD pipelines from nasty surprises.
3. Can cloud security posture management (CSPM) stop data loss?
Absolutely, CSPM is like a watchdog for your cloud setup. It sniffs out weak spots in your cloud security, helping with data loss prevention (DLP) and policy enforcement. Tools like Orca Security keep your cloud visibility sharp, so you’re not left in the dark.
4. What’s the deal with cloud access security brokers (CASB)?
Picture this, a gatekeeper for your cloud access. Cloud access security brokers (CASB), part of setups like Trend Micro Cloud One, monitor traffic and block shadow IT, keeping unauthorized access at bay.
5. How does artificial intelligence boost threat detection in cloud computing?
Alright, here’s the scoop. Artificial intelligence, paired with machine learning, powers real-time threat detection in platforms like Check Point CloudGuard. It’s like having a crystal ball, spotting cyber threats before they hit your hybrid cloud.
6. Why mix secure access service edge (SASE) with cloud-native application protection platforms (CNAPP)?
Hey, think of this as a dynamic duo. Secure access service edge (SASE) locks down connections, while a cloud-native application protection platform (CNAPP) uses behavioral analytics and automated compliance to fortify Google Cloud Platform (GCP) or other cloud infrastructures. Together, they tackle risk prioritization and incident response, keeping data protection tight as a drum.