You may worry that quantum computing could break your crypto, and that fear is real for many users. Quantum algorithms, like Shor’s algorithm, could crack elliptic curve cryptography and expose private keys and digital signatures, which would risk past and future transactions; nations, including China, run secretive work on quantum computers that makes the timeline hard to know.
The National Institute of Standards and Technology, NIST, is testing post-quantum cryptography to help protect public keys and key agreements.
This post shows seven clear ways quantum computing could hit crypto, from attacks on signatures to shifts in proof-of-work and proof-of-stake, and it covers Grover’s algorithm, quantum key distribution, hardware wallets, and lattice-based cryptography in plain terms.
You will get simple steps projects and users can take, plus what cryptographers and standards groups are doing. Read on.
Key Takeaways
- Shor’s algorithm can break RSA and elliptic-curve signatures, Grover cuts symmetric key strength, and “harvest now, decrypt later” drives urgent NIST post-quantum work.
- NIST began standardization after 2010 (competition 2016) and named FIPS 203–205 to standardize CRYSTALS‑Kyber, CRYSTALS‑Dilithium, and Sphincs+.
- Blockchains must adopt post-quantum algorithms, cryptographic agility, and hardware-wallet updates; Taproot and Schnorr buy time while QRL tests lattice-based schemes.
- Proof-of-work and proof-of-stake rely on signatures and face quantum risk; specialized miners aid PoW, but both need hybrid post-quantum schemes and larger symmetric keys.
- Public quantum computers lack enough qubits and error correction, so timelines remain uncertain; teams must test post-quantum cryptography, hybrid key exchange, and train staff.
Threat to Current Cryptographic Algorithms
Quantum computers, once they hit quantum supremacy, can run quantum algorithms that change how we solve hard math problems. Shor’s algorithm runs in polynomial time, it can factor large numbers and solve discrete logarithms, and that directly threatens RSA and elliptic curve cryptography.
Cryptocurrencies depend on SHA-256 hash function and ECDSA for public-key signing, so a break of private keys would put many digital assets at risk. Grover’s algorithm cuts the effective strength of symmetric cipher and cryptographic hash functions, which forces larger key-size for AES and similar systems.
Most systems rest on unsolved mathematical problems, so solving those problems would undermine existing encryption systems. Researchers warn of “Harvest Now, Decrypt Later” attacks, where adversaries store ciphertext today and decrypt it later with quantum computation.
Lattice-based cryptography and code-based cryptography form parts of post-quantum cryptography, and quantum key distribution (QKD) offers a physical route using quantum bits and quantum circuits.
Quantum gates and quantum circuits still face practical limits like qubit error rates and quantum error correction, so exact timelines for the quantum threat remain uncertain.
Vulnerability of Digital Signatures Across Blockchain Systems
Digital signatures guard most blockchains. They tie private keys to public addresses, and they prove who may move digital assets. Shor’s algorithm can solve prime factorization and discrete logarithms in polynomial time, and that breaks elliptic curve cryptography and many digital signature algorithms.
Bitcoin is moving from ECDSA to Schnorr scheme to raise cryptographic strength. If attackers run quantum computers that use Hadamard gate operations, they could derive private keys from public keys and fake signatures.
That threat hits proof-of-work and proof-of-stake networks, since both depend on signature math, so no chain gets a free pass.
Attackers might store old transaction data, and later use Shor’s algorithm to break recorded public keys. Such a collapse would let anyone execute transactions from any public key, and that would wipe out assumed wallet ownership.
Developers must upgrade digital signatures and key agreement protocols, and they should adopt post-quantum cryptography, like lattice-based cryptography or hash-based cryptography.
Grover’s algorithm can speed brute force on symmetric encryption, so teams will need larger key size, or new symmetric schemes. Hardware wallets add a layer of defense, but if the math falls to a quantum program, stored secrets lose their value.
Standards bodies, researchers, and node operators must add cryptographic agility, so chains can swap algorithms before past or future transactions lose privacy.
Breaking Past and Present Data Encryption
Attackers can store encrypted ledgers today under the “Harvest Now, Decrypt Later” tactic, like stashing loot for a rainy day. This move threatens secret keys, and it can undo privacy for past transactions.
Grover’s algorithm gives a square root speedup. Attackers could leverage that speed to cut effective key strength for symmetric ciphers. Elliptic curve cryptography, which secures most wallets, faces big risk from quantum algorithms that target discrete logs.
Secretive national programs, especially in China, add uncertainty about how soon attacks might arrive. The Bank for International Settlements published a report that analyzes quantum risks to classical finance, and it calls for assessments now.
Publicly accessible quantum computers cannot yet break encryption standards critical to cryptocurrencies. They lack enough physical qubits and robust error correction. Researchers now push post-quantum cryptography, like lattice-based cryptography, and they test BB84 protocol inspired methods for quantum-safe key exchange.
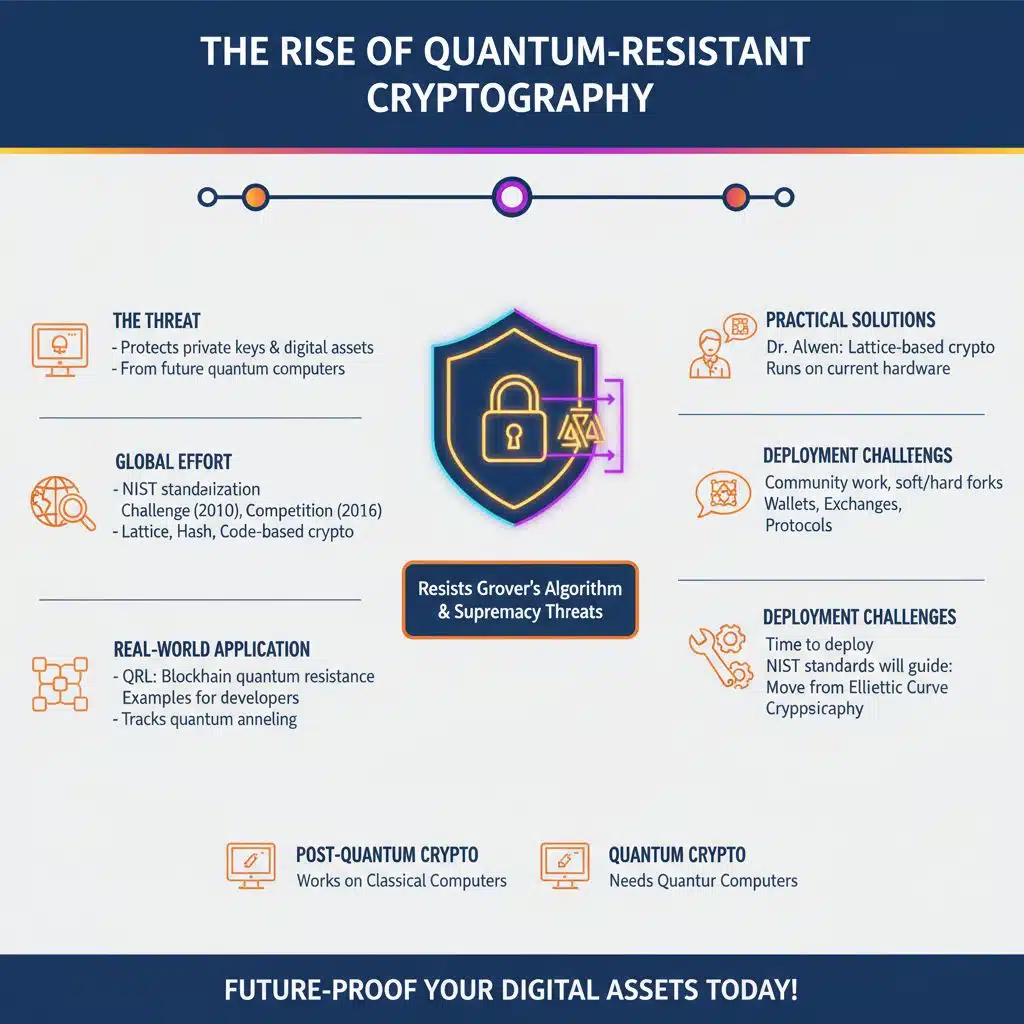
The Rise of Quantum-Resistant Cryptography
Post-quantum cryptography aims to protect private keys and digital assets from future quantum computers. NIST started a standardization process, after a challenge in 2010 and a global competition in 2016, to pick quantum-resistant public-key algorithms.
Researchers test lattice-based, hash-based, and code-based cryptography on classical machines, so systems can resist Grover’s algorithm, quantum supremacy threats, and other quantum algorithms.
Dr. Alwen has proposed lattice-based cryptography as a practical post-quantum solution.
Projects like Quantum Resistant Ledger (QRL) focus on blockchain quantum resistance, and they give real examples for developers to study, and researchers track quantum annealing too.
Post-quantum methods run on current hardware, and post-quantum encryption is feasible, but they need community work, soft or hard forks, and time to deploy. NIST will finish standards for public-key schemes, and those rules should guide wallets, exchanges, and protocols to move away from elliptic curve cryptography.
Some researchers study quantum cryptography that needs quantum computers, while post-quantum cryptography works on classical computers.
Evolution of Encryption Standards to Combat Quantum Threats
Quantum computing forces encryption change. NIST ran a long selection, it began with 69 candidate algorithms. Seven finalists and eight alternates remain. The agency named three first standards as FIPS 203, FIPS 204, and FIPS 205.
FIPS 203 covers CRYSTALS-Kyber, a lattice-based key encapsulation scheme. FIPS 204 standardizes CRYSTALS-Dilithium for digital signatures, also lattice-based. FIPS 205 pins down Sphincs+, a hash-based digital signature.
New math problems, like lattice problems and hash puzzles, form the base of post-quantum cryptography. These moves target threats from quantum computers, and quantum algorithms like Grover’s that can weaken key strength.
The transition will be gradual and complex. Experts expect new standards to roll out over at least a decade. Systems need cryptographic agility, modular designs that let teams swap algorithms fast.
That change will demand protocol updates, firmware patches, and staff training. MIT OpenCourseWare and Stanford online courses teach core cryptographic skills. Researchers publish open drafts on the Eprint server, anyone can read them.
Teams should test post-quantum cryptography and try lattice-based cryptography in lab settings. Small wins, like hybrid key exchange, buy time before full migration.
Potential Impact on Proof-of-Work and Proof-of-Stake Systems
PoW chains, running on ASIC miners, gain some protection from specialized hardware, but they still rely on digital signatures tied to private keys. Proof-of-Stake networks lack a hardware shield, and they also depend on elliptic curve cryptography for signing.
Both types face a real quantum threat from quantum computing if attackers use quantum algorithms to break signature schemes.
Hashing resists Grover’s algorithm better, yet ownership and authenticity of keys still worry custodians of stablecoins, CBDCs, deposit tokens, and identity solutions. Teams test lattice-based cryptography, post-quantum cryptography methods, upgradable cryptographic techniques, and hybrid security approaches to protect mission-critical ledgers.
Hardware wallets, protocol upgrades, and standards work can cut risk while researchers push for fast adoption.
Role of Hardware Wallets in Enhancing Security
Hardware wallets hold private keys offline, so hackers cannot grab them through the internet. Security experts call them the most secure storage for keys in classical settings, and they recommend cold storage for high-value digital assets.
Devices like a Ledger device or a Trezor device use a secure element and air-gapped setups, which block many types of cyberattacks. Quantum algorithms, including Grover’s algorithm, raise future concerns, yet that offline barrier keeps keys safer than hot wallets today.
Upgrading those devices for post-quantum cryptography may be hard because of firmware and hardware limits. Post-quantum approaches, such as lattice-based cryptography, will replace elliptic curve cryptography in some flows, and many devices will need deeper changes.
Owners will face a practical choice, apply firmware patches if available, or buy new hardware, like changing locks to match new keys.
Blockchain Adaptations for a Post-Quantum World
Blockchains must swap fragile math for hard math, fast. Bitcoin’s Taproot upgrade helps privacy, it hides differences between multi-signature and single-signature transactions. Taproot also aims to make opening Lightning Network channels indistinguishable from regular base layer transactions.
Researchers test quantum-resistant blockchain protocols, and some favor lattice-based cryptography for signatures. Projects build upgradable cryptographic modules, and they study hybrid security approaches to shield digital assets.
Quantum computers create a quantum threat to elliptic curve cryptography and to exposed private keys, especially as quantum supremacy advances. Grover’s algorithm cuts search work for symmetric keys, forcing longer keys or layered designs.
Quantum random number generation uses superposition states, double slit experiment setups, and measurements that collapse the wave function to give true randomness. Quantum Key Distribution, for example the BB84 protocol, shows secure key exchange, yet QKD is not ready for wide deployment.
Nodes need protocol upgrades, and hardware wallets used for Bitcoin must adopt post-quantum cryptographic signatures to protect private keys. Artificial intelligence and ML can scan ledgers, spot weak math, and automate migration paths to post-quantum cryptography.
Industry and Academic Efforts Towards Quantum Preparedness
NIST is moving fast, it is standardizing three post-quantum public-key standards, FIPS 203, 204, and 205. Quantum Resistant Ledger, research institutions, and startups fund work on lattice-based cryptography to protect private keys and digital assets.
MIT OpenCourseWare and Stanford courses teach core cryptography, and Signal and Wickr blogs host applied security talks. Applied cryptography builds software, while theoretical teams study finite field math, quadratic objective functions, and quantum algorithms like Grover’s algorithm; experiments even trace ideas back to dual-slit and double slits interference.
Industry and academia run joint labs and share benchmarks, code, and threat models to speed adoption of post-quantum cryptography. Groups use crypto libraries, open datasets, courseware, and ai tools to test quantum programs on emulators and noisy quantum computers aiming for quantum supremacy.
QRL, NIST, and university teams push for updates to wallets and protocols, and they urge moving lattice-based schemes into real systems.
Balancing Innovation with Security in the Quantum Era
Quantum computers can break today’s cryptography, and that puts decentralized digital assets at risk. Researchers show quantum search algorithms, like Grover’s algorithm, speed cryptographic analysis far beyond classical tools, and they can also tackle molecular modeling for drug design.
This threat makes community discussion urgent, and it pushes calls for proactive changes to protect private keys and the crypto ecosystem.
Transition will take years, it will require education, and it will need infrastructure updates to roll out post-quantum cryptography and lattice-based cryptography. Quantum annealing already aids optimization in financial modeling and drug design, and artificial intelligence groups must work with crypto engineers to balance innovation with security.
Hardware wallets, updated signature schemes that replace elliptic curve cryptography, and protocol shifts in proof-of-work and proof-of-stake systems add practical defenses.
Preparing the Crypto Ecosystem for the Quantum Transition
Cryptocurrencies should move early to post-quantum encryption standards to fix known vulnerabilities. The blockchain community must set common tests, and adopt post quantum cryptographic algorithms to defend against quantum computers.
Community discussion, urgency, and proactive changes are essential, and forums like Signal and Wickr host useful blogs for applied cryptography. Teams should trial lattice-based cryptography, swap in libraries, and run audits on migration paths.
Hardware wallets plus strict passphrase rules protect private keys while networks shift, and cold storage limits exposure to grover’s algorithm attacks. Education and awareness campaigns must teach developers, validators, and retail holders how to protect digital assets as computing power rises.
Researchers should pair artificial intelligence(ai) with big data tools to model attack windows and migration timelines.
Takeaways
Quantum machines will shake crypto, and raise a real quantum threat to private keys. Grover search will speed key guessing, while other quantum algorithms can crack signatures across blockchains.
NIST-backed shifts to lattice-based cryptography and post-quantum cryptography aim to protect digital assets. Hardware wallets, Taproot and Schnorr signatures buy time, but developers must move protocols fast.
FAQs on Ways Quantum Computing Could Impact Crypto
1. What is quantum computing and why is it a quantum threat to crypto?
Quantum computing uses quantum computers that use quantum physical effects to solve hard problems. It can change the game for cryptography, by using quantum algorithms to beat tasks that classical machines find slow. That potential risk is called the quantum threat, and people watch for signs of quantum supremacy.
2. Can quantum algorithms break elliptic curve cryptography or steal private keys?
Yes, some quantum algorithms can attack curve-based systems, and they can make finding private keys much faster. Think of a lock that a new machine can pick, much faster than before. Grover’s algorithm speeds search, and other quantum algorithms can target elliptic curve cryptography and private keys.
3. How can we protect digital assets from this threat?
Move to post-quantum cryptography now, use lattice-based cryptography options, and test cryptographic swaps in safe settings. Lattice based cryptography looks strong today, and it stays cryptographically sound under many tests. In short, plan early, act fast, be ready.
4. Will quantum supremacy make all crypto worthless overnight?
No, not overnight. Quantum supremacy means a quantum device solves some tasks faster, but practical attacks on real systems take time. Crypto teams, standards groups, and developers can harden systems, and many wallets and chains can upgrade, so digital assets are not doomed in a day.
5. How else could quantum computing affect blockchain and AI?
Quantum computing could speed consensus checks, change mining math, and speed some machine learning tasks, mixing with artificial intelligence in new ways. Quantum algorithms might cut computing time, but they also force new computing technology and design. It is a big shift, think of it like swapping from a bicycle to a rocket, you need new rules and new tools.