In a major cybersecurity incident, hackers have compromised the Tea app—a platform originally built as a safe digital space for women to privately discuss and warn each other about men—leading to the leak of over 13,000 personal photos and government-issued ID images.
The breach has triggered widespread concern over privacy, data security, and the future of women-centered digital platforms.
What Is the Tea App and Why Was It Created?
Tea was developed to function as a women-only, anonymous social platform that lets users share their dating experiences, report red flags, and conduct background searches on men they’ve interacted with. The app has positioned itself as a modern-day whisper network—allowing women to crowdsource safety information in the online dating era.
Founded by Sean Cook, the inspiration for Tea came from his own mother’s experience with online dating. Cook publicly shared that his mother had been catfished, deceived by men hiding criminal backgrounds, and put into emotionally and physically risky situations. This prompted him to build an app that could empower women to research and protect themselves by learning from others’ experiences.
On Tea, women can:
- Upload a man’s photo or search by name
- Tag individuals as “red flag” or “green flag”
- Leave anonymous reviews about behavior, character, and experiences
- Perform background checks to uncover past criminal records
- Reverse-search images to detect fake profiles or catfishing
Importantly, the app blocks screenshots and promises complete user anonymity—with the exception of chosen usernames—after a manual identity verification process involving government ID and selfie submission.
How the Hack Unfolded: Timeline and Scope
The breach came to light on Friday afternoon, after reports began surfacing about a possible data dump linked to the Tea app. A spokesperson from the company confirmed that their database had been illegally accessed, exposing more than 72,000 images, including 13,000 ID and selfie verification photos submitted during the registration process.
These images, required to prove users’ gender identity as women, were part of a legacy database from over two years ago, which the app claims was stored in compliance with law enforcement regulations on cyberbullying and abuse prevention.
While the company has maintained that user-uploaded images are deleted after review, the breach indicates that at least some of these records were retained longer than publicly disclosed—raising questions about data retention practices.
4Chan Connection: Planned Targeted Attack
Evidence suggests the hack was pre-meditated and coordinated, originating from a thread on 4Chan, a notorious online message board known for hosting toxic and extremist content. On Thursday night, 4Chan users launched a “hack and leak” campaign against Tea, expressing outrage over the app’s perceived targeting of men.
By Friday morning, a direct download link to the stolen image database appeared on the platform. Within hours, hundreds of posts began circulating on 4Chan and X (formerly Twitter) containing images of users’ government IDs, selfies, and potentially identifiable data.
Cybersecurity analysts believe the attackers may have viewed the app as a form of “gendered censorship,” and therefore chose to retaliate by undermining its security and exposing its users.
Serious Privacy Fallout: Location Data and Maps Shared
In a disturbing development, a Google Maps file was also created by an anonymous user. This map allegedly displays geographical coordinates of some Tea users based on the leaked data. While no specific names were attached to these locations, the very idea of mapping users—many of whom turned to the app seeking protection—has intensified fears about potential real-world harm, including stalking or harassment.
Some cybersecurity experts warn that the availability of geolocation data, when combined with facial images and ID documents, could open doors for doxxing, identity theft, and targeted harassment.
Tea App’s Official Response: Damage Control in Motion
Tea’s official spokesperson released a statement confirming the breach and stating that the company is “working around the clock” to contain the incident and enhance security.
“Protecting our users’ privacy and data is our highest priority,” the spokesperson said. “Tea is taking every necessary step to ensure the security of our platform and prevent further exposure.”
The company has hired third-party cybersecurity experts to conduct a full forensic investigation and has launched an emergency review of all its security systems, data storage policies, and user protection protocols.
As of now, Tea has not confirmed whether all users were affected, but many users are demanding more transparency regarding:
- What exactly was leaked
- Which users were impacted
- How long the data was stored
- Why old data wasn’t permanently deleted
User Trust Under Threat: Public Reactions Are Mixed
The app has seen explosive growth in recent days, with Tea confirming via its Instagram Story that over 2 million people have signed up. However, the sudden breach has led many users to question whether they can continue to trust a platform that asks for such sensitive information.
Dozens of users took to Tea’s social media pages to express concerns about:
- Whether their photos and IDs were among the stolen files
- If the company had ever clearly stated that such data would be retained
- Whether they should delete their accounts or pursue legal action
Some women even noted that they’re still stuck on waitlists, and fear their data may already be compromised even before accessing the platform.
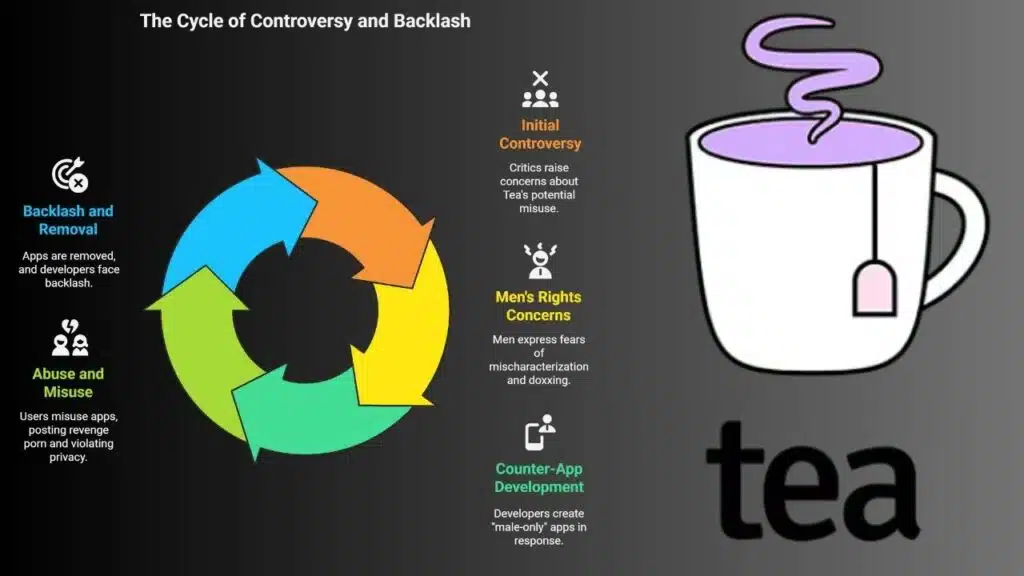
Controversy Beyond the Hack: A Polarizing App by Design
Even before the hack, Tea was controversial. Critics, particularly men’s rights groups, argued that it promoted “vigilante-style justice” and opened the door to false accusations or misuse by bitter exes or trolls.
Some men have expressed fears of being doxxed or mischaracterized without due process. In response to Tea, a few developers tried launching “male-only” apps that claimed to provide a counterbalance. One such app, called Teaborn, quickly spiraled into chaos after users began posting revenge porn and violating privacy guidelines. The app was subsequently removed from the App Store, and its developer received intense backlash for enabling abuse.
A Bigger Conversation: Women’s Safety vs. Data Security
The Tea app’s breach highlights a troubling dilemma: how can technology empower vulnerable groups without exposing them to new threats?
While the app aimed to protect women from dangerous encounters, the failure to secure highly sensitive data has created new vulnerabilities—ironically putting those same users at risk.
Cybersecurity experts and digital rights organizations are urging platforms like Tea to:
- Implement end-to-end encryption
- Minimize data retention
- Provide opt-out and data deletion options
- Offer clear and accessible user policies
What Happens Next?
Tea now faces a critical moment. To survive this crisis and maintain its user base, it must:
- Be transparent about what went wrong
- Clearly communicate with affected users
- Upgrade its security infrastructure
- Possibly face legal scrutiny or regulatory fines, depending on the jurisdictions affected
In a world where apps are being used to bridge safety gaps for women and marginalized groups, this hack serves as a sobering reminder that privacy and protection must go hand in hand.
The information is Collected from Fortune and NBC News.