In today’s hyper-connected corporate landscape, a standard consumer device is no longer just a communication tool; it is a potential vulnerability. For executives, journalists, and government officials, the most secure smartphones for business are not a luxury; they are a necessity. With the rise of “zero-click” spyware, sophisticated phishing attacks, and state-sponsored surveillance, relying on a simple passcode is no longer sufficient.
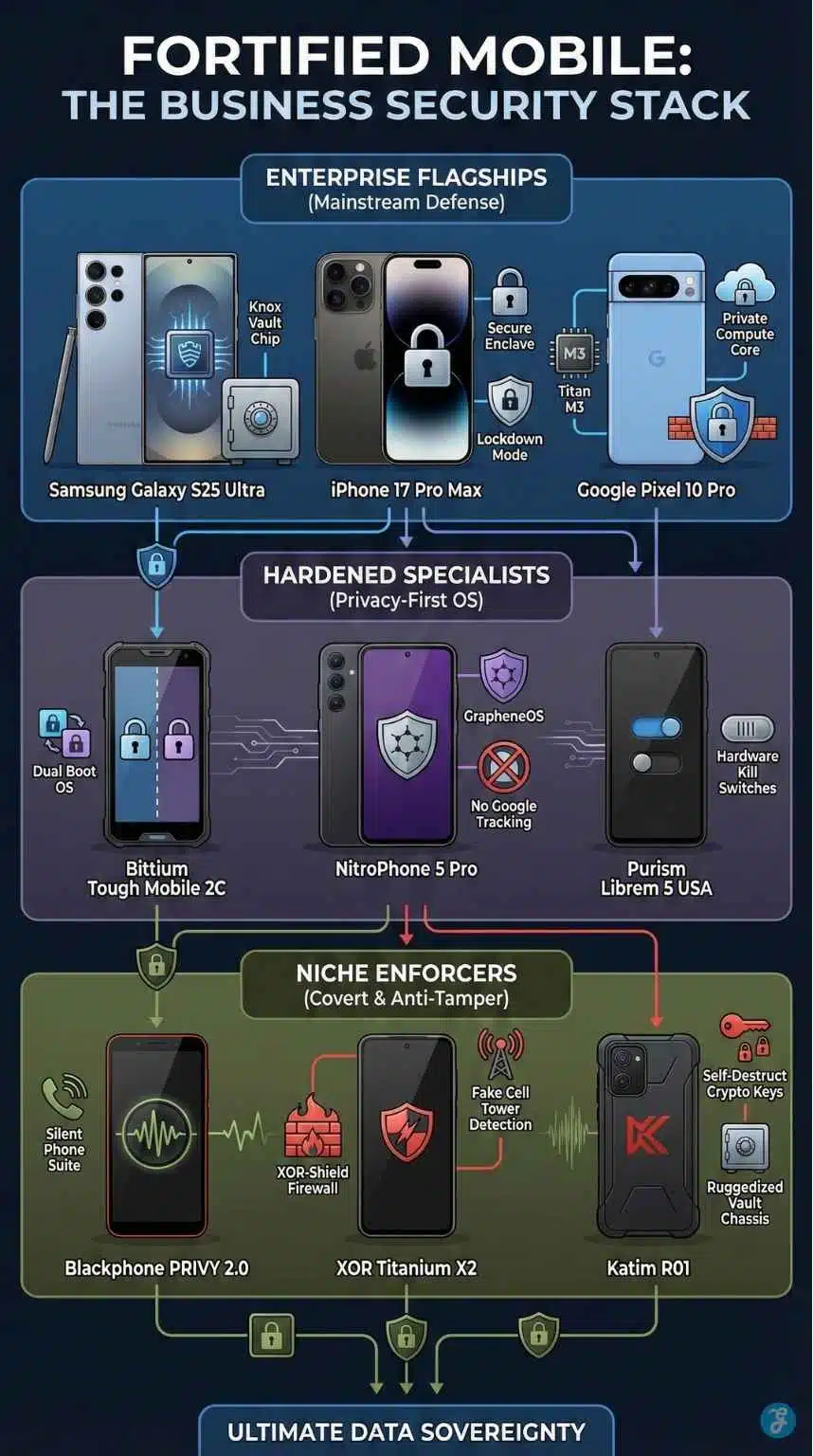
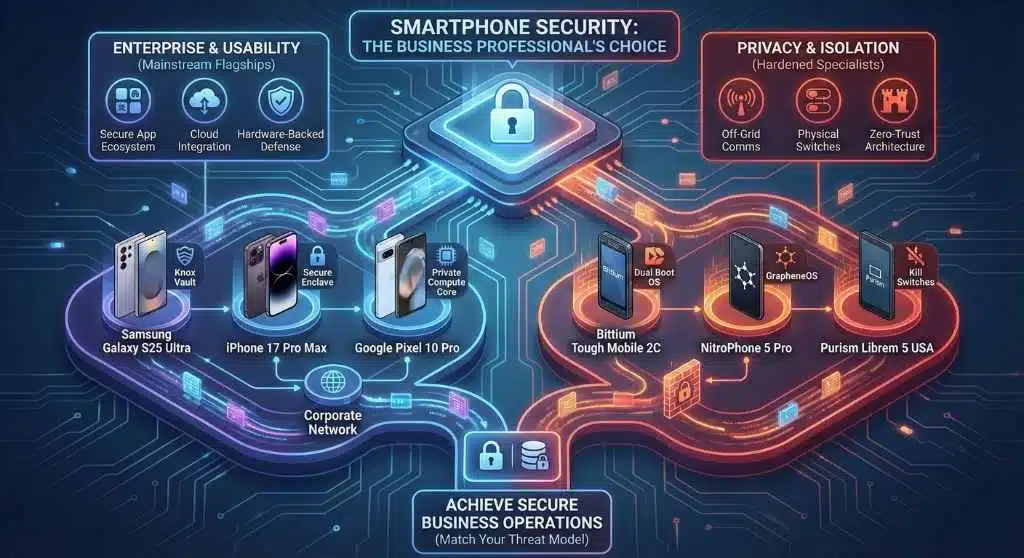
The landscape of mobile security has split into two distinct paths. On one side, we have the “Enterprise Flagships”—mainstream devices from Samsung, Apple, and Google that have integrated military-grade security architectures like Knox and Secure Enclave to protect corporate fleets. On the other side, we have “Privacy Fortresses”, specialized devices built from the ground up with custom operating systems, physical kill switches, and hardware-level encryption to ensure absolute data sovereignty.
This comprehensive guide ranks the top 12 devices across these categories, helping you choose the right tool for your threat model.
Key Takeaways
-
The S25 Ultra & iPhone 17: These remain the best choices for 90% of businesses due to the balance of usability, app support, and hardware-backed security.
-
Hardware Isolation: It is the gold standard; ensure your device has a separate chip for storing passwords (Knox Vault, Secure Enclave, Titan M).
-
Lockdown Modes are underutilized: If you travel to high-risk areas, enabling these features on Apple or Samsung devices can prevent state-level spyware attacks.
-
True Privacy requires sacrifice: Devices like the Librem 5 or XOR offer superior privacy but lack the app ecosystems of Android and iOS.
Quick Comparison: Top 3 Secure Phones at a Glance
| Device | Best For | Top Security Feature | OS Architecture |
| Samsung Galaxy S25 Ultra | Enterprise Fleets | Knox Vault (Hardware Isolation) | Android (One UI + Knox) |
| Bittium Tough Mobile 2C | Government/Defense | Dual Boot (Separated OS) | Hardened Android + Secure OS |
| Purism Librem 5 USA | Privacy Purists | 3x Hardware Kill Switches | PureOS (Linux-based) |
The “Big Three” Enterprise Flagships
Best for: C-Suite executives and corporate fleets requiring full app compatibility (Teams, Outlook, Slack) with robust, hardware-backed defense.
1. Samsung Galaxy S25 Ultra
The Standard for Corporate Defense
The Samsung Galaxy S25 Ultra continues to hold the crown as the default choice for enterprise security. While it looks like a consumer flagship, its real power lies in the Samsung Knox platform, a defense-grade security architecture anchored directly into the chip manufacturing process.
Why It Is Secure
The core of the S25 Ultra’s defense is Knox Vault. This is a tamper-resistant processor that is physically isolated from the phone’s main chipset (the Snapdragon 8 Elite). It stores your most sensitive data—PINs, passwords, biometrics, and blockchain keys—in a digital “safe room.” Even if a hacker manages to compromise the main Android operating system with malware, they cannot breach the physical barrier of the Knox Vault to steal your credentials.
Furthermore, the device introduces Message Guard, a “sandbox” that automatically isolates image files received via Samsung Messages, Google Messages, and select third-party apps. It neutralizes potential threats hidden in image attachments (steganography) before you even open them, effectively stopping zero-click exploits.
-
Key Specs: Snapdragon 8 Elite, Knox Vault (EAL5+ Certified), 7 years of security updates.
-
Best For: CIOs and Enterprise fleets that need seamless Microsoft integration.
2. iPhone 17 Pro Max
The Walled Garden Vault
Apple’s “walled garden” approach has long been its greatest security asset, but the iPhone 17 Pro Max takes this further with specialized modes designed for high-risk targets. The device relies on the Secure Enclave, a dedicated coprocessor that handles encryption keys and FaceID data, ensuring that even Apple itself cannot access your device’s contents.
Why It Is Secure
The standout feature for high-risk professionals is Lockdown Mode. When activated, this optional “extreme protection” setting significantly reduces the attack surface of the iPhone. It blocks most message attachments, disables complex web technologies (like JIT JavaScript compilation), and blocks incoming service invitations from strangers. It essentially turns the smartphone into a fortress, making it incredibly difficult for mercenary spyware (like Pegasus) to gain a foothold.
Additionally, the new Advanced Data Protection for iCloud ensures end-to-end encryption for your cloud backups. This means that if you lose your phone, your data in the cloud remains encrypted with keys only you hold, preventing law enforcement or hackers from subpoenaing or stealing your backups.
-
Key Specs: A19 Pro Chip, Secure Enclave, Lockdown Mode 2.0.
-
Best For: Journalists, diplomats, and executives targeted by sophisticated spyware.
3. Google Pixel 10 Pro
The AI Guardian
The Google Pixel 10 Pro represents the cleanest, most responsive version of Android, backed by Google’s custom silicon. It is the first device to receive monthly security patches, closing vulnerabilities faster than any other Android manufacturer.
Why It Is Secure
The security backbone of the Pixel 10 Pro is the Titan M3 security chip. Similar to a credit card chip, it verifies the integrity of the operating system every time the phone boots up. If it detects that the OS has been tampered with or downgraded to an older, vulnerable version, it prevents the phone from booting.
Google also emphasizes on-device processing via the Private Compute Core. This distinct partition of the operating system handles sensitive data processing—like Live Caption, Now Playing, and Smart Reply—completely offline. This ensures that your behavioral data and ambient audio processing never leave the device to touch the cloud, neutralizing network-based interception risks.
-
Key Specs: Tensor G5, Titan M3 Chip, Private Compute Core.
-
Best For: Professionals who want a stock Android experience with the fastest patch cycle.
4. Motorola ThinkPhone 25
The IT Department’s Extension
Designed explicitly to pair with the ubiquitous Lenovo ThinkPad laptops, the Motorola ThinkPhone is a business-first device. It bridges the gap between mobile and desktop security, offering a unified “safe space” for corporate data.
Why It Is Secure
The device runs on ThinkShield for Mobile, a comprehensive security platform that mimics the BIOS-level security found in Lenovo PCs. It includes Moto KeySafe, a dedicated hardware security layer that adds an extra level of protection for passwords and encryption keys.
Crucially for IT managers, the ThinkPhone allows for seamless, secure integration with Windows. You can drag and drop files securely between phone and laptop, use the phone as an encrypted webcam, and share a unified clipboard, all protected by a local, encrypted connection that doesn’t rely on public cloud servers.
-
Key Specs: ThinkShield, Moto KeySafe, MIL-STD 810H durability.
-
Best For: Organizations already invested in the Lenovo/Windows ecosystem.
The “Hardened” Privacy Specialists
Best for: Users who fundamentally distrust Big Tech data collection and require an operating system free from mass surveillance.
5. Bittium Tough Mobile 2C
The Military-Grade Tank
Hailing from Finland, Bittium is a favorite among European defense agencies. The Tough Mobile 2C is not just a phone; it is a secure communications terminal designed to operate in hostile environments.
Why It Is Secure
The defining feature of the 2C is its Dual-Boot Functionality. The device literally runs two completely separate operating systems.
-
Hardened Android: For day-to-day tasks (email, browsing).
- Bittium Secure OS: A restricted, high-security zone for top-secret data.These two modes are completely isolated from one another. Additionally, the phone features a hardware-based Privacy Mode that physically disconnects microphones, cameras, and Bluetooth at the touch of a button, ensuring that no malware can covertly record your meetings.
-
Key Specs: Dual-Boot OS, Hardware Privacy Mode, IP67, Made in Finland.
-
Best For: Government officials and defense contractors.
6. NitroPhone 5 Pro
The “De-Googled” Flagship
Physically, the NitroPhone 5 Pro is a Google Pixel. However, the software has been completely scrubbed and replaced by the German security firm Nitrokey. It offers the high-end hardware of a flagship with the privacy of a burner phone.
Why It Is Secure
The device runs GrapheneOS, widely considered the most secure Android variant in existence. GrapheneOS hardens the memory allocator against zero-day exploits, removes all Google Play Services (stopping tracking), and sandboxes every app strictly.
Uniquely, Nitrokey offers a version where the microphones and sensors are physically removed from the circuit board before shipping. This “hardware removal” guarantees that even if the phone is hacked, it physically cannot listen to you.
-
Key Specs: GrapheneOS, Optional Physical Sensor Removal, Titan M2.
-
Best For: Tech-savvy professionals who want modern hardware without the data harvesting.
7. Purism Librem 5 USA
Supply Chain Sovereignty
Most phones are assembled in China, raising concerns about supply chain interdiction (hardware backdoors installed at the factory). The Purism Librem 5 USA addresses this by manufacturing its electronics within the United States.
Why It Is Secure
The Librem 5 runs PureOS, a Linux-based operating system that is not Android. This makes it immune to the vast majority of Android malware. Its most famous feature is the set of three Hardware Kill Switches on the side of the chassis.
-
Switch 1 cuts the Camera and Mic.
-
Switch 2 cuts WiFi and Bluetooth.
- Switch 3 cuts the Cellular Modem.When these switches are flipped, the circuits are mechanically severed. No software hack in the world can override a broken circuit.
-
Key Specs: PureOS (Linux), 3 Hardware Kill Switches, User-Replaceable Battery.
-
Best For: Privacy purists who need to ensure they cannot be tracked or recorded.
8. Murena 2
The Privacy Switch for Everyone
The Murena 2 is designed for the non-technical user who wants privacy “out of the box” without needing to learn Linux or flash a custom ROM.
Why It Is Secure
It runs /e/OS, a “de-Googled” version of Android that replaces Google services with private alternatives. The phone features a unique Privacy Switch on the side that instantly cuts the camera and microphone circuits.
Software-wise, it features an Advanced Privacy Widget—a dashboard that shows you exactly which trackers are being blocked in real-time. It also allows you to mask your IP address and fake your geolocation effortlessly, feeding false data to apps that demand to know where you are.
-
Key Specs: /e/OS, Physical Privacy Switch, Tracker Blocking Dashboard.
-
Best For: General users who want privacy without a steep learning curve.
The Niche Enforcers
Best for: Covert communication, anti-tampering, and ultra-high-net-worth individuals.
9. Blackphone PRIVY 2.0
The Comms Specialist
Developed by the pioneers of encrypted communication, Silent Circle, the Blackphone PRIVY 2.0 is a device dedicated to protecting what you say and type.
Why It Is Secure
The phone comes pre-loaded with the Silent Phone Suite, a peer-to-peer encrypted calling and messaging platform. These calls do not route through standard carrier voice networks, bypassing the lawful interception systems used by governments and telcos. The device acts as a “hardened endpoint” for these encrypted sessions, ensuring that the keys are generated and stored locally on the device, never on a server.
-
Key Specs: Silent OS, Silent Phone Suite, Encrypted file storage.
-
Best For: International deal-makers negotiating in high-risk regions.
10. XOR Titanium X2
The Luxury Firewall
The XOR Titanium X2 is a “dumb” phone. It has no app store, no web browser, and no games. This limitation is its strength. By removing the ability to install apps, you remove 99% of the attack surface.
Why It Is Secure
Hand-built from titanium, this phone features XOR-Shield, a firmware-level firewall for the SIM card. It can detect “Stingrays” (fake cell towers used by police and criminals to intercept calls) and alert the user. It also supports a remote wipe feature that can be triggered by sending a secret SMS code from another phone, instantly bricking the device if it is stolen.
-
Key Specs: Proprietary OS, Fake BTS Detection, Remote Data Wipe.
-
Best For: Ultra-high-net-worth individuals who need a phone strictly for secure voice calls.
11. Katim R01
The Rugged Vault
The Katim R01 is a ruggedized smartphone built for field operatives. It is designed to withstand both physical and digital assaults.
Why It Is Secure
The device features a Self-Destruct Mechanism for its encryption keys. If the phone’s sensors detect physical tampering—such as an attempt to drill into the casing or freeze the memory chips (a “cold boot” attack)—the device will automatically wipe the encryption keys, rendering the data mathematically unrecoverable. It also features a “Shield Mode” that disables all recording sensors and radio transmissions for top-secret meetings.
-
Key Specs: Tamper-Proof Chassis, Self-Destruct Crypto Keys, Shield Mode.
-
Best For: Field operatives working in hostile physical environments.
12. Fairphone 5 (Enterprise Edition)
The Ethical Long-Game
While famous for its repairability, the Fairphone 5 is a hidden gem for security due to its unparalleled support lifecycle.
Why It Is Secure
Most security vulnerabilities arise from outdated software. Manufacturers often drop support after 3-4 years, leaving phones exposed. Fairphone guarantees 8 to 10 years of security updates. This means a Fairphone 5 bought today will still be receiving critical patches in the early 2030s. Its modular design also allows for the physical removal of cameras or microphones if a business requires a camera-less device for sensitive facilities.
-
Key Specs: 8+ Years Support, Modular Hardware, Easy Component Removal.
-
Best For: Environmentally conscious businesses requiring long-term asset utility.
Buying Guide: What Makes a Smartphone “Business Secure”?
When evaluating a device for your business, look beyond the marketing fluff and focus on these four pillars of mobile security:
1. Hardware Root of Trust
Software encryption is good, but hardware encryption is better. Look for devices with a dedicated security chip (like Titan M3, Secure Enclave, or Knox Vault). These chips are separate from the main processor and store your encryption keys. If the main OS is hacked, the attacker still cannot extract the keys from this separate “vault.”
2. Supply Chain Integrity
Where was the phone made? For most businesses, standard manufacturing is fine. However, for high-threat profiles, “Supply Chain Interdiction” is a real risk. Devices like the Purism Librem 5 USA or Bittium offer tighter control over the assembly process, reducing the risk of a hardware bug being planted at the factory.
3. OS Hardening & Updates
A secure phone is an updated phone.
-
Mainstream: Look for commitments of at least 5-7 years of monthly security patches.
-
Custom OS: Operating systems like GrapheneOS (on NitroPhone) offer memory hardening that makes it significantly harder for malware to exploit bugs, even if they haven’t been patched yet.
4. Physical Kill Switches
For the ultimate peace of mind, software toggles aren’t enough. Malware can fake a “software off” switch. A physical switch that breaks the electrical circuit (like on the Purism or Murena) is the only way to be 100% sure your camera and mic are off.
Frequently Asked Questions (FAQ)
Is an iPhone more secure than a Samsung Knox device?
For the average user, they are functionally equivalent. Both use hardware-backed encryption (Secure Enclave vs. Knox Vault). However, Samsung’s Knox platform offers more granular control for IT departments to manage corporate fleets, while Apple’s “Lockdown Mode” offers a slightly more accessible “panic button” for individuals under attack.
Can secure smartphones be hacked?
Yes. No device is “uncrackable.” However, the goal is to make the cost of hacking the device higher than the value of the data on it. Hacking a fully updated Pixel 10 Pro or iPhone 17 requires million-dollar “zero-day” exploits that are typically reserved for high-value targets like terrorists or dissidents, not average business owners.
What is a “De-Googled” phone?
A “De-Googled” phone is an Android device that has had all Google services (Play Store, Maps, Tracking Frameworks) removed. This stops Google from collecting your location and usage data. While excellent for privacy, it means you cannot use apps that rely on Google Play Services (like Uber, banking apps, or push notifications) without complex workarounds.
Why do I need a hardware kill switch?
Malware can trick your software into thinking the camera is off while it is secretly recording. A hardware kill switch physically severs the electrical connection to the component. It is the digital equivalent of unplugging a webcam—physics guarantees it cannot be used.
Is it worth buying an encrypted “niche” phone like XOR or Blackphone?
Only if your threat model involves targeted espionage. For a standard lawyer or doctor, these phones are overkill and inconvenient (no WhatsApp, no Maps). But for an arms dealer negotiator or a journalist in a war zone, the inability to be geo-located or intercepted via fake cell towers is worth the lack of Candy Crush.
Final Thought: Security is a Process, Not a Product
Buying one of the most secure smartphones for business is a powerful first step, but it is not a magic bullet. The most sophisticated encryption in the world cannot save you if you use “Password123” or click on suspicious links.
The best security strategy combines the right hardware, like the fortress-like Galaxy S25 Ultra or the privacy-centric NitroPhone, with the right mindset. Treat your phone like a vault, not a toy, and your business secrets will remain exactly that: secret.