In today’s digital age, website security is more critical than ever. Cyber threats continue to evolve, targeting businesses and personal websites alike. Hackers exploit weak security points to steal data, disrupt services, and compromise user trust.
Addressing these vulnerabilities is not optional—it’s essential for protecting your online presence.
In this comprehensive guide, we’ll explore the 10 Most Common Website Security Vulnerabilities, understand how they impact websites, and discuss actionable steps to fix them. Whether you run a small blog or a large e-commerce platform, ensuring your site is secure will protect both your business and your users.
1. SQL Injection (SQLi)
SQL Injection remains one of the most common website security vulnerabilities today, affecting websites across industries. Hackers exploit this vulnerability to manipulate or extract critical data from databases, putting businesses and users at risk. Understanding how SQL Injection works is crucial to implementing robust security measures.
What is SQL Injection?
SQL Injection (SQLi) is one of the most common website security vulnerabilities that allows attackers to manipulate database queries. By injecting malicious SQL code, hackers can gain unauthorized access to sensitive data, modify records, or even delete databases. Attackers typically exploit vulnerable input fields such as login forms, search bars, and URL parameters where user input is not properly sanitized.
Risks of SQL Injection
- Unauthorized access to user data, including usernames, passwords, and payment information.
- Data leaks and theft that can result in identity fraud and reputational damage.
- Full database compromise, allowing attackers to modify, delete, or steal critical records.
- Website defacement or deletion, disrupting operations and damaging credibility.
- Potential escalation to server-level access, leading to a complete system takeover.
How to Fix SQL Injection
- Use Prepared Statements & Parameterized Queries – Prevent direct SQL execution by properly structuring database queries. This ensures user inputs are treated as data, not executable code.
- Input Validation & Sanitization – Enforce strict validation rules to reject unexpected inputs and escape special characters that could be used for SQL injection.
- Limit Database Permissions – Assign the least necessary privileges to database users, restricting access to critical operations.
Deploy Web Application Firewall (WAF) – Blocks malicious SQL injection attempts automatically by monitoring and filtering incoming traffic.
- Use ORM (Object-Relational Mapping) Libraries – Frameworks like SQLAlchemy, Hibernate, or Django ORM help prevent SQL injection by managing database interactions securely.
- Monitor and Log Database Activity – Regularly review logs to detect and respond to unusual query patterns that may indicate an attack attempt.
- Keep Database and Server Software Updated – Ensure your database management system (DBMS) is patched against known vulnerabilities to reduce risks.
2. Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) is among the most common website security vulnerabilities that allows attackers to inject malicious scripts into trusted websites.
These scripts execute in users’ browsers, potentially leading to stolen credentials, unauthorized actions, and compromised website integrity. Understanding XSS vulnerabilities and implementing security measures is essential to protect users and maintain trust.
What is XSS?
Cross-Site Scripting (XSS) is an attack where hackers inject malicious scripts into webpages that execute in a user’s browser. This can be used to steal cookies, session tokens, manipulate webpage content, and even perform actions on behalf of users without their consent.
XSS vulnerabilities are often exploited through comment sections, login forms, and search bars when user input is not properly validated.
Risks of XSS
- User data theft (passwords, credit card details, personal information)
- Redirection to phishing sites or malware-infected pages
- Unauthorized website modifications leading to defacement or misinformation
- Exploiting administrative accounts to gain higher-level access
- Hijacking user sessions to perform unauthorized actions
- Spreading malware through malicious links embedded in website elements
How to Fix XSS
- Sanitize and Validate User Input – Ensure all user-generated content is properly encoded and escapes special characters to prevent script execution.
- Implement Content Security Policy (CSP) – Restrict unauthorized script execution by specifying allowed content sources.
- Escape Output Data – Convert special characters in user-generated content to HTML entities to prevent browsers from interpreting them as code.
- Use Secure JavaScript Frameworks – React, Angular, and Vue have built-in XSS protections that automatically sanitize dynamic content.
- Apply HTTP Security Headers – Use headers like X-XSS-Protection and X-Content-Type-Options to add additional layers of security.
- Use Subresource Integrity (SRI) – Prevent tampering with externally loaded scripts by verifying file integrity through cryptographic hash checks.
3. Cross-Site Request Forgery (CSRF)
Cross-Site Request Forgery (CSRF) is one of the most common website security vulnerabilities that exploits authenticated user sessions. This attack forces users to execute unwanted actions on a trusted website without their knowledge. Websites that lack proper validation mechanisms are particularly vulnerable to CSRF attacks, making it crucial to implement effective security measures.
What is CSRF?
CSRF (Cross-Site Request Forgery) attacks trick authenticated users into performing actions they didn’t intend, such as transferring funds, changing account settings, or modifying security preferences, without their knowledge. Attackers often exploit users who are logged into a trusted site by embedding malicious requests into web forms, emails, or social media links.
Risks of CSRF
- Unauthorized transactions or password changes, leading to financial and personal data loss.
- User impersonation, allowing attackers to take control of legitimate user sessions.
- Account takeovers that can lead to the exposure of sensitive information.
- Manipulation of user settings, including email addresses and security credentials.
How to Fix CSRF
- Use Anti-CSRF Tokens – Generate unique, cryptographically secure tokens for each request and validate them on the server side.
- Verify Referrer Headers – Ensure incoming requests originate from trusted sources and block suspicious ones.
- Enforce Secure Authentication – Implement multi-factor authentication (MFA) to add an extra layer of protection.
- Set Strict SameSite Cookie Policies – Configure cookies with the ‘SameSite=strict’ attribute to prevent unauthorized request execution.
- Limit Session Lifetimes & Implement Logout Mechanisms – Reduce the window of attack by automatically logging users out after a period of inactivity.
- Use HTTP-Only & Secure Cookies – Prevent access to authentication cookies from client-side scripts and enforce encryption in transit.
4. Weak Password Security
Weak password security remains one of the most common website security vulnerabilities, often leading to unauthorized access and data breaches. Cybercriminals use various tactics, such as brute force attacks and credential stuffing, to exploit weak passwords and gain control over user accounts. Strengthening password policies is a crucial step in safeguarding sensitive information.
Why Weak Passwords Are a Risk
Many websites suffer from security breaches due to weak or reused passwords. Attackers use brute force techniques to guess login credentials. Furthermore, credentials obtained from previous data breaches are often used in credential stuffing attacks, where hackers try stolen username-password pairs on multiple sites. With the rise of automated hacking tools, weak passwords can be cracked within minutes, leading to unauthorized access, data theft, and financial losses.
How to Fix Weak Password Security
- Enforce Strong Password Policies – Require complex, unique passwords with a mix of uppercase and lowercase letters, numbers, and special characters.
- Implement Multi-Factor Authentication – Adds an extra layer of security by requiring additional verification methods such as OTPs or biometric authentication.
- Monitor Login Attempts & Lockout Policies – Detect and block brute-force attacks by limiting failed login attempts and implementing CAPTCHA verification.
- Use a Password Manager– Encourage users to store credentials securely in an encrypted password manager rather than writing them down or reusing passwords across multiple sites.
- Educate Users About Phishing & Social Engineering – Cybercriminals often trick users into revealing passwords through phishing emails and fake login pages. Awareness training can help prevent such attacks.
5. Insecure File Uploads
Allowing users to upload files without proper security measures is one of the most common website security vulnerabilities that can lead to serious consequences. Attackers often exploit weak file upload mechanisms to execute malicious scripts, compromise servers, or launch cyber attacks. Without strict security controls, websites become easy targets for unauthorized access and data breaches.
Why File Uploads Are Dangerous
Allowing users to upload files without restrictions can lead to malicious file execution. Attackers can exploit file upload functionalities to upload scripts, execute arbitrary code, or distribute malware.
Malicious uploads can compromise entire servers, steal sensitive data, or deface websites. Additionally, improperly handled file uploads can result in denial-of-service (DoS) attacks due to resource exhaustion.
How to Fix Insecure File Uploads
- Restrict File Types & Sizes – Allow only necessary file extensions and impose file size limits to prevent oversized uploads from consuming server resources.
- Use Secure Storage Locations – Store uploaded files outside the web root directory to prevent direct access. Implement access controls to limit exposure.
- Scan Uploaded Files – Implement real-time malware scanning to detect and block malicious files before they can be executed.
- Rename Uploaded Files – Prevent execution by renaming files with random, non-executable names and removing potentially dangerous extensions.
- Validate File Content – Check the MIME type and file signatures to ensure uploaded files match their claimed formats.
- Implement User Authentication & Permissions – Restrict file uploads to authenticated users and enforce role-based access controls to limit who can upload and manage files.
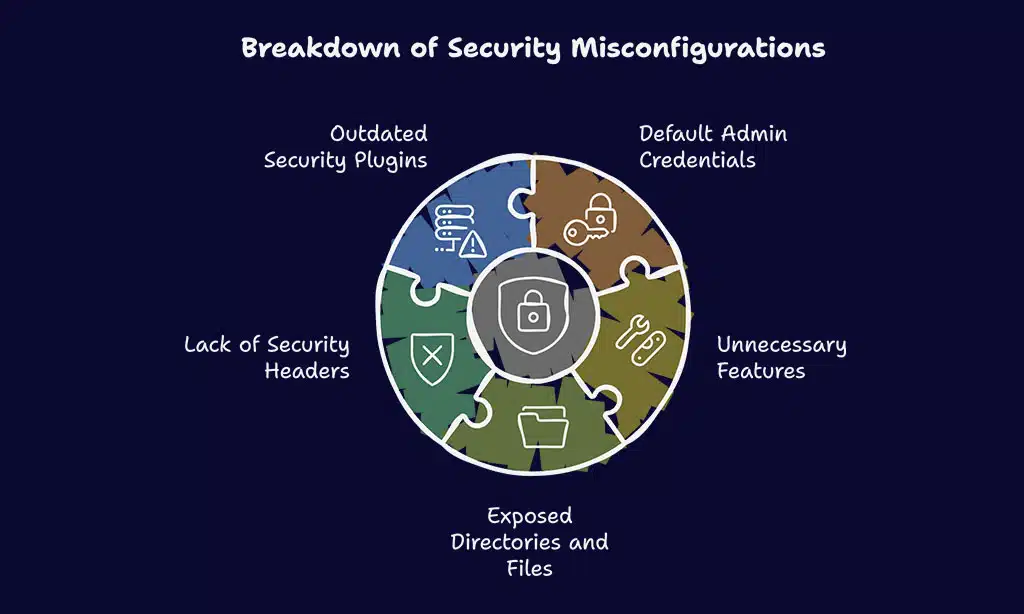
6. Security Misconfigurations
Security misconfigurations remain one of the most common website security vulnerabilities, often arising due to default settings, incomplete configurations, or overlooked security patches.
Attackers actively exploit these misconfigurations to gain unauthorized access, manipulate system behavior, or extract sensitive data. Regular security assessments and proper configuration management are essential to minimize these risks.
Common Security Misconfigurations
- Default admin credentials, which make it easy for attackers to gain unauthorized access.
- Unnecessary features enabled, increasing the attack surface and making the system more vulnerable.
- Exposed directories and files, which can be exploited to gather sensitive information or execute malicious scripts.
- Lack of proper security headers, leaving the website susceptible to XSS, Clickjacking, and MIME-type sniffing attacks.
- Outdated or misconfigured security plugins, leading to potential gaps in protection.
How to Fix Security Misconfigurations
- Regularly Audit Security Settings – Conduct frequent security assessments to identify and patch vulnerabilities.
- Disable Unused Features & Services – Turn off default or unused settings, plugins, and services to minimize security risks.
- Implement the Principle of Least Privilege – Grant users only the permissions necessary for their roles to prevent unauthorized access.
- Apply Security Headers – Configure HTTP security headers like Content Security Policy (CSP), X-Frame-Options, and X-XSS-Protection.
- Ensure Proper Configuration of Security Plugins – Use well-maintained security plugins and configure them correctly for optimal protection.
7. Unpatched Software and Plugins
Unpatched software and outdated plugins remain among the most common website security vulnerabilities, exposing websites to known exploits and cyberattacks.
Hackers actively scan for unpatched vulnerabilities in content management systems (CMS), plugins, and themes, allowing them to inject malware, steal sensitive data, or take control of websites. Keeping software updated is a critical step in preventing these security risks.
Why Outdated Software Is a Threat
Hackers exploit vulnerabilities in outdated CMS, plugins, and themes. When software is not regularly updated, it creates security loopholes that cybercriminals can exploit to inject malicious code, gain unauthorized access, or cause disruptions. Many well-known breaches have occurred due to outdated software being exploited by attackers.
How to Fix This
- Regular Updates & Patching – Keep software up to date by installing the latest patches as soon as they are released to close security gaps.
- Remove Unused Plugins & Themes – Eliminate unnecessary software to reduce attack surfaces and improve overall security.
- Use Only Trusted Plugins – Choose well-maintained software from reputable sources to ensure timely updates and patches.
- Automate Updates Where Possible – Enable automatic updates for CMS, plugins, and themes to reduce the risk of missing critical patches.
- Perform Security Audits Regularly – Conduct vulnerability scans and security assessments to identify and address potential weaknesses before they are exploited.
8. Insufficient Data Encryption
Data encryption plays a vital role in safeguarding sensitive information online, yet it remains one of the most common website security vulnerabilities. Many websites fail to implement robust encryption standards, leaving user data exposed to cybercriminals.
Without proper encryption, financial transactions, login credentials, and personal details become easy targets for hackers, leading to identity theft and financial fraud.
Why Encryption Matters
Without encryption, sensitive data is exposed to interception by hackers. Unencrypted data traveling over the internet can be easily intercepted through man-in-the-middle (MITM) attacks, compromising login credentials, financial transactions, and personal information. Moreover, data stored in databases without encryption is vulnerable to breaches, leading to identity theft and financial loss.
How to Fix Insufficient Encryption
- Use SSL/TLS Certificates – Encrypt data in transit to prevent eavesdropping and tampering. Websites should enforce HTTPS with an updated SSL/TLS certificate to ensure secure communication.
- Encrypt Stored User Data – Implement database encryption to protect sensitive records, ensuring unauthorized users cannot access plaintext data even if a breach occurs.
- Implement End-to-End Encryption – Secure private user communications by encrypting data at both the sender’s and recipient’s ends, ensuring only intended recipients can decrypt messages.
- Use Strong Encryption Algorithms – Employ AES-256 encryption for data storage and TLS 1.3 for secure transmissions. Avoid deprecated protocols like SSL and TLS 1.0.
- Regularly Rotate Encryption Keys – Update encryption keys periodically to reduce the risk of key compromise. Use a robust key management system to securely store and manage encryption keys.
9. Lack of Proper Access Controls
Lack of proper access controls is one of the most common website security vulnerabilities, allowing unauthorized users to access sensitive areas of a system. When access permissions are not adequately defined, attackers can exploit weaknesses to escalate privileges, manipulate data, or gain full control over critical infrastructure.
Proper access management ensures that only authorized users have the necessary permissions, reducing the risk of security breaches.
Risks of Poor Access Control
- Unauthorized access to critical areas, allowing attackers to manipulate or steal sensitive data.
- Data breaches due to weak access rules, which can lead to financial losses and reputational damage.
- Privilege escalation attacks where attackers gain higher-level permissions than intended.
- Insider threats where employees or contractors abuse their access to harm the organization.
How to Fix Access Control Issues
- Use Role-Based Access Control (RBAC) – Limit access per user roles and enforce the principle of least privilege.
- Monitor & Log User Activity – Track and analyze access logs to detect suspicious access patterns and prevent unauthorized modifications.
- Use Secure Authentication Methods – Enforce strong passwords, Multi-Factor Authentication (MFA), and biometric authentication where possible.
- Implement Just-In-Time Access Control – Grant temporary access privileges only when needed, reducing long-term exposure.
- Regularly Review & Update Access Policies – Periodically audit user roles and access levels to ensure compliance with security best practices.
- Apply Network Segmentation – Restrict user access to only necessary parts of the system, limiting lateral movement in case of a breach.
10. DDoS Attacks & Poor Traffic Management
DDoS (Distributed Denial-of-Service) attacks are among the most common website security vulnerabilities, posing a serious threat to website availability and performance.
Attackers use botnets and automated scripts to flood a website with massive amounts of traffic, making it impossible for legitimate users to access services. Without proper traffic management, businesses risk downtime, financial losses, and reputational damage.
Why DDoS Attacks Are Harmful
DDoS (Distributed Denial-of-Service) attacks flood servers with excessive traffic, causing downtime. These attacks can overwhelm server resources, making websites inaccessible to legitimate users. Cybercriminals often use botnets to execute large-scale DDoS attacks, which can severely impact businesses, leading to lost revenue and damaged reputations.
How to Fix DDoS Vulnerabilities
- Use a CDN with DDoS Protection – Content Delivery Networks (CDNs) help distribute traffic and filter out malicious requests before they reach your main server.
- Implement Rate Limiting – Restrict the number of requests per user to prevent flooding and brute-force attempts.
- Monitor Traffic & Set Up Alerts – Use real-time monitoring tools to detect early signs of a DDoS attack and respond promptly.
- Deploy Web Application Firewalls (WAF) – WAFs can detect and block malicious traffic patterns associated with DDoS attacks.
- Leverage Anycast Routing – Distribute incoming traffic across multiple servers to prevent single points of failure.
- Work with a DDoS Mitigation Service – Specialized security services can help absorb and neutralize large-scale DDoS attacks before they impact your website.
Takeaways
Cybersecurity is an ongoing process. Protecting your website from the Most Common Website Security Vulnerabilities requires proactive measures, continuous monitoring, and regular updates.
By implementing the security fixes outlined in this guide, you can safeguard your website against hackers and ensure a safer experience for your users.