Have you lost sleep over a data breach? A single hack can shut down your app, leak files, or lock your team out. You might feel stuck, staring at logs at 3 AM. You need strong digital guards.
Cybersecurity Firms In Poland Protecting The Digital World work day and night to guard your data. QualySec runs in-depth penetration tests and has kept Microsoft and Adobe safe. This post will list ten top firms and show how they spot weak spots, stop attacks, and guide you past rules like GDPR.
Keep reading.
Key Takeaways
- QualySec has served Microsoft and Adobe for eight years under Chandan Kumar Sahoo. Sekurno wins 90% positive reviews. Both firms test apps and networks with Nmap, Metasploit, and Nessus.
- Securing (est. 2003 in Warsaw and Kraków) and TPx Communications run 24/7 SIEM and threat scans. They meet a three-hour response SLA. Cyber Cops offer similar managed SOC services.
- NextLink Labs and Foresite Cybersecurity report 100% customer satisfaction. They build DevSecOps pipelines, use SIEM platforms, and guide clients on data protection and risk management.
- Rewterz and Link Group help firms meet GDPR and ISO 27001 rules. They craft custom risk plans and run incident response drills to boost compliance and resilience.
- SOC hubs in Kraków and Katowice use Splunk, Zeek, and Suricata. They guard networks, SCADA systems, and power grids with AI-driven monitoring and real-time packet analysis.
What services does QualySec offer?
QualySec offers penetration testing, web app assessment, mobile device security, connectivity checks, and internet safety reviews. Analysts run vulnerability scanners and web proxy systems.
They scan networks for risks, do threat analysis, and test application security. Experts guide clients on data protection, risk management, and compliance.
Founder Chandan Kumar Sahoo guides the crew with over eight years in cyber defense. Companies like Microsoft, Adobe, Facebook, and Buffer trust their pen testing skills. Reviews hail them as a leader in penetration testing services.
Clients praise their security consulting and information security efforts. The firm holds a strong reputation for reliability and client satisfaction.
How does Securing protect digital assets?
Securing has protected digital assets since 2003 from its Warsaw and Kraków offices. The firm builds custom IT solutions for each project, weaving risk assessment, vulnerability management, and encryption into every layer.
A security monitoring platform feeds real-time vulnerability updates to clients, so teams can patch weak spots fast. Shared expertise among cyber teams acts as a force multiplier, boosting incident response skills across the board.
Specialists deploy intrusion detection systems and a scanning tool to monitor network traffic and applications. Clients get ongoing support and updates, so digital protection never sleeps.
This proactive defense model helps with threat mitigation and asset management, and cuts response time. Teams tweak each setup to match client needs, keeping security tight as a drum.
What cybersecurity solutions does NextLink Labs provide?
NextLink Labs uses DevSecOps and process improvement to harden code and ops. Engineers build secure CI/CD pipelines with a build server and an automation tool. They run vulnerability scans as part of each flow.
Teams add threat modeling before every release. Clients note outcome transparency and praise clear communication.
Managers draw on strong project leadership to lift productivity and guard data. The company shows metrics that highlight measurable improvements in security posture. Service delivery shines with integrity and it drives high trust.
This approach fuels 100 percent customer satisfaction.
How does TPx Communications enhance cybersecurity?
TPx boosts cybersecurity with digital defense that monitors and blocks threats around the clock. They run safe links, enforce network safety, scan endpoints, and guard data stores for data protection.
They mix IT solutions with security shields to give full coverage. This mix cuts blind spots and stops sneaky hacks.
Their plans cost less. That helps firms large and small. Teams learn key tricks through live classes and clear guides. This educational approach builds smart, confident staff. It turns risk management from a worry into a daily habit.
What are Sekurno’s key cybersecurity offerings?
Sekurno probes networks and apps for weak spots, using Nmap for port mapping and Metasploit for exploit tests. The team runs vulnerability assessments with Nessus and manual checks, then crafts risk management plans.
Their managed services feed real time alerts into a SIEM console, keeping threats in sight. Analysts follow a clear security evaluation path, tying fixes to business goals.
About 90% of reviews praise the depth of analysis and commitment to clients, many noting hands on client support. Customers applaud the technical expertise, clear reporting, and smooth project management.
Firms needing detailed security evaluations pick this group. Analysts catch and fix complex holes fast.
How does REDTEAM. PL support cybersecurity efforts?
REDTEAM.PL tests client systems with deep vulnerability assessment and risk analysis. The team runs penetration testing and security audits to spot hidden flaws. They use a network scanner and an exploit framework to mimic hacker moves.
Clients praise their clear reports, fast incident response drills, and smooth client interaction.
Organizations gain solid risk management plans and security evaluation for apps and servers. Engineers use a packet sniffer and a proxy tool to track odd traffic. They map out gaps and set fix plans.
Their knack for finding hard threats helps teams lock doors fast.
What expertise does Foresite Cybersecurity bring?
Foresite Cybersecurity locks down data with strong encryption protocols and firewall setups. They blend data privacy, vulnerability assessment, and IT security to shield your systems.
Clients praise their data protection and IT security work, with 100 percent positive feedback on knowledge, speed, cost. Discussing risks feels like a chat over coffee, they keep talks simple and clear.
Reviewers note project leadership in 70 percent of comments and they love the customized security strategies. The crew uses a network scanner and SIEM platform to spot threats before they strike, like a guard dog barking at intruders.
Teams trust their proactive approach to risk management, so they sleep easier at night.
What services do Cyber Cops specialize in?
Cyber Cops locks down data and IT systems. They run threat assessment checks and use SIEM platforms, encryption tools, firewalls, and intrusion detection software. Experts scan networks with vulnerability scanners and watch for odd activity.
This quick work cuts risk and shields sensitive information.
Consultants craft customized risk management and compliance solutions for each client. Surveys show 100% of clients rate cost-effective plans and fast support. Teams shape incident response playbooks and run drills to test readiness.
Support covers 24-hour managed services and managed consulting, including data protection audits.
How does Rewterz contribute to cybersecurity?
Rewterz builds layers of protection around client networks using cybersecurity solutions. The firm runs risk assessments and vulnerability scans. It uses a security information and event management platform and a penetration testing toolkit.
Teams fix bugs fast and boost security posture across systems. They guard data and keep systems safe.
Clients praise the clear updates and quick fixes from the incident response team. The group adapts services to fit each client’s evolving needs. This flexibility fuels high client satisfaction and trust.
Rewterz plants security enhancement at every step.
What cybersecurity services does Link Group deliver?
Link Group builds cybersecurity plans for small businesses. They run vulnerability assessments to spot weak spots in networks and applications. The firm adds data protection routines and risk management controls to guard client data.
It layers threat detection tools like packet analyzers, firewalls, and intrusion detection systems. Then it drills incident response steps to boost operational resilience fast.
Clients praise the quick execution and thorough security service. This team crafts full security solutions for outfits with few internal staff. They adapt every step to match a firm’s size and budget.
All reviews cite solid gains in IT safety and safety records. It boosts small business security, time after time.
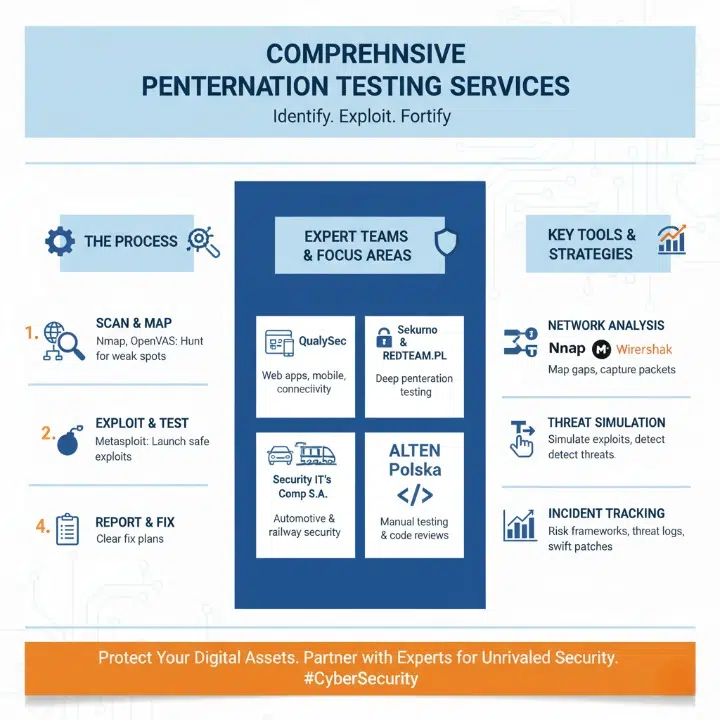
Comprehensive Penetration Testing Services
Experts use Nmap, a network mapper, and OpenVAS, a vulnerability auditor, to hunt for weak spots. Then they launch safe exploits with Metasploit, a pen-test toolkit, and hand over clear fix plans.
How do experts identify vulnerabilities in networks and applications?
Cyber teams scan code and systems for weak spots. They test defenses before attackers strike.
- QualySec runs vulnerability assessment scans on web applications, handheld devices, and connectivity points.
- Sekurno and REDTEAM.PL launch deep penetration testing attacks to unearth hidden flaws in complex environments.
- Security IT’s Comp S.A. tackles automotive and railway network security with security audits on control systems and data paths.
- ALTEN Polska delivers manual penetration testing and code reviews to spot system weakness across multiple platforms.
- Analysts deploy Nmap and Wireshark to map network security gaps and capture malicious packets in real time.
- Engineers leverage Metasploit and the Treatnet suite to simulate exploitation and detect emerging threats before they spread.
- Teams use risk management frameworks and threat detection logs to track incident patterns and guide swift patches.
Advanced Threat Detection Solutions
Zeek and Suricata scan network traffic, flag odd packets in seconds. Keep scrolling to peek under the hood of these tools in action.
What are the benefits of real-time monitoring and incident response?
NOPALCYBER scans every packet across data pipes, spotting odd spikes at zero hour. Its 24/7 monitoring services act like a guard dog that never blinks. Security IT (Comp S.A.) deploys its managed SOC center service with a three-hour critical time response SLA and wields the Threatnet suite, including Log Collector and Marker tools.
ALTEN Polska keeps its SOC as a Service eyes on logs and fires alerts at once. These platforms use realtime analytics to catch threats before they spread, feeding security operations teams with clear signals.
Teams jump on incidents, cutting dwell time to minutes. They mix threat detection with automated alerting to stop breaches fast. Staffers use advanced analytics to map attack patterns and fix holes on the go.
Clients praise the fast incident management, and NOPALCYBER logs 100% customer satisfaction. Firms curb risk, keep operations smooth, and tame digital chaos.
Data Protection and Compliance Services
They run GDPR audits, apply data encryption, roll out ISO 27001 controls, and manage security logs in a SIEM platform to guard data and meet rules, so read on to learn more.
How do firms ensure adherence to GDPR and other regulations?
CYBERSAFEHAVEN CONSULTING keeps data protection on track with regular audits and risk management reviews. It uses ISO 27001 checklists and GDPR guidelines to guard sensitive information.
ALTEN Polska runs gap assessments against NIST SP 800-218 and NIS2 standards. Security IT holds ABW and SKW certification for classified data and deploys CENTAUR PKI solutions.
Foresite Cybersecurity guides clients through secure development practices and privacy reviews. Rewterz improves cybersecurity with on-site audits and frank communication, meeting regulatory and client requirements.
Vulnerability scans and SIEM dashboards spot data breaches early, and GRC platforms track policy updates. Each SDL step and manual test forms a long term, proactive compliance plan.
Industrial Cybersecurity Expertise
Security teams lock down PLCs and SCADA platforms, so power grids and factories keep humming. They use anomaly detection, SIEM platforms, and intrusion detection tools to spot threats fast, and keep hackers on their toes.
How is operational technology and critical infrastructure protected?
ICSEC guards operational technology in factories, power plants, and transport hubs, delivering industrial cybersecurity at all layers. Comp S.A.’s successor, Security IT, traces back to thirty-five years in infrastructure protection and critical infrastructure defense, with more than five hundred experts on network security.
The Electronic Monitoring System watches sensors, raises alarms in seconds, and logs events for law enforcement teams. ALTEN Polska handles automotive cybersecurity management, carries out cybersecurity audits, and installs cybersecurity management systems for factories and assembly lines.
Engineers use the Treatnet suite to map network routes and trap malicious traffic with RouterMAP and Sinkhole tools. Outsourcing or turnkey projects fit different plant needs, and teams mix on-site support with remote monitoring.
Technicians test firewalls, scan SCADA networks, and check compliance standards against GDPR and safety management protocols. Operators get real-time threat management across devices, from programmable logic controllers to control servers.
Innovative Cyber Defense Strategies
It feels like guarding a castle from ghost knights. Teams use AI, machine learning, threat intelligence, SIEM platforms, and endpoint detection tools to lock down every gate.
How are AI and automation used for proactive security?
Teams at ALTEN Polska use AI for advanced threat detection and application testing. They add security testing to the Secure Software Development Lifecycle. This blend of testing and automation flags bugs and weak spots.
Engineers patch flaws before hackers spot them. The system learns from attacks and adapts fast.
Automation drives real time monitoring, incident response, and compliance tracking. ALTEN’s GRC solution collects logs, runs automated reporting, and feeds analytics dashboards. Security teams see odd moves at a glance.
They isolate threats within moments. This proactive cyber defense outpaces most attacks.
Security Operations Centers in Poland
Security Operations Centers in Poland, like those in Kraków and Katowice, run SIEM with Splunk and incident response workflows to spot threats fast and stop them in their tracks—read on to learn more.
Why are Kraków and Katowice important hubs for cybersecurity talent?
Poland named Kraków and Katowice as top cyber hubs by opening a Security Operations Center in the first and a Cyber Defense Center in the second. Teams scan logs on a live monitoring platform, spot odd signals, and sprint into action to stop intruders.
Local specialists serve both homegrown firms and clients overseas, using incident response playbooks and threat detection frameworks.
Both sites act as innovation workshops where experts tinker with new tools, tweak automation scripts, and roll out fresh shields. This hands-on lab work forges edge-cutting methods, pushing Poland into the lead as a regional cyber defense champ.
Takeaways
Ten firms stepped up to guard data and networks. Each runs security probing and weakness audits. Teams in Kraków and Katowice form strong SOC hubs. Log analyzers and intrusion sensors spot attacks fast.
Firms handle GDPR checks and shield privacy. Smart AI tools and automation routines block threats early. This lineup will keep digital assets safe.
FAQs
1. What do these cybersecurity firms in Poland do for the digital world?
They scan networks, block threats, and lock up data. They build strong shields around info. They watch logs day and night. They stand guard so you can rest easy.
2. How do they keep hackers at bay?
They use firewalls, test systems, and chase new risks. They update tools fast, train staff to spot odd moves. They hunt bugs like pros.
3. Why pick a Polish firm to guard your data?
Poland has sharp minds, they solve tough puzzles. They mix global know how with local speed. They work close, talk plain, nail down leaks quick.
4. How do I choose one of the ten top firms?
List your needs, set a budget, ask for demos. Check past wins, dig into case notes, talk to references. Chat with them, feel the vibe, pick the partner you trust.