Do you feel lost in a storm of cyber threats? Traditional firewalls and antivirus tools can lag behind new attacks. Endpoint security often misses sly phishing emails. Your team may work late, hunting alerts, but still miss key signs of a breach.
AI cuts false alerts in threat detection by up to ninety percent. This post shows 10 ways artificial intelligence and machine learning automate incident response, threat intelligence, malware analysis, phishing detection, endpoint security, and more.
Ready to learn more?
Key Takeaways
- IBM study: AI cuts false alerts by up to 90%. It lowers breach costs by $1.76 million (39.3%) and speeds containment by 108 days. The AI cybersecurity market rose from $14.9 billion in 2021 to a projected $133.8 billion by 2030.
- Security teams use bots and playbooks from tools like Secureframe Comply AI. These systems block malicious IPs, isolate devices, and guide real-time fixes. They save millions and cut downtime.
- AI-driven phishing detection uses neural networks and NLP to scan email content and URLs. It quarantines risky messages in minutes and retrains on new scams with live threat feeds.
- AI powers patch management and vulnerability scanning to plug holes that cause 47% of breaches. It ships patches in minutes and cuts manual work for the 56% of firms that still patch by hand.
- AI filters noise from 500–1,000+ daily security alerts. It flags true threats and cuts 40% false positives. IT teams free up over 20% of their work time for high-value tasks.
AI-Powered Threat Detection
AI systems sift through logs from security information and event management tools and intrusion detection systems. They spot odd patterns in network traffic and flag cyber threats.
They use machine learning models to detect anomalies and run root cause analysis in seconds. These systems act like guard dogs on the digital highway.
An IBM study shows that firms using AI paid $3.60 million per breach and cut costs by $1.76 million, or 39.3 percent. Full AI deployment shrinks containment time by 108 days. Even partial use saves $1.32 million, or 28.1 percent, on breach costs.
The AI in cybersecurity market grew from $14.9 billion in 2021 and may hit $133.8 billion by 2030. These smart tools boost endpoint security and data loss prevention.
Predictive Threat Intelligence
AI scans system logs, network flows, and user actions in real time. It uses predictive analytics and deep learning to spot threats early. Secureframe runs risk assessments, then gives fast advice to close security gaps.
Google Cloud’s AI Workbench uses Sec-PaLM to sort logs and warn of suspicious activity.
This setup feels like a radar for cyber attacks, it warns before data breaches. Teams use machine learning algorithms to map threat actor moves, they spot odd traffic spikes or failed logins.
Analysts act on those hints, they block attacks fast and trim incident response time. Foresight boosts endpoint security and helps IT teams breathe easier.
User and Entity Behavior Analytics (UEBA)
Splunk and IBM QRadar plug into SIEM and UEBA platforms. They learn normal patterns with anomaly detection models, then spot threat actors hiding in plain sight. The tech grabs a finance clerk straying off script faster than you can say “unauthorized download.” It halts data exfiltration before it hits the dark web.
Machine learning (ml) and network traffic analysis logs feed the system lots of data. AI builds a baseline of daily clicks, logins, file moves, and browser tabs. It flags odd spikes—maybe a dev pushing secret code or an admin testing stolen creds.
It fires off alerts to the SOC, so teams jump on threats with automated incident response. They cut dwell time, crush insider threats, and dodge data breaches.
AI-Driven Phishing Detection
AI sifts through inbox messages with the eagerness of a guard dog sniffing out threats. This system scans email content and URLs with neural networks trained on phishing samples. Engineers fed machine learning models real scam emails to sharpen pattern recognition.
Natural language processing breaks down text tone and structure, spotting sneaky tricks. Phishing detection runs around the clock, scoring each message on risk. Companies deploy email security gateways that feed AI algorithms fresh data every second.
Every flagged email triggers an alert, cutting response time from hours to minutes. IT teams smile as automatic quarantine blocks risky messages before users click. Organizations gain faster threat detection and response, reducing breach risk.
AI tools adapt when cyber criminals tweak their tricks, retraining models on new scam styles. This smart approach taps threat intelligence feeds to fuel anomaly detection. Users see fewer tricky emails, and security pros get breathing room for tougher tasks.
Behavioral Biometric Authentication
AI uses typing rhythms and mouse paths to check who uses an account. It tracks touch points on mobile devices and gait patterns with cameras. It spots odd actions and blocks fake logins.
This method cuts fraud and stops many data breaches. Many firms use machine learning and neural networks for this task. This step improves threat detection in real time.
Security teams gain strong endpoint protection. AI also edits security rules and runs policy checks on its own. It handles assessments and tweaks settings to meet regulatory compliance.
This cuts human error and boosts cybersecurity compliance. Systems monitor user and entity behavior analytics (UEBA) data for anomaly detection.
AI-Enhanced Endpoint Protection
Endpoint agents gather logs and network traffic. AI in cybersecurity consolidates this data into one view, automating encryption and patch deployment. AI algorithms rank vulnerabilities by risk.
This approach helps with proactive vulnerability scanning and patch management. It picks weak spots before hackers can strike.
Organizations save money by optimizing resources. Datto Endpoint Detection and Response and Datto Anti-Malware boost endpoint security. Teams spot malware, block malicious websites, and stop cyber-attacks on IoT devices.
Anomaly detection flags unusual logins and triggers incident response. Real-time threat detection cuts data breaches and thwarts fraudulent activities.
Automated Security Patching
Artificial intelligence (ai) drives patch management with a smart vulnerability scanner. The system runs vulnerability scanning to spot gaps in servers and apps. It then sends updates to endpoints for better endpoint security.
It plugs holes before hackers exploit them. Research shows 47% of breaches stem from unpatched vulnerabilities. A patch management system with machine learning cuts that risk.
More than half of organizations, 56%, still fix flaws by hand. They juggle tickets and delays. AI automates that workload. This process tests updates in a staging lab with network traffic analysis and intrusion detection systems.
It ships patches in minutes. Teams sleep easier, while systems stay secure.
Malware Analysis and Mitigation with AI
AI drives endpoint security and threat detection by scanning file behavior for odd code actions. The system marks both known malware and new zero-day threats. Then it applies behavioral analysis to system logs and network flows.
Sensors flag anomalies in real time and cut incident response delays. A next-gen shield like ShieldPlus AV lifts malware detection rates by 40%.
Hackers tweak code to slip past defenses like a fox. Security teams launch automated penetration testing with DeepProbe to find weak spots. AI links those findings into patch management and vulnerability scanning workflows.
This mix shrinks data breach risks by about 30% in live drills. Threat intelligence integration helps block future cyber threats fast.
Dynamic Deception Capabilities
ShadowPlex traps cyberthreats with fake nodes and keys. Machine learning watches network traffic analysis data and alerts teams fast. It spots odd behavior in user and entity actions.
Acalvio’s system shifts honeypots on the fly. Platforms mimic real endpoints to fool hackers and slow attacks. Tools link to intrusion detection systems, boost threat detection and shore up endpoint security.
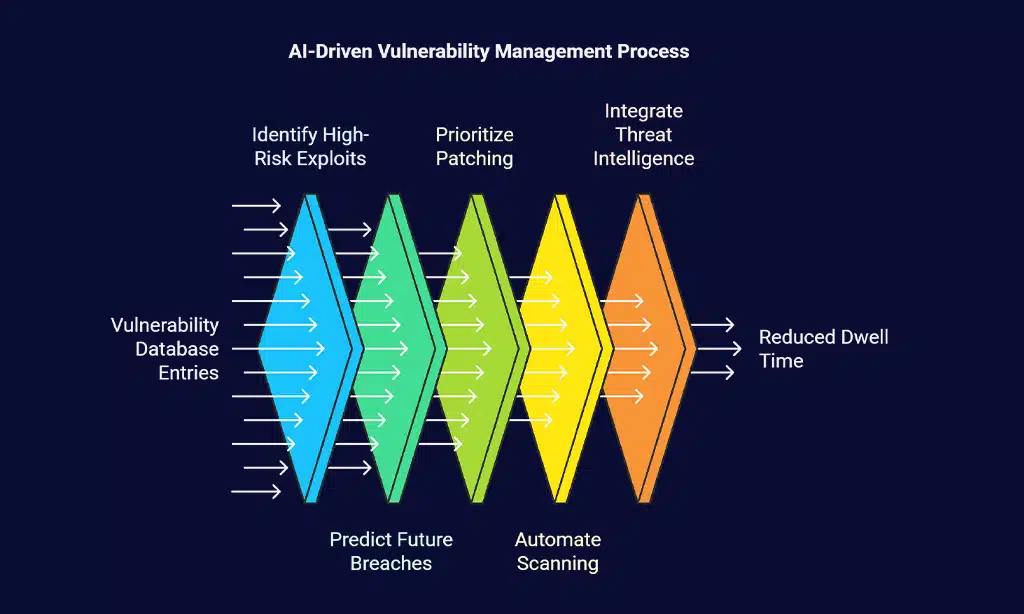
AI-Based Vulnerability Management
AI sifts through thousands of entries in the vulnerability database. It points out the exploits that hackers want most. Hackers chase the same holes. AI marks the holes that carry highest risk.
It predicts weeks ahead which bugs may spark data breaches. Teams see what to patch first. Patching cuts risk by a mile, since 47 percent of breaches stem from unpatched holes. A manual team slows down when they handle 100,000 assets.
Fifty-six percent of orgs use manual steps. That leaves a wide gap, a real target for cyber thieves.
Deep learning models drive new patch management. They run vulnerability scanning on servers, routers, endpoints, they send alerts in real time, they sort out dozens of flaws. A network mapper shows open ports, an open source scanner flags known bugs, an enterprise scanner rates each flaw.
AI algorithms link to threat intelligence feeds. They drop low risk items, use risk prioritization, flash red on critical bugs. This speeds up fixes. It cuts dwell time. Teams trade spreadsheets for dashboards.
They smile more, sweat less.
Real-Time Threat Intelligence Integration
Security teams feed live logs from firewalls and honeypots into a SIEM system. Google Cloud Security AI Workbench pairs with Sec-PaLM to process logs and autonomously integrate threat intelligence.
That engine analyzes sources to predict and prioritize threats, flagging suspicious IPs tied to ddos attacks and data breaches. VirusTotal Code Insight generates code summaries for quick malware detection.
Threat intelligence integration links live feeds and platforms. AI-driven algorithms adjust firewall rules on the fly and score alerts with predictive analytics for real-time threat detection.
That mix cuts false positives and speeds up response. Teams gain stronger network security and situational awareness.
Automated Penetration Testing
Automated penetration testing tools like DeepExploit run swift vulnerability scanning on servers and probe hidden entry points. NodeZero tests apps and servers, spotting weak spots fast.
Each tool learns from scan data, using neural networks.
AI automates risk assessments, generating insights and treatment plans in seconds. It watches network traffic for odd flows, spotting cyber threats and boosting network security. Teams cut tedious tasks and focus on critical fixes.
Reducing Stress on IT Teams with AI
AI tools like Secureframe Comply AI cut manual toil. They speed threat resolution and guide decision-making on network security. Staff in 59% of organizations handle over 500 cloud security alerts per day.
Another 38% see more than 1,000 alerts daily, often about anomaly detection or phishing detection. Workers mark 40% or more of these messages as false positives (43%) or low priority (49%), then waste over 20% of their day (56%) just reviewing them.
Teams miss 55% of critical alerts under such fatigue.
AI in cybersecurity filters noise and flags true cyber threats with real-time threat detection and incident response automation. It tackles endpoint security, vulnerability scanning, patch management, network traffic analysis, and compliance tasks fast.
Staff jump to high-value work like predictive analytics and fraud detection. Deep learning models, machine learning, and neural networks keep data exfiltration and DDOS attacks in check.
Morale climbs when mundane work shrinks.
Takeaways
Cybersecurity teams gain superpowers with smart defenses. Systems watch network traffic through intrusion detection systems. Machine learning spots odd patterns in data. Patch management tools fix gaps fast.
Endpoint detection solutions lock down vulnerable devices. Threat intelligence feeds track dark web chatter. Deep learning filters block savvy phishing attempts. Real-time analytics stop denial of service attacks before they hit.
Automated vulnerability scanning hunts for hidden flaws. Teams can rest easy as AI guards their networks and data.
FAQs
1. What is real-time threat detection in AI cybersecurity?
Real-time threat detection uses AI to run network traffic analysis and spot phishing and detect malware in a snap. It acts like a guard dog on the internet.
2. How does AI boost endpoint security?
AI in cybersecurity watches each device for odd moves, using behavioral analysis and neural networks. It catches insider threats and malicious software before they roam free.
3. Can generative AI help with phishing detection?
Yes, generative AI crafts fake scams to train teams and then hunts phishing on the internet. It taps threat intelligence integration and machine learning for fraud detection.
4. How does AI speed up incident response?
AI technologies use predictive analytics and user and entity behavior analytics to flag anomaly detection. They add dark web monitoring and intrusion detection systems, then guide your team to act fast.
5. Will AI handle vulnerability scanning and patch management?
It will. AI runs vulnerability scanning and checks network traffic analysis for weak spots. Then it suggests patch management steps to cut data breaches and cyber intrusion risk.
6. How does AI help with compliance and training?
AI builds cybersecurity training from DDoS attacks and data exfiltration cases. It logs each move for regulatory compliance and data loss prevention (DLP), keeping teams sharp and ready.