For any website owner, experiencing a hack is a terrifying experience. One moment, your site is working fine; the next, it’s showing strange pop-ups or redirecting visitors to shady pages. Hackers can exploit weak passwords, outdated plugins, or hidden vulnerabilities to take control of your site without warning.
A hacked website doesn’t just hurt your business—it damages trust. Search engines might blocklist you, making it harder for users to find you online. The good news? You can fix this mess with the right steps and tools.
In this guide, you’ll discover how to recover quickly and secure your site against future attacks.
Ready to reclaim control? Keep reading!
Recognizing Signs of a Website Hack
Your website might act strange, like a car making odd noises before breaking down. Strange pop-ups or content changes could mean trouble is brewing.
Unanticipated Redirects or Pop-Ups
Strange browser redirects can signal a hacked website. These may redirect users to shady sites or show offensive content. Unwanted pop-ups might appear, sometimes mimicking antivirus warnings.
Hackers often use these tricks to spread malware or steal data.
Unusual patterns in network traffic often follow such attacks. Pay attention to suspicious spikes in activity. Hosts might also install rogue software without permission, worsening the issue.
Regular malware scans and checking server logs help catch these dangers early.
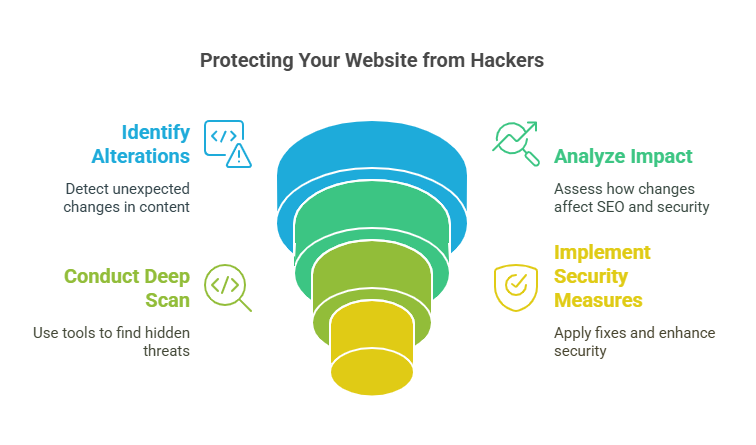
Alterations to Website Content
Hackers often inject spam pages or unwanted ads into your site. These changes can impact your search engine rankings and harm website security. Altered content might include fake product listings, phishing links, or redirects to malicious websites.
Google may flag such modifications with warnings in the search results. Pay attention to updates that seem out of place or unauthorized edits on key sections like the homepage. A malware scanner can detect hidden threats or code injection altering important files.
Conducting a deep scan helps catch all harmful changes quickly, protecting your hosting account from further risks.
Search Engine Blacklisting
A hacked website can get blocklisted by search engines like Google. This happens when they detect malware, spammy links, or harmful content on your site. Your site might stop showing up in search results, and visitors may see browser warnings like “Deceptive Site Ahead.” These alerts drive users away and hurt traffic.
Spam links cause big issues too. Search engine algorithms treat them as security threats. If left unchecked, this lowers rankings and damages trust with users. To fix it, remove bad code and submit a Google Review Request through the search console for reevaluation quickly.
Actions to Take Immediately After a Hack Detection
Act fast to protect your website and data. These first steps are critical for limiting the damage and starting recovery.
Notify Your Hosting Provider
Contact your hosting provider right away. They may have tools to identify security flaws or malware in your hosting account. Most hosting companies can guide you through website recovery and offer malware scanning services.
Hosting providers often keep backups. These backups also help restore data after a breach. Informing them ensures they monitor the issue closely, preventing further damage caused by unauthorized access or viruses.
Temporarily Disable the Website
Take your website offline to stop further damage. Hackers might steal sensitive data or inject more malicious codes if the site remains active. Display a maintenance message while investigating, so visitors know it’s temporary.
This step also gives you time to assess the hack’s impact without risking access by attackers.
You can suspend your hosting account through your hosting provider’s control panel. Another option is setting up an “Under Maintenance” page via updated DNS entries or HTTP headers.
Blocking unauthorized access protects users and keeps search engines from flagging it on spam blocklists.
Alert Users and Stakeholders
Inform users about the security breach quickly. Share clear steps to secure their accounts, like changing passwords and checking for unauthorized access. Use empathy while communicating—show you care about their data.
Notify stakeholders, including your hosting company and partners, right away. Explain potential impacts on business operations or website functionality. Transparency builds trust during a crisis like this.
10 Essential Steps to Recover a Hacked Website
Fixing a hacked website requires patience, smart tools, and quick actions—read on for steps to take control.
Backup the Compromised Website
Access your hosting account and open the File Manager. Enable “SHOW HIDDEN FILES (DOTFILES)” to see all files, including system ones. Select every file on your website, then compress them into a single ZIP archive.
Don’t skip any files—they may hold critical information for recovery later.
Store this backup securely on an external drive or cloud service. This step locks in what you’ve got before making changes or removing malware. Regular backups can save headaches if future security vulnerabilities arise again!
Update Passwords and Review User Permissions
Change passwords for all user accounts immediately. Use a strong password generator to create new, secure ones. Weak passwords are easy targets for hackers and can lead to repeated breaches.
After resetting, enable two-factor authentication on all accounts for added security.
Review permissions tied to each account. Limit access only to what is necessary—no more, no less. Check if unauthorized access occurred through shared hosting or outdated credentials.
Remove any unrecognized users from the system without delay. Regularly auditing these settings helps prevent future issues and cyber threats like ransomware or phishing attacks.
Restore from a Secure Backup
Use a backup created before the website was hacked. Verify it contains no malicious code or errors. Check its integrity on a secure device to avoid adding back any security issues.
Always use clean, reliable backups from trusted storage locations.
Regular testing of backup files ensures they work correctly during a crisis. Schedule backups often to keep data safe and minimize loss during cyber attacks or breaches. Consider automatic tools for better website recovery planning.
Conduct a Malware and Malicious Code Scan
Scan your site for malware and malicious code using trusted tools like Malwarebytes or Microsoft Defender. Check all files, including backups, before restoration. Malicious scripts often hide in plugins, themes, or custom code.
A vulnerability scanner can help identify software vulnerabilities exploited by hackers.
Focus on removing any backdoors that grant unauthorized access. Hackers may plant hidden codes to regain control later. Antivirus software can detect these threats and secure the system effectively.
Always repeat scans after cleanup to confirm no traces remain.
Eliminate Backdoors and Security Weaknesses
Backdoors give hackers secret ways into your site. Use a vulnerability scanner to spot hidden problems. Delete any malicious code or files found on the server. Check access logs for unexpected login attempts or changes that look suspicious.
Strengthen security by changing all weak passwords to stronger ones using a password generator.
Old software is risky and can create openings for attacks. Update plugins, themes, and core software immediately after cleaning up the site. Install a web application firewall (WAF) to block cyberthreats before they reach your system.
Scan .htaccess and critical files for tampering, then reset them if needed to remove unauthorized changes fully.
Upgrade All Plugins, Themes, and Core Software
Outdated plugins and themes are like open doors for hackers. Update them immediately to close these gaps. Use the latest versions of your platform, whether WordPress or another CMS.
Old software often contains security vulnerabilities hackers exploit.
Enable automatic updates if possible. It saves time and keeps things secure without manual checks. Remove unused files, outdated plugins, and inactive themes too—they’re dead weight with hidden risks.
Regular maintenance helps stop unauthorized access before it starts!
Reset the .htaccess File
Check the .htaccess file for unauthorized changes. Hackers often modify it to redirect users or hide their malicious code. Rename the current file to “.htaccess_old” and create a new one.
Use default settings from your hosting provider, or rebuild it based on secure configurations.
Add security rules to block suspicious IPs and restrict access to sensitive directories. Update this file regularly to patch any vulnerabilities. Always back up before making changes in case you need to troubleshoot later.
Check for Blacklisting and Request Removal
Blacklists can hurt traffic and trust. Use tools like Google Search Console or online blacklist checkers to see if your site is flagged. Look for warnings in browser messages, such as “Deceptive Site Ahead.” These alerts often mean blacklisting by Google Safe Browsing or other services.
Submit a removal request after cleaning the site. Reach out to Google using their search console for review and re-indexing. Also, contact any other blacklist providers directly for delisting.
After approval, monitor your website to ensure smooth functionality without any warnings.
Engage Google for Site Review and Re-indexing
Use Google Search Console to verify website ownership. Then, submit a reindexing request for the hacked pages. Adding an updated sitemap helps Googlebots crawl your site faster. If past issues raised browser warnings, this step clears them up.
Confirm that all malicious code is gone before asking for review. Google Safe Browsing tools can check if blacklisting persists. Once resolved, your recovery strengthens search visibility and builds user trust again.
Enhance Security Protocols
Strengthen website security by using tools like DDoS protection and web application firewalls. These block harmful traffic, stopping cyber criminals in their tracks. Encrypt sensitive data to safeguard against breaches.
Regularly perform security audits to spot vulnerabilities early.
Train employees on cybersecurity best practices to minimize risks from phishing or malware attacks. Use strong passwords with a password generator, and change them often. Enable two-factor authentication for all user accounts—it’s like adding an extra lock to your door! Keep plugins, themes, and software updated to close any loopholes hackers might exploit.
Preventing Future Website Hacks
Hackers don’t sleep, so your website security shouldn’t either. Take proactive steps now, or risk another break-in later.
Conduct Regular Security Audits
Security audits help uncover hidden vulnerabilities. They catch weak passwords, outdated software, and malicious code early. Scan your website regularly with a vulnerability scanner.
Review server logs for failed login attempts or unauthorized access points. Fix security issues immediately to prevent data breaches.
Check plugins, themes, and DNS entries during each audit. Identify outdated components and update them promptly. Analyze error logs to spot recurring problems. Use tools like Google Search Console or antivirus programs to flag risks fast.
Regular reviews keep your hosting account protected from cybercrime threats like phishing attacks or spam emails sneaking in unnoticed.
Implement Advanced Monitoring Solutions
Track website traffic with advanced monitoring tools. Use real-time alerts for failed login attempts or unexplained spikes in activity. Set up daily malware detection scans to spot malicious code early.
Keep detailed server logs and access logs to review any suspicious behavior. These steps help catch unauthorized access before bigger issues arise.
Install a vulnerability scanner to find security problems quickly. Tools like Google Search Console can warn about errors or blacklisting issues fast. Regularly check DNS entries and monitor changes closely.
By staying one step ahead, you reduce risks of future hacks while creating a safer site environment for your users.
Train Your Team in Cybersecurity Best Practices
Staff often overlook small habits that lead to big security breaches. Teach your team how weak passwords or clicking shady email links can invite danger. Use tools like “Have I Been Pwned” to show real risks of leaked data.
Share stories of cyber crimes caused by simple human errors, such as falling for a phishing scam.
Run regular training sessions on spotting redirection attacks and fake login pages. Explain terms like social engineering in simple words, breaking down tactics hackers use. Offer password generators or two-factor authentication tips to secure accounts.
Foster cybersecurity awareness with frequent updates on current threats, ensuring employees stay sharp against tricks like cracking and spam traps in emails.
Takeaways
Recovering a hacked website is a challenging process. It requires immediate action, keen attention, and proper planning for the future. To discuss this matter further, cybersecurity specialist Emily Carter provides her insights.
Emily has over 15 years of experience in IT security. She holds a master’s degree in cybersecurity from MIT and is an expert in website recovery and defense strategies. Her collaborations with Fortune 500 companies establish her expertise in preventing online threats.
Emily emphasizes addressing core vulnerabilities such as weak passwords or outdated plugins. Each recommended action is integral—like assembling puzzle pieces—to secure and restore your site effectively.
Backups are essential when attacks occur, malware scans detect potential risks, and blacklisting checks help rebuild trust with search engines.
She highlights the importance of prioritizing the protection of sensitive data immediately after a breach. Ethical responsibility includes promptly informing users of any exposure to their information and taking swift corrective action—not ignoring the issue.
Emily recommends incorporating these steps into everyday practice: leverage strong password generators, consistently update plugins, and frequently conduct vulnerability scans using tools like Google Search Console or server logs monitoring systems.
A proactive approach is far more effective than a reactive one in mitigating risks!
While the guidance provided is practical and manageable for website administrators, consistent effort upfront is necessary. Delaying action increases risks, potentially leading to even more severe consequences.
It’s better to take steps now to avoid escalating problems that could worsen over time.
FAQs on Essential Steps To Recover A Hacked Website
1. How do I start recovering a hacked website?
Start by contacting your hosting provider. They can help identify the issue and provide guidance on next steps, like analyzing server logs or restoring a website backup.
2. What should I check for after a security breach?
Look for malicious code, unauthorized access, failed login attempts, and changes to DNS entries or user accounts. Review error logs and access logs for suspicious activity.
3. How can weak passwords lead to hacking?
Weak passwords are easy targets for phishers and crawlers. Use a password generator to create strong ones and update all credentials immediately after an attack.
4. Should I use tools like Google Search Console during recovery?
Yes! Google Search Console helps detect security vulnerabilities, browser warnings, or issues flagged in Google Safe Browsing that may have blacklisted your site.
5. Can software updates prevent future attacks?
Absolutely! Outdated systems often contain security vulnerabilities hackers exploit. Regular software updates improve IT security and reduce risks from cyber threats.