In what is being described as the largest cryptocurrency theft in history, Dubai-based crypto exchange Bybit fell victim to a devastating hack on February 21, 2025, resulting in the theft of approximately $1.5 billion (€1.4 billion) worth of Ethereum (ETH).
The attack, which was executed during a routine transfer of assets between Bybit’s cold (offline) wallet and hot (online) wallet, exposed the vulnerabilities of even the most well-established crypto exchanges. Cold wallets are typically used for long-term storage as they remain disconnected from the internet, while hot wallets facilitate everyday transactions but are more susceptible to hacking attempts.
Shortly after the breach, the stolen Ethereum was transferred to an unknown address, triggering an immediate response from Bybit’s security team. The exchange moved quickly to lock down its systems, secure remaining funds, and collaborate with cybersecurity experts to track down the stolen assets.
Despite the severity of the attack, Bybit assured its users that their funds were safe and that it was financially strong enough to cover all liabilities.
How the Attack Happened: Vulnerability in Wallet Transfers
Bybit’s official statement revealed that the hack occurred during the transfer of assets from a cold wallet to a hot wallet, a process that requires multiple security measures, including multi-signature authentication and advanced encryption.
Cybersecurity analysts suggest that hackers may have exploited an internal vulnerability in Bybit’s wallet infrastructure or gained unauthorized access through social engineering tactics—a common technique where attackers manipulate employees into revealing sensitive information.
Unlike past hacks that exploited flaws in smart contracts or DeFi platforms, this attack targeted Bybit’s centralized infrastructure, emphasizing the growing risks for major exchanges handling large sums of crypto assets.
Bybit’s Immediate Response and Damage Control
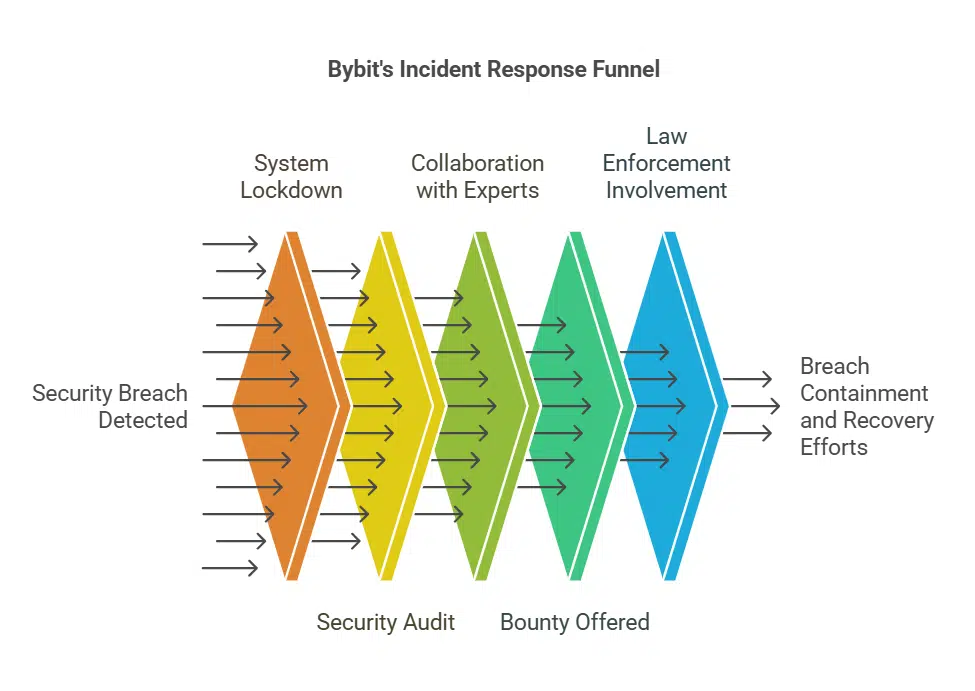
The moment the breach was detected, Bybit took a series of emergency steps to contain the situation and prevent further losses:
- System Lockdown: Bybit immediately suspended withdrawals and isolated the compromised wallet from its network.
- Security Audit: The company conducted an in-depth security audit to identify how the hacker gained access.
- Collaboration with Industry Experts: Bybit partnered with leading blockchain analytics firms to trace the stolen assets and prevent their laundering.
- 10% Bounty Reward: The exchange offered a bounty of 10% (up to $140 million) to cybersecurity experts and ethical hackers who could help recover the stolen funds.
- Working with Law Enforcement: Bybit contacted international regulatory bodies and cybercrime agencies to investigate the breach and track down the perpetrators.
Despite the alarming scale of the attack, Bybit reassured its users that their assets were fully backed and that withdrawals for unaffected accounts remained operational.
A Remarkable Recovery: How Bybit Closed the $1.5 Billion Gap in Just 72 Hours
While many crypto platforms have struggled for months (or even years) to recover from major security breaches, Bybit managed to close the financial gap in under three days.
The rapid recovery was made possible due to an unprecedented industry-wide effort, with multiple players stepping in to help:
- $42.89 million (€41 million) in suspicious transactions were frozen by various crypto exchanges and brokerage platforms.
- Bybit secured 446,870 Ethereum (€1.17 billion) through loans, whale deposits, and currency purchases, stabilizing its reserves and restoring lost assets.
- Crypto tracking firms such as Lookonchain and Elliptic provided crucial insights into the movement of stolen funds, helping to block further transactions.
- Several major crypto exchanges, including Binance and OKX, assisted in monitoring suspicious transactions related to the stolen funds.
The rapid action and cross-platform cooperation demonstrated a new level of resilience within the cryptocurrency industry.
Who’s Behind the Attack? North Korea’s Lazarus Group Suspected
Investigations by Elliptic, a well-known blockchain research firm, suggest that North Korea’s Lazarus Group may be responsible for the attack.
The Lazarus Group has been linked to multiple high-profile crypto thefts in the past, including the $625 million Ronin Network hack (Axie Infinity) in 2022 and several attacks on DeFi platforms in 2023 and 2024.
According to Elliptic’s report:
- Minutes after the Bybit hack, the stolen tokens were converted into Ethereum—a signature move by the Lazarus Group.
- The stolen Ethereum was then dispersed into over 50 different crypto wallets in an attempt to obscure the trail.
- As of February 24, 14.5% of the stolen assets (worth $195 million/€187 million) had already been withdrawn through layered transactions.
Laundering Process: The Lazarus Group is known for its complex laundering tactics, including:
- Token Swapping: Converting stolen assets into another cryptocurrency (such as Ether) to erase transaction histories.
- Mixing Services: Using platforms like Tornado Cash to further obfuscate the origin of funds.
- Layering Transactions: Moving crypto across multiple wallets to make it harder for investigators to trace.
- Converting to Fiat Currency: Eventually liquidating the stolen assets into real-world currencies through underground markets.
Given its history of cyberattacks, the Lazarus Group remains a top suspect, though investigations are ongoing.
The Bigger Picture: Crypto Security Threats Continue to Rise
The Bybit heist is the latest in a growing trend of crypto security breaches. According to data from Reuters, over $2 billion (€1.9 billion) worth of crypto has been stolen in 2024 alone.
Some of the biggest hacks in recent years include:
- Poly Network (2021): $611 million stolen (later mostly returned).
- FTX Collapse (2022): $477 million lost in a suspected insider hack.
- Ronin Network (2022): $625 million stolen by North Korean hackers.
- Mango Markets (2022): $114 million stolen via a flash loan attack.
Lessons for the Crypto Industry
The Bybit hack serves as a wake-up call for crypto exchanges worldwide. Security experts are urging stronger preventive measures, including:
- Enhanced Wallet Security: Exchanges should increase multi-signature authentication and air-gapped cold storage protection.
- AI-Powered Fraud Detection: Implementing machine learning models to detect suspicious transactions in real time.
- More Stringent User Verification: Strengthening KYC (Know Your Customer) and AML (Anti-Money Laundering) processes.
- Industry-Wide Collaboration: Increased cooperation between crypto exchanges, regulators, and blockchain analytics firms to combat financial crime.
What’s Next for Bybit?
Despite the unprecedented attack, Bybit’s resilience and quick recovery have reassured its users and the crypto industry at large.
Bybit has stated that it will be implementing new security protocols and working on more advanced risk management systems to prevent future breaches.
While the investigation is still ongoing, the crypto community’s collective response to the Bybit hack highlights the importance of unity in tackling cyber threats.
As the digital asset space continues to evolve, security will remain a top priority for exchanges and investors alike.